Will generative AI make the digital twin promise real in the energy and utilities industry?
IBM Big Data Hub
AUGUST 22, 2023
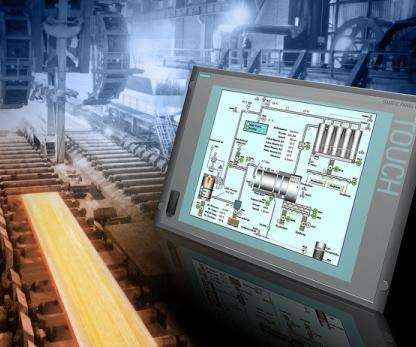
Generative AI and digital twin use cases in asset-intensive industries Various use cases come into reality when you leverage generative AI for digital twin technologies in an asset-intensive industry such as energy and utilities. A digital twin is the digital representation of a physical asset. Asset performance management.











































Let's personalize your content