How to Use Signal Encrypted Messaging
WIRED Threat Level
AUGUST 18, 2022
The best end-to-end encrypted messaging app has a host of security features. Here are the ones you should care about.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

WIRED Threat Level
AUGUST 18, 2022
The best end-to-end encrypted messaging app has a host of security features. Here are the ones you should care about.

The Last Watchdog
MAY 19, 2022
Security is essential for a CMS. Security is also necessary if your retrieval system (such as a website or mobile app) has a paywall or is restricted to only a subset of people, such as customers or resellers. Best security practices. percent of CMS users worry about the security of their CMS—while 46.4
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
OCTOBER 18, 2022
A bug in the message encryption mechanism used by Microsoft in Office 365 can allow to access the contents of the messages. Researchers at the cybersecurity firm WithSecure discovered a bug in the message encryption mechanism used by Microsoft in Office 365 that can allow to access message contents due. ” concludes WithSecure.

Thales Cloud Protection & Licensing
NOVEMBER 2, 2021
Quantum Resistant Encryption – Are You Ready? Over the past few months, a handful of Thales CPL clients have mentioned their concern regarding the future threat of quantum computing to their data security frameworks. With the emergence of quantum risk to cipher-security, we will no doubt emerge more resilient out the other end.

IBM Big Data Hub
JANUARY 22, 2024
Notify the security team Once you’ve disconnected the affected systems, notify your IT security team of the attack. Hackers know this might be your first instinct, and some types of ransomware notice restart attempts and cause additional harm, like damaging Windows or deleting encrypted files.

Thales Cloud Protection & Licensing
FEBRUARY 9, 2018
With organizations around the world now deploying ever-increasing amounts of encryption solutions in an effort to ward off cybercrime, businesses are facing a combination of challenges. Protecting data through encryption. Using algorithms to encode data as ciphertext, encryption acts as a safety blanket for data.

Krebs on Security
NOVEMBER 23, 2018
So here’s a quick refresher course on how to make it through the next few weeks without getting snookered online. USE A CREDIT CARD: It’s nearly impossible for consumers to tell how secure a main street or online merchant is, and safety seals or attestations that something is “hacker safe” are a guarantee of nothing.

eSecurity Planet
OCTOBER 18, 2022
However, even with the best planning, organizations can find a few users, machines, or systems that were overlooked or whose backup may be corrupted or encrypted. Also read: Best Backup Solutions for Ransomware Protection How One Company Survived a Ransomware Attack Without Paying the Ransom. How Does Ransomware Encryption Work?
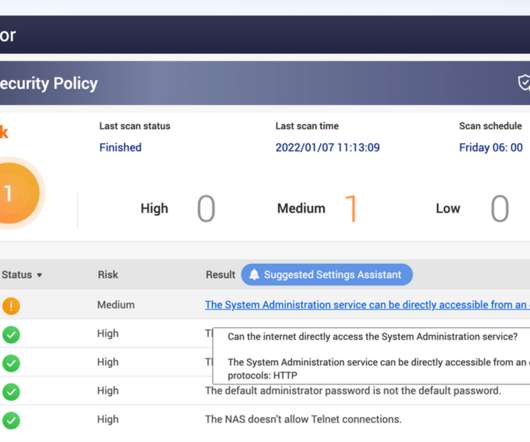
Security Affairs
JANUARY 7, 2022
Taiwanese vendor QNAP has warned customers to secure network-attached storage (NAS) exposed online from ransomware and brute-force attacks. QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP networking devices.” The post How to secure QNAP NAS devices?

IT Governance
APRIL 5, 2023
Malware is one of the most common cyber security threats that organisations and individuals face. It can do this in a number of ways, such as: Stealing, encrypting or deleting sensitive information; Hijacking or altering core system functions; Monitoring user activity; and Spamming the device with adverts. What is malware?

Security Affairs
MARCH 26, 2019
Good news for the victims of the Hacked Ransomware, the security firm Emsisoft has released a free decryptor to decrypt the data of infected computers. Security experts at Emsisoft released a free decryptor for the Hacked Ransomware. Well, experts an Emsisoft also released a free decryptor tool for this threat. Pierluigi Paganini.

Thales Cloud Protection & Licensing
FEBRUARY 20, 2024
How to protect your machinelearning Models richard-r.stew… Tue, 02/20/2024 - 21:50 Dr. Werner Dondl and Michael Zunke In computer technology, few fields have garnered as much attention as artificial intelligence ( [KD1] [RJ2] AI) and machine learning (ML). An encrypted model is basically useless without the correct decryption key.

Thales Cloud Protection & Licensing
FEBRUARY 20, 2024
How to protect your machinelearning Models richard-r.stew… Tue, 02/20/2024 - 21:50 Dr. Werner Dondl and Michael Zunke In computer technology, few fields have garnered as much attention as artificial intelligence ( [KD1] [RJ2] AI) and machine learning (ML). An encrypted model is basically useless without the correct decryption key.

The Last Watchdog
MAY 3, 2021
Encryption agility is going to be essential as we move forward with digital transformation. All of the technical innovation cybersecurity vendors are churning out to deal with ever-expanding cyber risks, at the end of the day, come down to protecting encrypted data. Refer: The vital role of basic research.

Thales Cloud Protection & Licensing
FEBRUARY 14, 2024
How to Protect Your Machine Learning Models madhav Thu, 02/15/2024 - 07:20 Contributors: Dr. Werner Dondl and Michael Zunke Introduction In computer technology, few fields have garnered as much attention as artificial intelligence ( AI) and machine learning (ML). An encrypted model is basically useless without the correct decryption key.

Dark Reading
NOVEMBER 3, 2021
Experts weigh in on steps network and security administrators need to take before the next time a root certificate expires.

The Security Ledger
JANUARY 14, 2022
The post Spotlight: ShardSecure on Protecting Data At Rest Without Encryption appeared first on The Security Ledger with Paul F. Related Stories Episode 230: Are Vaccine Passports Cyber Secure? Spotlight: COVID Broke Security. As always, you can check our full conversation in our latest Security Ledger podcast at Blubrry.

IT Governance
SEPTEMBER 1, 2021
Cyber security is becoming an expensive endeavour for organisations – and in many cases, the costs are so high that they can’t deal with threats appropriately. However, it’s one thing to want to invest in cyber security, but something else entirely to set aside the budget to do so. What is cyber security as a service?

The Last Watchdog
JULY 30, 2018
One sliver of the $90 billion, or so, companies are expected to spend this year on cybersecurity products and services is an estimated $85 million they will shell out for encrypted flash drives. Related: How DataLocker got its start h. The encryption in our products is handled by a chip inside the actual hardware itself.

The Last Watchdog
NOVEMBER 12, 2023
However, there’s still a long way to go to achieve deep interoperability of interconnected services in a way that preserves privacy and is very secure. Matter works much the way website authentication and website traffic encryption gets executed. That’s because gadgets that bear the Matter logo are more readily available than ever.
Security Affairs
FEBRUARY 5, 2024
The researchers noticed that one of the iOS apps had ATS (App Transport Security) intentionally disabled. The ATS is a security mechanism that forces the use of the HTTPS protocol, which means that disabling it could open to tamper with and decrypt the traffic. “With ATS disabled, insecure communication happens. .
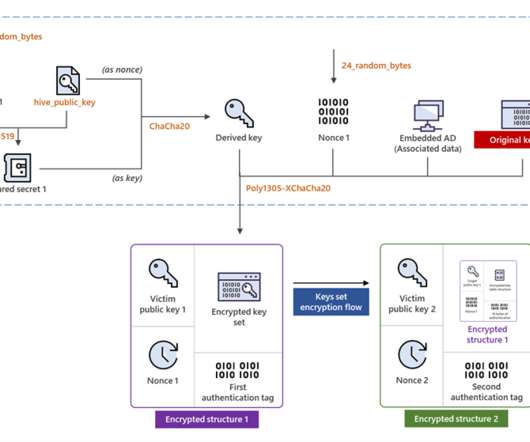
Security Affairs
JULY 6, 2022
Hive ransomware operators have improved their file-encrypting module by migrating to Rust language and adopting a more sophisticated encryption method. The most important change in the latest Hive variant is the encryption mechanism it adopts. ” reads the post published by Microsoft. ” continues Microsoft.
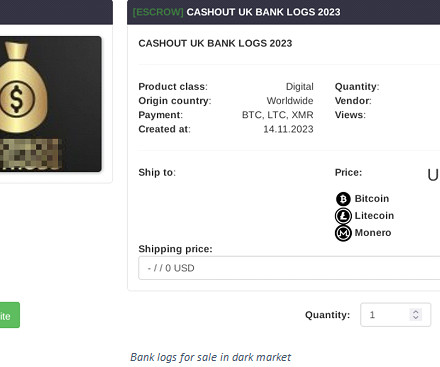
Security Affairs
DECEMBER 18, 2023
This data may include usernames, passwords, credit card numbers, social security numbers, and other sensitive information. They may use various tactics to evade antivirus and other security measures. It violates privacy and security regulations, and individuals involved in such activities can face severe legal consequences.
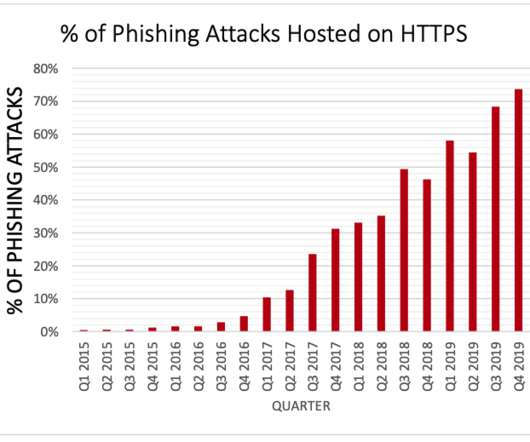
Krebs on Security
MARCH 25, 2020
Unfortunately, part of that message is misleading and may help perpetuate a popular misunderstanding about Web site security and trust that phishers have been exploiting for years now. The text I have a beef with is the bit on the right, beneath the “This site is secure” statement. government properties and phishing pages.

Thales Cloud Protection & Licensing
FEBRUARY 7, 2022
You can now implement and maintain encryption with minimal impact. However, their integration raises challenges around security, privacy, and the reliability of the underlying infrastructure. Encryption is best practice to ensure cybercriminals do not gain access to your business’s sensitive data. Initial encryption.

eSecurity Planet
JANUARY 18, 2024
When assessing the overall security of cloud storage and choosing a solution tailored to your business, it helps to determine its features, potential risks, security measures, and other considerations. It excels in remote access, scalability, and security, with distributed storage options and privacy adherence capabilities.

Security Affairs
APRIL 13, 2023
Knowing how to fight them off is entirely another. However, over one-third of businesses are impacted by insider threats every year, and US businesses face about 2.500 internal security breaches in the aggregate per day. The question isn’t why to build out an insider threat prevention program: it’s how.
Thales Cloud Protection & Licensing
OCTOBER 17, 2023
Cyber Security Awareness Month – Answering Google’s Most Commonly Asked Questions madhav Wed, 10/18/2023 - 05:25 This month is Cyber Security Awareness Month , highlighting how far security education needs to go in order to enable a secure interconnected world. Encryption What is encryption?

eSecurity Planet
NOVEMBER 10, 2023
DNS security protects the domain name system (DNS) from attackers seeking to reroute traffic to malicious sites. This article will provide an overview of DNS Security, common attacks, and how to use DNS security to prevent DNS attacks and manipulation.
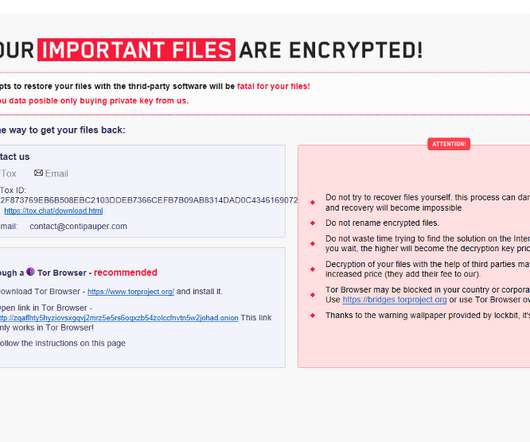
eSecurity Planet
OCTOBER 6, 2021
The malware encrypts files and spreads to the entire system to maximize damage, which forces companies to lock down the whole network to stop the propagation. Encryption is the Key. Encryption is used everywhere. Encrypting is neither hashing nor obfuscating files. What Happens During Ransomware Encryption?

Thales Cloud Protection & Licensing
JANUARY 28, 2020
An extension of the celebration for Data Protection Day in Europe, Data Privacy Day functions as the signature event of the National Cyber Security Centre’s ongoing education and awareness efforts surrounding online privacy. With the above in mind, it’s worth a discussion about specific security controls in greater detail…. Encryption.

Thales Cloud Protection & Licensing
NOVEMBER 24, 2020
Mitigating Ransomware Attacks – Decoupling Encryption Keys From Encrypted Data. Once the hackers gain an inside entry in an organisation’s IT systems, they deploy a file-encrypting malware known as ransomware. Some ransomware selectively seeks out sensitive data and will only encrypt those files. Wed, 11/25/2020 - 05:55.

The Last Watchdog
JUNE 2, 2021
A new form of agile cryptography must get established in order to robustly preserve privacy and security as all this raw data gets put to commercial use. PKI is the authentication and encryption framework on which the Internet is built. And this is where attribute-based encryption – ABE — enters the picture.

The Last Watchdog
DECEMBER 13, 2023
Related: Why IoT standards matter Digital Trust refers to the level of confidence both businesses and consumers hold in digital products and services – not just that they are suitably reliable, but also that they are as private and secure as they need to be. Threat actors are pursuing a “harvest now, decrypt later” strategy, Savin told me.

Thales Cloud Protection & Licensing
JANUARY 13, 2021
Data Encryption Shields the Energy Sector Against Emerging Threats. Security of CNI is a national security issue. Additionally, the vulnerabilities of the energy sector are of particular concern to national security due to its enabling function across all CNI systems. How to shield the energy sector. A recent U.S.

Security Affairs
MAY 4, 2022
A security researcher discovered that samples of Conti, REvil, LockBit ransomware were vulnerable to DLL hijacking. Page shared its findings through its Malvuln project exclusively dedicated to the research of security flaws in malware codes. “Conti looks for and executes DLLs in its current directory. Pierluigi Paganini.

The Last Watchdog
NOVEMBER 12, 2019
a Lehi,Utah-based supplier of digital certificates, found 71 percent of global organizations already see the emergence of quantum processing power as a material security threat. Their trepidation is focused on the potential undermining of a core security component of classical computing systems: encryption. Case in point, the U.S

Security Affairs
AUGUST 21, 2021
The US Cybersecurity and Infrastructure Security Agency (CISA) released guidance on how to prevent data breaches resulting from ransomware attacks. The post US CISA releases guidance on how to prevent ransomware data breaches appeared first on Security Affairs. Follow me on Twitter: @securityaffairs and Facebook.

ForAllSecure
MARCH 29, 2023
However, as with any software component, APIs are also prone to security vulnerabilities that can be exploited by attackers. API security is an ongoing process that demands continual attention and effort from everyone on the development team. API Basics: What Is an API and How Do APIs Work?

eSecurity Planet
MARCH 3, 2023
To protect against those threats, a Wi-Fi Protected Access (WPA) encryption protocol is recommended. And even though it’s been around since 2004, WPA2 remains the Wi-Fi security standard. WPA2 is a security protocol that secures wireless networks using the advanced encryption standard (AES).

Security Affairs
NOVEMBER 1, 2021
Positive Technologies researchers Vladimir Kononovich and Alexey Stennikov have discovered security flaws Wincor Cineo ATMs that could be exploited to bypass Black-Box attack protections and withdraw cash. The vulnerabilities discovered by the security duo impacts the Wincor Cineo ATMs with the RM3 and CMD-V5 dispensers.

The Last Watchdog
SEPTEMBER 30, 2019
Homomorphic encryption has long been something of a Holy Grail in cryptography. Related: Post-quantum cryptography on the horizon For decades, some of our smartest mathematicians and computer scientists have struggled to derive a third way to keep data encrypted — not just the two classical ways, at rest and in transit.

Dark Reading
JANUARY 7, 2022
Logic flaw exists in malware that can be used to prevent it from encrypting remote shares, security vendor says.

The Last Watchdog
MAY 8, 2019
Related: Marriott reports huge data breach Ever thought about encrypting the data held on a portable storage device? Launched as a one-man operation in 2007, DataLocker has grown into a leading manufacturer of encrypted external drives, thumb drives, flash drives and self-encrypting, recordable CDs and DVDs.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content