Ransomware Group Turns to Facebook Ads
Krebs on Security
NOVEMBER 10, 2020
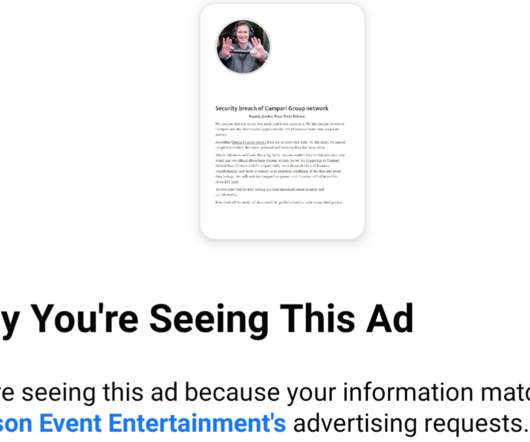
Now, one crime group has started using hacked Facebook accounts to run ads publicly pressuring their ransomware victims into paying up. The ad was designed to turn the screws to the Italian beverage vendor Campari Group , which acknowledged on Nov. Of course, it didn’t cost the ransomware group anything. EST today (Nov.







































Let's personalize your content