GUEST ESSAY: In pursuit of smarter cybersecurity — to overcome complex risks and grow revenue
The Last Watchdog
JANUARY 8, 2023
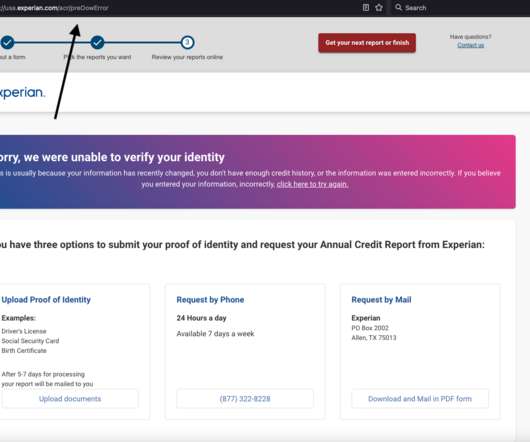
In golf there’s a popular saying: play the course, not your opponent. Related: How ‘CAASM’ closes gaps. In an enterprise, it’s the same rule. All areas of an organization need to be free to “play their own game.”. And when malware, ransomware, or other cyber threats get in the way, the focus shifts from forward progress to focused co-operation.







































Let's personalize your content