Riding the State Unemployment Fraud ‘Wave’
Krebs on Security
MAY 23, 2020
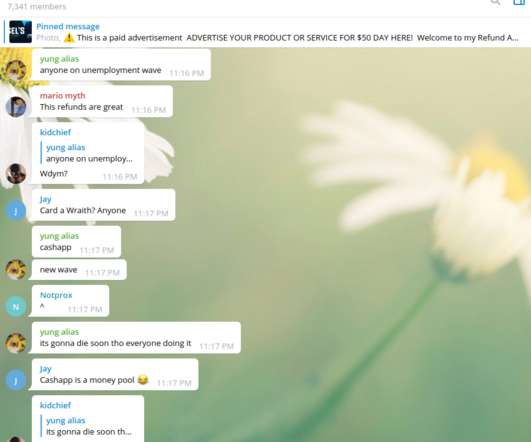
When a reliable method of scamming money out of people, companies or governments becomes widely known, underground forums and chat networks tend to light up with activity as more fraudsters pile on to claim their share. And that’s exactly what appears to be going on right now as multiple U.S. states struggle to combat a tsunami of phony Pandemic Unemployment Assistance (PUA) claims.



































Let's personalize your content