IRS To Ditch Biometric Requirement for Online Access
Krebs on Security
FEBRUARY 7, 2022
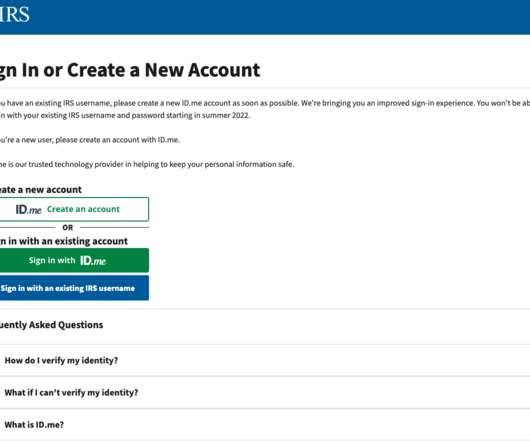
The Internal Revenue Service (IRS) said today it will be transitioning away from requiring biometric data from taxpayers who wish to access their records at the agency’s website. The reversal comes as privacy experts and lawmakers have been pushing the IRS and other federal agencies to find less intrusive methods for validating one’s identity with the U.S. government online.






































Let's personalize your content