Ransomware Risk Management: 11 Essential Steps
Data Breach Today
DECEMBER 18, 2019
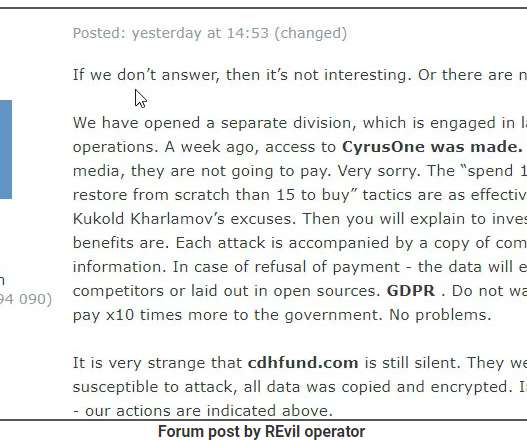
Tips From a Cybersecurity Veteran on Winning the Battle In this in-depth blog, a long-time cybersecurity specialist who recently joined the staff of Information Security Media Group sizes up evolving ransomware risks and offers a list of 11 critical mitigation steps.





































Let's personalize your content