Top 3 Black Friday 2020 scams to avoid
IT Governance
NOVEMBER 23, 2020
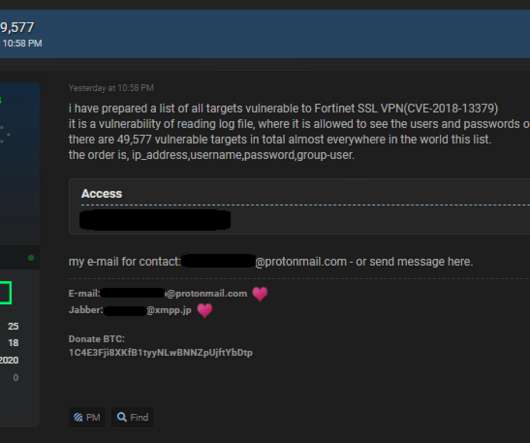
Amid the mad dash for bargains and inevitable stories of shop-floor brawls, Black Friday brings with it a spike in cyber security threats, as cyber criminals take advantage of people desperate for bargains. In this blog, we look at some of the scams you should look out for and what you can do to protect yourself. Why Black Friday is primetime for cyber crime.





































Let's personalize your content