Small business cyber security: the ultimate guide
IT Governance
SEPTEMBER 24, 2020
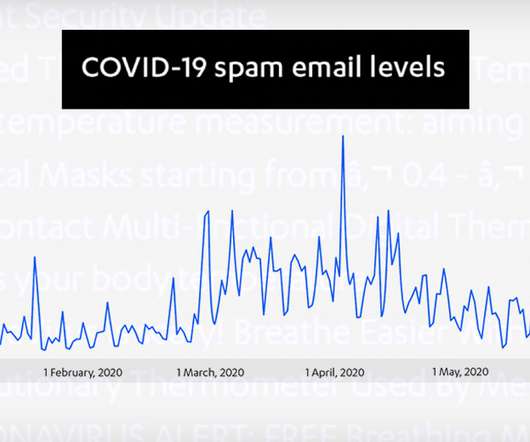
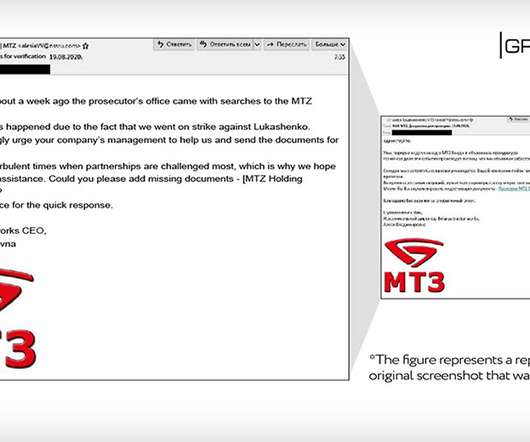
If you’re an SME, cyber security might feel seem impossibly complex and filled with endless pitfalls. Although it’s true that there’s a lot at stake – with ineffective security measures potentially threatening your productivity, your bank accounts, and your employees’ and third parties’ personal data – the path to effective security needn’t be difficult.





































Let's personalize your content