Fraud Management & Cybercrime , Ransomware
Conti Ransomware Targets Costa Rican Government Entities
After Demand of $10 Million Ransom Is Not Met, Conti Begins Leaking Data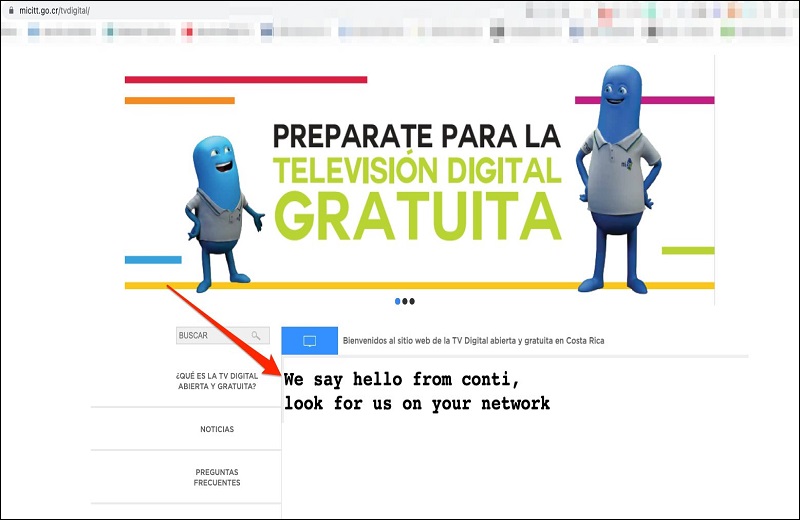
The Conti ransomware group, which declared support for Russia’s invasion of Ukraine, has subsequently been highly active in targeting the U.S. and its NATO allies. But in the latest attack spree recorded on a single nation, Conti has reportedly targeted at least five Costa Rican government agencies.
See Also: Defending Governments from Ransomware: Modernizing Malware Security with Cloud Sandboxing
The targeted agencies include the Ministry of Finance - or Ministerio de Hacienda; the Ministry of Science, Innovation, Technology and Telecommunications - or MICITT; the Instituto Meteorológico Nacional - or IMN; the Radiográfica Costarricense - or RACSA; and a Caja Costarricense de Seguro Social - or CCSS - portal. Paola Vega Castillo, the head of MICITT, confirmed this list in a press conference held in Costa Rica on Wednesday.
According to Castillo, in the case of MICITT, only "modification of the contents of the web page" was carried out and no evidence of information being extracted was found. But in case of the IMN and RACSA a "process of extracting email archives" was detected, and the CCSS confirmed that its human resources portal had been targeted, she says.
QCostaRica, a local media agency, cited Minister of the Presidency Geannina Dinarte Romero, who also confirmed this report but ruled out any chances of a ransom payment to the Conti group.
Conti had demanded a $10 million ransom from the Costa Rican government, but since no negotiations were initiated, the group has now begun to leak data it exfiltrated during the attack, according to its dark web site.
The Biggest Victim
The first and probably the largest agency affected is Costa Rica's Ministry of Finance, based on the amount of data exfiltrated, according to Conti's post.
#Conti's latest update on the cyberattack against Costa Rica's Ministerio de Hacienda
— BetterCyber (@_bettercyber_) April 20, 2022
"If the ministry cannot explain to its tax payers what is going on, we will do it 1) we have penetrated their critical infrastructure, gained access to about 800 servers, ..."pic.twitter.com/wp2Y8UeGGN
In the post published by the ransomware group on its name and shame website "Conti News," the group says that it has gained access to about 800 servers from which nearly 1TB worth of data has been exfiltrated, including 900GB of Tax Administration Portal - or ATV - databases, in the MSSQL mdf format, and 100GB of internal documents containing full names and email addresses of those in the Ministry of Finance.
On Wednesday, the Conti group added an update to the same post, stating it had access to two other email server files of two more Costa Rican entities. The group also claimed to have implemented a large number of backdoors in various public ministries and private companies and pledged to continue to attack the ministries of Costa Rica until its government paid them, according to the update.
In the late hours of Wednesday, Conti News added four compressed files with information supposedly extracted from the victim's systems that includes more than 10GB of information available for download.
The Ministry's Response
The Ministry of Finance said in an extensive Twitter thread that in the early hours of Monday, April 18, it began to have problems in some of its servers and that since then, it has been investigating and analyzing in depth what had happened. Meanwhile, it temporarily suspended the ATV and TICA - Tax and Customs - platforms and said they will be available again after the analysis is completed.
The data exposed/leaked by the attackers corresponds to the General Directorate of Customs and is used as input and support, but it is not of any historical nature, the ministry says in the Twitter thread.
After the initial announcement by Conti and the subsequent confirmation by the ministry about the incident, the group targeted the site of the Ministry of Science and Technology to publish a message that says: "We say hello from Conti, look for us within your network."
At the time of this writing, Information Security Media Group found all the targeted websites still down and based on the Twitter posts of the Ministry of Finance, it appears that even the ATV and TICA portals are offline as their IT teams are trying to resolve the issue along with the help of external stakeholders.
"So far, Spain, the United States, Israel, Microsoft and GBM, the leading IT services company in Central America and the Caribbean, have offered their help to the country to regain control of Treasury platforms," Dinarte Romero said in her press conference.
Latest Victims
The Conti group has already claimed access to an extensive government network through backdoors it says it placed in them. It also says that it will not stop its operations until the ransom is paid, and today the group added another two government entities - the Social Development Fund and Family Allowances, or Fondo de Desarrollo Social y Asignaciones Familiares or FODESAF, and the Ministry of Labor and Social Security, or Ministerio de Trabajo y Seguridad Social or MTSS - to the already-long list of targeted Costa Rican government entities.
#Conti continues the cyberattack against Costa Rica, allegedly compromising the Fondo de Desarrollo Social y Asignaciones Familiares (FODESAF) and Ministerio de Trabajo y Seguridad Social (MTSS)...#Ransomware #RansomwareGroup pic.twitter.com/pmbQIog12I
— BetterCyber (@_bettercyber_) April 21, 2022
At the time of writing, the two websites, fodesaf.go.cr and mtss.go.cr, which appear to be subdomains of the main government website, were still online and did not display any messages from Conti group, as was seen in the case of the MICITT website.
The group has also published more data - approximately 24GB - allegedly belonging to the Costa Rican Ministry of Finance, according to an updated post on Conti's dark web site Conti News. This takes the total published data count to six files containing 39.77GB of data.
Jorge Mora, director of digital governance at MICITT, said in a press conference Wednesday that apart from the analysis of the current situation, prevention processes and mitigation measures are being developed., and alerts are being issued to other institutions so that they are further prepared for such events,.
"We are in the process of identifying risks in other institutions so that the teams can attend to them in a preventive manner," Mora said.
Conti Turns to Linux-Based VMs
As Costa Rica reels from Conti's repeated breaches, the group also seems to be sharpening its skills, according to research from Trellix that says the Russian ransomware group has now turned its attention to ESXi Hypervisors with its Linux-based variant.
"On April 4, 2022, we detected a sample uploaded, which triggered our threat-hunting rules. Upon further investigation, we determined the file is a Conti variant compiled for the Linux operating system targeting ESXi servers. Although the ESXi version of Conti is not new and has already been discussed, this is the first public sample we have seen in the wild," the researchers say.
Following the leak of several years' worth of internal messages and Conti's playbook in 2021, the researchers at Trellix have provided a technical analysis of the recently detected Linux variant of Conti ransomware, in a technical blog.