Taking on SOAR: The Challenges and Opportunities
Data Breach Today
MAY 18, 2021
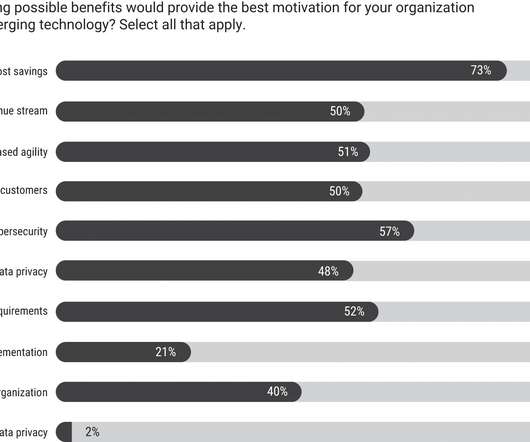
Experts Say the Technologies Won't Mean Fewer SOC Analyst Jobs Security orchestration, automation and response technologies, or SOAR, give organizations the ability to manage an increasing number of alerts. But security experts say there's no worry that SOAR will replace people. In fact, SOAR could help with staff retention.





































Let's personalize your content