How to Use Signal Encrypted Messaging
WIRED Threat Level
AUGUST 18, 2022
The best end-to-end encrypted messaging app has a host of security features. Here are the ones you should care about.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

WIRED Threat Level
AUGUST 18, 2022
The best end-to-end encrypted messaging app has a host of security features. Here are the ones you should care about.

Data Breach Today
JUNE 11, 2020
Learn How To Run Deep SSL Inspection For Encrypted Traffic. View this webinar OnDemand and learn how you can run deep SSL inspection for encrypted traffic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
OCTOBER 18, 2022
A bug in the message encryption mechanism used by Microsoft in Office 365 can allow to access the contents of the messages. Researchers at the cybersecurity firm WithSecure discovered a bug in the message encryption mechanism used by Microsoft in Office 365 that can allow to access message contents due. ” concludes WithSecure.

Thales Cloud Protection & Licensing
NOVEMBER 2, 2021
Quantum Resistant Encryption – Are You Ready? When functional quantum computing becomes available it is anticipated to make many current asymmetric encryption ciphers (RSA, Diffie-Hellman, ECC etc.) Learn more about Thales solutions for quantum resistant encryption. Encryption. Tue, 11/02/2021 - 09:10. .

IBM Big Data Hub
JANUARY 22, 2024
Hackers know this might be your first instinct, and some types of ransomware notice restart attempts and cause additional harm, like damaging Windows or deleting encrypted files. Just upload a sample of the encrypted file and, if you have them, a ransom note and the attacker’s contact information.

eSecurity Planet
OCTOBER 18, 2022
However, even with the best planning, organizations can find a few users, machines, or systems that were overlooked or whose backup may be corrupted or encrypted. Also read: Best Backup Solutions for Ransomware Protection How One Company Survived a Ransomware Attack Without Paying the Ransom. How Does Ransomware Encryption Work?

IT Governance
APRIL 5, 2023
It can do this in a number of ways, such as: Stealing, encrypting or deleting sensitive information; Hijacking or altering core system functions; Monitoring user activity; and Spamming the device with adverts. Ransomware spreads through a target’s systems, encrypting files as it goes. What is malware?

Security Affairs
MARCH 26, 2019
The Hacked Ransomware was first spotted in 2017, it appends.hacked extension to the encrypted files and includes ransom notes in Italian, English, Spanish, and Turkish. In 2018, the popular malware researcher Michael Gillespie discovered a weakness in the encryption process that allowed the expert to create a decryption tool.

Thales Cloud Protection & Licensing
FEBRUARY 20, 2024
How to protect your machinelearning Models richard-r.stew… Tue, 02/20/2024 - 21:50 Dr. Werner Dondl and Michael Zunke In computer technology, few fields have garnered as much attention as artificial intelligence ( [KD1] [RJ2] AI) and machine learning (ML). An encrypted model is basically useless without the correct decryption key.

Thales Cloud Protection & Licensing
FEBRUARY 20, 2024
How to protect your machinelearning Models richard-r.stew… Tue, 02/20/2024 - 21:50 Dr. Werner Dondl and Michael Zunke In computer technology, few fields have garnered as much attention as artificial intelligence ( [KD1] [RJ2] AI) and machine learning (ML). An encrypted model is basically useless without the correct decryption key.

The Last Watchdog
MAY 3, 2021
Encryption agility is going to be essential as we move forward with digital transformation. All of the technical innovation cybersecurity vendors are churning out to deal with ever-expanding cyber risks, at the end of the day, come down to protecting encrypted data. Refer: The vital role of basic research.
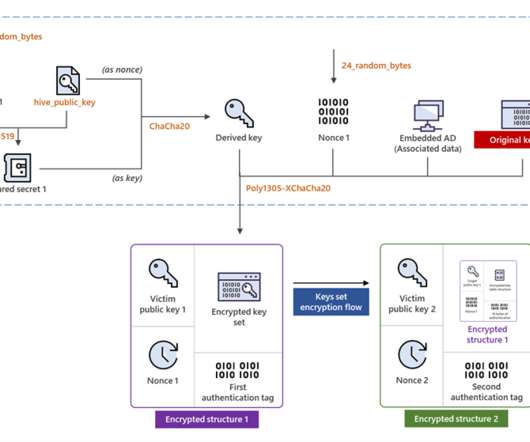
Security Affairs
JULY 6, 2022
Hive ransomware operators have improved their file-encrypting module by migrating to Rust language and adopting a more sophisticated encryption method. The most important change in the latest Hive variant is the encryption mechanism it adopts. ” reads the post published by Microsoft. ” continues Microsoft.

Thales Cloud Protection & Licensing
FEBRUARY 14, 2024
How to Protect Your Machine Learning Models madhav Thu, 02/15/2024 - 07:20 Contributors: Dr. Werner Dondl and Michael Zunke Introduction In computer technology, few fields have garnered as much attention as artificial intelligence ( AI) and machine learning (ML). An encrypted model is basically useless without the correct decryption key.

Dark Reading
NOVEMBER 3, 2021
Experts weigh in on steps network and security administrators need to take before the next time a root certificate expires.

The Last Watchdog
JULY 30, 2018
One sliver of the $90 billion, or so, companies are expected to spend this year on cybersecurity products and services is an estimated $85 million they will shell out for encrypted flash drives. Related: How DataLocker got its start h. The encryption in our products is handled by a chip inside the actual hardware itself.

The Last Watchdog
MAY 19, 2022
The best practices for securing your CMS begin with these five low-hanging-fruit steps: •Make sure that your CMS platform’s access control and encryption features are turned on and configured correctly. or higher) encryption protocol, because systems using an older version of TLS are a security risk. What can you do about it?
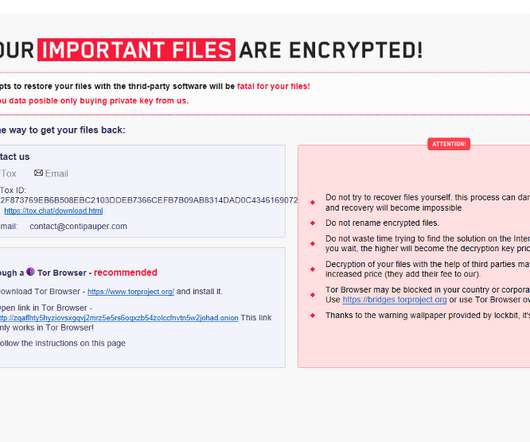
eSecurity Planet
OCTOBER 6, 2021
The malware encrypts files and spreads to the entire system to maximize damage, which forces companies to lock down the whole network to stop the propagation. Encryption is the Key. Encryption is used everywhere. Encrypting is neither hashing nor obfuscating files. What Happens During Ransomware Encryption?

The Security Ledger
JANUARY 14, 2022
The post Spotlight: ShardSecure on Protecting Data At Rest Without Encryption appeared first on The Security Ledger with Paul F. Encryption tools for securing that data are widely available, but they come with costs both in management overhead and in speed of access. Click the icon below to listen. Spotlight: COVID Broke Security.

Thales Cloud Protection & Licensing
FEBRUARY 7, 2022
You can now implement and maintain encryption with minimal impact. Encryption is best practice to ensure cybercriminals do not gain access to your business’s sensitive data. But deployment and management of encryption generally incur downtime. Most of this downtime is generated by initial encryption and re-keying data sets.

Thales Cloud Protection & Licensing
NOVEMBER 24, 2020
Mitigating Ransomware Attacks – Decoupling Encryption Keys From Encrypted Data. Once the hackers gain an inside entry in an organisation’s IT systems, they deploy a file-encrypting malware known as ransomware. Some ransomware selectively seeks out sensitive data and will only encrypt those files. Wed, 11/25/2020 - 05:55.
Security Affairs
FEBRUARY 5, 2024
It makes the app susceptible to interception where an attacker could force a victim to use the unencrypted HTTP protocol while forwarding the data to the real server, encrypted.” . “With ATS disabled, insecure communication happens. ” reads the report published by Pen Test Partners.

The Last Watchdog
JUNE 2, 2021
They outlined why something called attribute-based encryption, or ABE, has emerged as the basis for a new form of agile cryptography that we will need in order to kick digital transformation into high gear. PKI is the authentication and encryption framework on which the Internet is built. Encrypting just once.

Thales Cloud Protection & Licensing
FEBRUARY 9, 2018
With organizations around the world now deploying ever-increasing amounts of encryption solutions in an effort to ward off cybercrime, businesses are facing a combination of challenges. Protecting data through encryption. Using algorithms to encode data as ciphertext, encryption acts as a safety blanket for data.

WIRED Threat Level
NOVEMBER 23, 2019
So-called lightweight encryption has its place. But some researchers argue that more manufacturers should stick with proven methods.

Security Affairs
APRIL 13, 2023
Knowing how to fight them off is entirely another. The question isn’t why to build out an insider threat prevention program: it’s how. The origin and impact of insider risk To understand best how to combat them, it helps to know where insider threats originate and why. Knowing that insider threats are a risk is one thing.
Security Affairs
DECEMBER 18, 2023
Some info stealers may use encryption techniques to hide their communication with command-and-control servers, making it more challenging for security systems to detect malicious activities. There are various types of info stealers, each with its own specific focus.

Thales Cloud Protection & Licensing
JANUARY 28, 2020
Namely, they should implement encryption, key management and identity and access management (IAM) to help preserve the privacy of their stored data. Encryption. An organization’s digital security strategy would not be complete without encryption. Key Management. A Streamlined Data Security Strategy.

The Last Watchdog
NOVEMBER 12, 2019
Their trepidation is focused on the potential undermining of a core security component of classical computing systems: encryption. The monumental challenge is that replacing classical encryption with PQC will be complicated and time consuming. To its credit, the global cybersecurity community is not asleep on this.

Thales Cloud Protection & Licensing
JANUARY 13, 2021
Data Encryption Shields the Energy Sector Against Emerging Threats. How to shield the energy sector. The only fail-safe solution to ensure that your data is secure as it travels across the network is encryption. Encryption. Wed, 01/13/2021 - 09:42. Security of CNI is a national security issue. More About This Author >.

The Last Watchdog
SEPTEMBER 30, 2019
Homomorphic encryption has long been something of a Holy Grail in cryptography. Related: Post-quantum cryptography on the horizon For decades, some of our smartest mathematicians and computer scientists have struggled to derive a third way to keep data encrypted — not just the two classical ways, at rest and in transit.

The Last Watchdog
MAY 8, 2019
Related: Marriott reports huge data breach Ever thought about encrypting the data held on a portable storage device? Launched as a one-man operation in 2007, DataLocker has grown into a leading manufacturer of encrypted external drives, thumb drives, flash drives and self-encrypting, recordable CDs and DVDs.

Security Affairs
MAY 4, 2022
The security researcher John Page aka ( hyp3rlinx ) discovered that malware from multiple ransomware operations, including Conti , REvil , LockBit , AvosLocker , and Black Basta, are affected by flaws that could be exploited block file encryption. “Conti looks for and executes DLLs in its current directory. . Pierluigi Paganini.

Dark Reading
JANUARY 7, 2022
Logic flaw exists in malware that can be used to prevent it from encrypting remote shares, security vendor says.

eSecurity Planet
MARCH 3, 2023
To protect against those threats, a Wi-Fi Protected Access (WPA) encryption protocol is recommended. WPA2 is a security protocol that secures wireless networks using the advanced encryption standard (AES). WEP and WPA are both under 4%, while WPA2 commands a 73% share of known wireless encryption connections.

Security Affairs
AUGUST 21, 2021
The US Cybersecurity and Infrastructure Security Agency (CISA) released guidance on how to prevent data breaches resulting from ransomware attacks. The post US CISA releases guidance on how to prevent ransomware data breaches appeared first on Security Affairs. softwa re company Kaseya. . Pierluigi Paganini.

The Last Watchdog
FEBRUARY 18, 2020
It was just a few short years ago that the tech sector, led by Google, Mozilla and Microsoft, commenced a big push to increase the use of HTTPS – and its underlying TLS authentication and encryption protocol. Related: Why Google’s HTTPS push is a good thing At the time, just 50 % of Internet traffic used encryption.

Security Affairs
NOVEMBER 1, 2021
An attacker with access to the dispenser controller’s USB port can install an outdated or modified firmware version to bypass the encryption and make cash withdrawals. ATM vendors have implemented a built-in protection against black-box in modern systems, typically using end-to-end encryption between an ATM computer and the dispenser.

WIRED Threat Level
NOVEMBER 2, 2020
You can lock down your meetings like never before—even if you have to give up a few features to do so.

The Last Watchdog
DECEMBER 13, 2023
Each time we use a mobile app or website-hosted service, digital certificates and the Public Key Infrastructure ( PKI ) come into play — to assure authentication and encrypt sensitive data transfers. Acohido is dedicated to fostering public awareness about how to make the Internet as private and secure as it ought to be. (LW

WIRED Threat Level
JANUARY 29, 2020
Both iPhones and Androids are encrypted by default. But there are steps you can take to safeguard your data on backups and messaging apps.
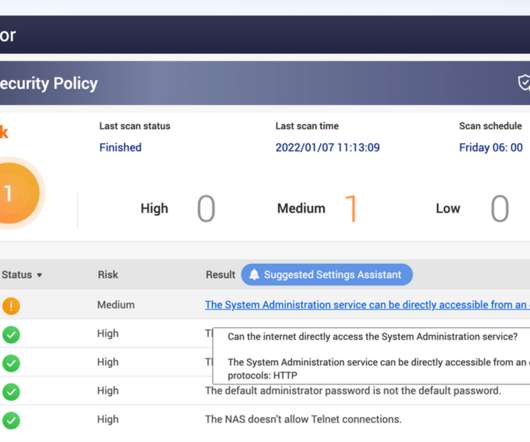
Security Affairs
JANUARY 7, 2022
The ransomware, tracked by Intezer as “ QNAPCrypt ” and “ eCh0raix ” by Anomali, is written in the Go programming language and uses AES encryption to encrypt files. The malicious code appends.encrypt extension to filenames of encrypted files. The post How to secure QNAP NAS devices? Pierluigi Paganini.

WIRED Threat Level
DECEMBER 9, 2017
Encrypt them. Want to keep outsiders from listening in on your chats, phone calls, and more? All of them.

Thales Cloud Protection & Licensing
FEBRUARY 1, 2023
How to Address the Requirements of Personal Data Protection (PDP) Law of Indonesia divya Thu, 02/02/2023 - 06:35 In response to the increased number of attacks targeting the personal data of millions of Indonesian citizens, the government passed the first Personal Data Protection (PDP) Law in 2022.

IBM Big Data Hub
FEBRUARY 23, 2024
If a breach is unlikely to harm users—for example, if the stolen data is so heavily encrypted that hackers can’t use it—the company does not need to notify data subjects. GDPR heavily encourages encryption and pseudonymization, so organizations may want to implement these controls in particular.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content