Twitter Rushes to Fix Flaw in Android Version
Data Breach Today
AUGUST 6, 2020
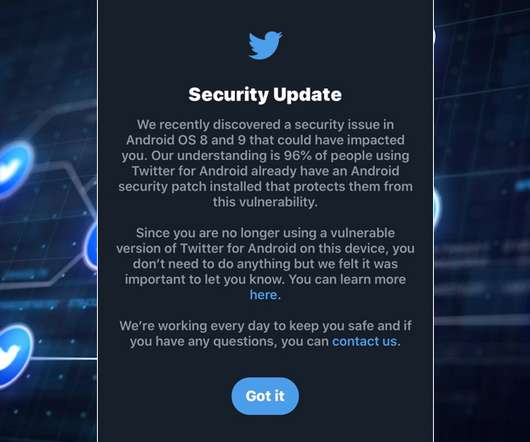
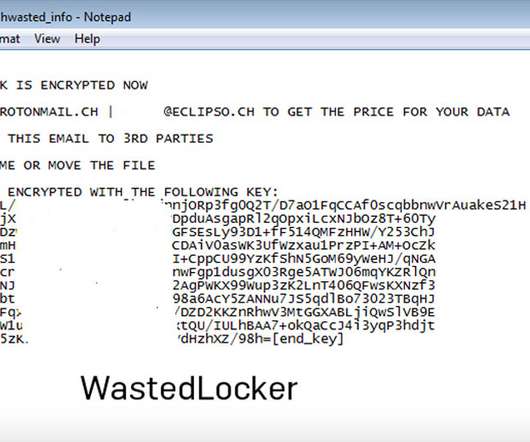
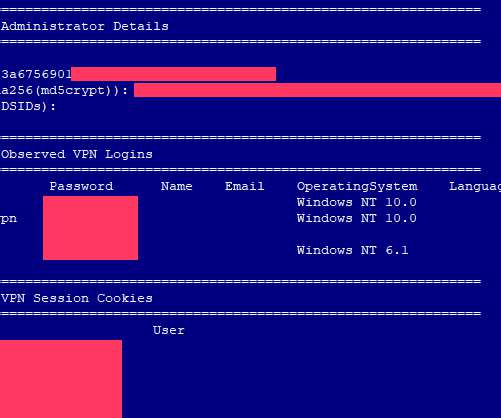
Vulnerability Could Enable Hackers to Access User Data, Including Direct Messages Twitter rushed out a fix for a flaw in the Android version of its social media platform that could have allowed hackers to access user data, including within the direct message feature. The news comes as more details have emerged about a recent Twitter hacking incident.


































Let's personalize your content