Holy Ghost ransomware operation is linked to North Korea
Security Affairs
JULY 15, 2022
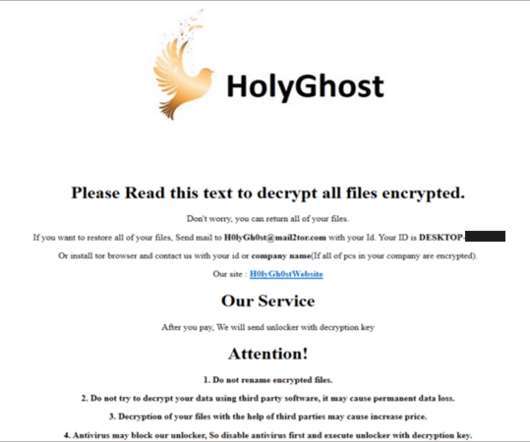
The list of victims includes manufacturing organizations, banks, schools, and event and meeting planning companies. The Holy Ghost ransomware appends the file extension.h0lyenc to filenames of encrypted files. MSTIC linked DEV-0530 to another North Korean-based group tracked as PLUTONIUM (aka DarkSeoul or Andariel ).
















































Let's personalize your content