LastPass Data Breach: It's Time to Ditch This Password Manager
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.

Data Breach Today
DECEMBER 26, 2022
APT Groups Use 500 Decoy Domains of Popular NFT, DeFi Platforms North Korean attackers are using phishing websites to impersonate popular NFT platforms and DeFi marketplaces to steal digital assets worth hundreds of thousands of dollars. They set up nearly 500 decoy sites, including that of a project associated with the World Cup and NFT marketplace OpenSea.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
DECEMBER 29, 2022
How CISOs handle the ethical issues around data breaches can make or break their careers. Don't wait until a breach happens to plot the course forward.

Security Affairs
DECEMBER 25, 2022
Threat actors are actively exploiting a critical flaw in the YITH WooCommerce Gift Cards Premium WordPress plugin installed by over 50,000 websites. Hackers are actively exploiting a critical vulnerability, tracked as CVE-2022-45359 (CVSS v3: 9.8), affecting the WordPress plugin YITH WooCommerce Gift Cards Premium. The YITH WooCommerce Gift Cards Premium plugin allows websites of online stores to sell gift cards, a WordPress plugin used on over 50,000 websites.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
WIRED Threat Level
DECEMBER 29, 2022
The year was marked by sinister new twists on cybersecurity classics, including phishing, breaches, and ransomware attacks.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Schneier on Security
DECEMBER 30, 2022
Yet another smartphone side-channel attack: “ EarSpy: Spying Caller Speech and Identity through Tiny Vibrations of Smartphone Ear Speakers “: Abstract: Eavesdropping from the user’s smartphone is a well-known threat to the user’s safety and privacy. Existing studies show that loudspeaker reverberation can inject speech into motion sensor readings, leading to speech eavesdropping.

KnowBe4
DECEMBER 27, 2022
Impersonating Facebook using its own platform against them, a new phishing attack takes advantage of victim’s inability to distinguish legitimate from illegitimate.

Dark Reading
DECEMBER 30, 2022
Dark Reading's panel of security experts deliver a magnum of bubbly hot takes on what 2023 will look like, featuring evil AIs, WWIII, wild workplace soon-to-be-norms, and more.

Data Breach Today
DECEMBER 30, 2022
Website Remains Down Following Christmas Day Attack One of Europe's busiest ports is added to the list of LockBit ransomware victims. The hacking group targeted Portugal's Port of Lisbon on Christmas day, giving the facility a deadline of Jan.18 to pay a ransom of $1.5 million in exchange for their data deletion.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Schneier on Security
DECEMBER 26, 2022
Last August, LastPass reported a security breach, saying that no customer information—or passwords—were compromised. Turns out the full story is worse : While no customer data was accessed during the August 2022 incident, some source code and technical information were stolen from our development environment and used to target another employee, obtaining credentials and keys which were used to access and decrypt some storage volumes within the cloud-based storage service. […].

KnowBe4
DECEMBER 28, 2022
By Roger A. Grimes. KnowBe4 recommends that everyone use a password manager to create and use strong passwords as a part of their password policy [link].

Dark Reading
DECEMBER 29, 2022
Attackers are harvesting credentials from compromised systems. Here's how some commonly used tools can enable this.

Data Breach Today
DECEMBER 30, 2022
Agency Says It Has Temporary 'Exclusive Control' of Assets for Safe Custody The Bahamas Securities Commission seized digital assets worth $3.5 billion from local firm FTX Digital Markets. The regulator says the funds were at risk of "imminent dissipation" due to hack attacks, and will temporarily remain under its exclusive control, stored in secure digital wallets.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Lenny Zeltser
DECEMBER 30, 2022
Cybersecurity leaders not only go against threat actors to defend the organization but also find themselves at odds with other business executives. How can we avoid fighting everyone? What does it take to ensure the security team doesn't become the department of "no"? In the following conversation with Chris Cochran and Ron Eddings at Hacker Valley , I discuss how CISOs and other security leaders can: Build relationships with security and business functions.

Security Affairs
DECEMBER 25, 2022
Experts warn of a critical Linux Kernel vulnerability (CVSS score of 10) impacting SMB servers that can lead to remote code execution. A critical Linux kernel vulnerability (CVSS score of 10) exposes SMB servers with ksmbd enabled to hack. KSMBD is a Linux kernel server that implements SMB3 protocol in kernel space for sharing files over the network.

Dark Reading
DECEMBER 28, 2022
Will the bottom falling out of the cryptocurrency market have a profound impact on cybercriminal tactics and business models? Experts weigh in on what to expect.

Data Breach Today
DECEMBER 29, 2022
Global Cyber Alliance CEO Philip Reitinger Shares Updates, Challenges Global Cyber Alliance CEO Philip Reitinger shares updates on the alliance's Internet Integrity and Capacity & Resilience programs, which tackle key challenges of internet infrastructure, privacy and safety. Success is measured by the number of partners and "who is using the platform," he says.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Jamf
DECEMBER 29, 2022
Content filtering is a must for K-12 schools. In many places, it's the law. But how do you find the right one for your students from the dizzying array of content filters available?

Security Affairs
DECEMBER 24, 2022
The cybersecurity researcher RE-Solver discovered Backdoor credentials in ZyXEL LTE3301-M209 LTE indoor routers. Security researcher ReSolver announced the discovery of hardcoded credentials (CVE-2022-40602) in ZyXEL LTE3301-M209 LTE indoor routers. In previous research, the expert discovered a Telnet backdoor in D-Link DWR-921 which is also present in the ZyXEL LTE3301-M209 as well.

Dark Reading
DECEMBER 29, 2022
Businesses need to educate employees the type of social engineering attacks used by hacking group DEV-0537 (LAPSUS$) and strengthen their security posture.

Data Breach Today
DECEMBER 26, 2022
Effective testing of incident response plans continues to be a major weakness for many healthcare sector entities, especially those facing ransomware and other disruptive incidents, says Van Steel, a partner at consultancy LBMC Information Security.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

KnowBe4
DECEMBER 27, 2022
QBot malware phishing campaigns have adopted a new distribution method using SVG files to perform HTML smuggling that locally creates a malicious installer for Windows.

Troy Hunt
DECEMBER 30, 2022
We made it! That's 2022 done and dusted, and what a year it was, both professionally and personally. It feels great to get to the end of the year with all the proverbial ducks lined up, some massive achievements now behind us (not least of which was the wedding), and a clean slate coming into 2023 to do amazing things. I'm super excited about next year and can't wait to share a whole bunch of new stuff over the coming 52 Fridays.

Dark Reading
DECEMBER 27, 2022
The unfettered collaboration of the GitHub model creates a security headache. Follow these seven principles to help relieve the pain.

Data Breach Today
DECEMBER 25, 2022
Regulatory Pressure over Security, Privacy Mounts on Beleaguered Social Media Firm A member of a criminal data breach forum says he's selling email addresses and phone numbers of 400 million Twitter users. If verified, the data breach would be a further blow to Twitter and its beleaguered chief executive as regulators increase pressure over the firm's security practices.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

KnowBe4
DECEMBER 29, 2022
New data focused on cyberattacks in the second half of the year-to-date shows phishing taking the overwhelming lead as the initial attack vector of choice.
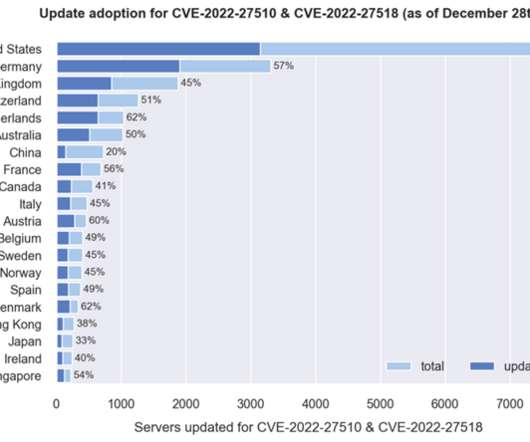
Security Affairs
DECEMBER 29, 2022
Researchers warn of thousands of Citrix Application Delivery Controller (ADC) and Gateway endpoints are still unpatched. NCC Group’s Fox-IT research team warns of thousands of Citrix ADC and Gateway endpoints remain vulnerable to two critical vulnerabilities, tracked as CVE-2022-27510 and CVE-2022-27518 (CVSS scores: 9.8), that the company addressed in recent months.

Dark Reading
DECEMBER 29, 2022
Security leaders from a media corporation, a commercial real estate company, and an automotive technology company share how they address cyber-risk.
Let's personalize your content