Sugar Ransomware, a new RaaS in the threat landscape
Security Affairs
FEBRUARY 2, 2022
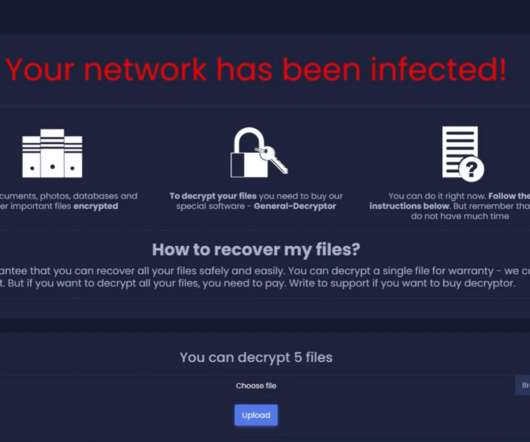
Cyber security team at retail giant Walmart dissected a new ransomware family dubbed Sugar, which implements a ransomware-as-a-service model. The cyber threat team at retail giant Walmart has analyzed a new ransomware family dubbed Sugar, which is offered through a ransomware-as-a-service (RaaS) model. Pierluigi Paganini.




















Let's personalize your content