No, I Did Not Hack Your MS Exchange Server
Krebs on Security
MARCH 28, 2021
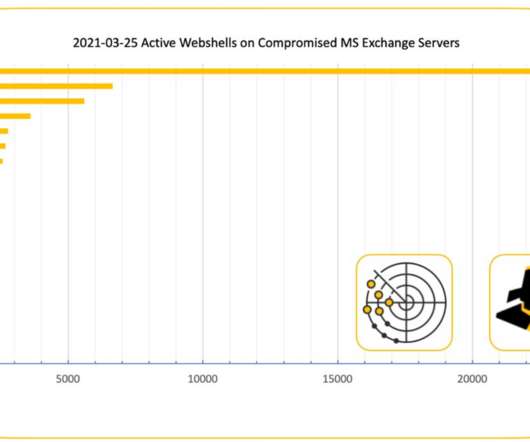
Watson said the Krebsonsecurity file will attempt to open up an encrypted connection between the Exchange server and the above-mentioned IP address, and send a small amount of traffic to it each minute. Here are a few of the more notable examples , although all of those events are almost a decade old. At Least 30,000 U.S.
































Let's personalize your content