Hundreds of organisations breached patient data rules, reveals BMJ
The Guardian Data Protection
MAY 11, 2022
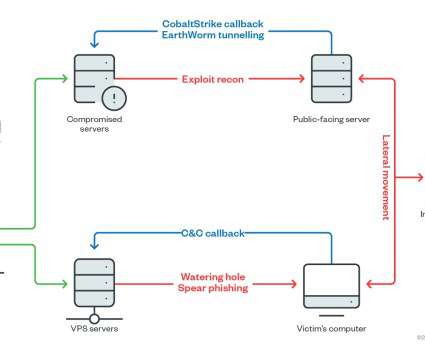
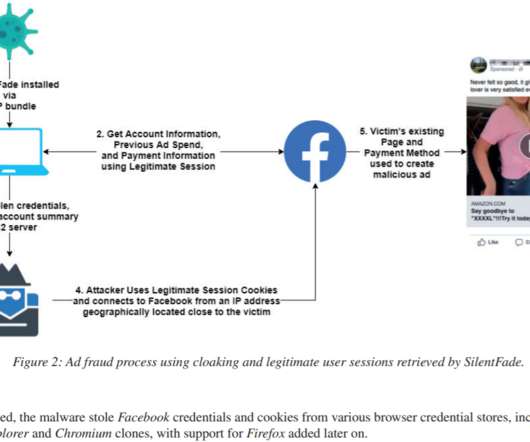
High risk” breaches were revealed to have occurred at healthcare groups, pharmaceutical giants and educational institutions including Virgin Care, GlaxoSmithKline (GSK) and Imperial College London, during audits by NHS Digital, according to an investigation by the British Medical Journal (BMJ).







































Let's personalize your content