Few Fortune 100 Firms List Security Pros in Their Executive Ranks
Krebs on Security
JULY 21, 2023
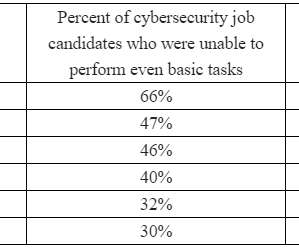
But one aspect of that vaunted list that hasn’t shifted much since is that very few of these companies list any security professionals within their top executive ranks. For example, 88 percent listed a Director of Human Resources (or “Chief People Officer”), and 37 out of 100 included a Chief Marketing Officer.

















































Let's personalize your content