15 Cybersecurity Pitfalls and Fixes for SMBs
Threatpost
APRIL 5, 2021
In this roundtable, security experts focus on smaller businesses offer real-world advice for actionable ways to shore up defenses using fewer resources.

Threatpost
APRIL 5, 2021
In this roundtable, security experts focus on smaller businesses offer real-world advice for actionable ways to shore up defenses using fewer resources.

DXC Technology
APRIL 8, 2021
Many companies are eager to use artificial intelligence (AI) in production, but struggle to achieve real value from the technology. What’s the key to success? Creating new services that learn from data and can scale across the enterprise involves three domains: software development, machine learning (ML) and, of course, data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

AIIM
APRIL 6, 2021
In a truly all-digital world, there would be no need for printers – or scanners or document couriers. Documents would never need to be printed, and processes would run smoothly from all-electronic input to all-electronic output. This may already the reality for some leading companies, but for most organizations, forms, contracts, agreements, and signoffs are still rooted in wet ink on paper.

Data Breach Today
APRIL 4, 2021
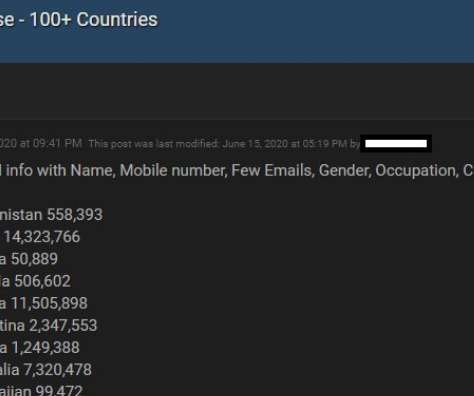
Facebook Says Data Comes from Previously Reported 2019 Incident A security researcher found more than 500 million Facebook records made available for free on the darknet, exposing basic user information including any phone numbers associated with accounts. Facebook says this is “old data” previously reported.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Krebs on Security
APRIL 6, 2021
Ne’er-do-wells leaked personal data — including phone numbers — for some 553 million Facebook users this week. Facebook says the data was collected before 2020 when it changed things to prevent such information from being scraped from profiles. To my mind, this just reinforces the need to remove mobile phone numbers from all of your online accounts wherever feasible.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
APRIL 8, 2021
Document Management is the use of a software application to track digital documents from creation through approval and publication. It serves in many ways to apply a formal governance framework to the document creation and collaborative editing processes. Today document management is generally incorporated as a set of capabilities in a broader enterprise content management (ECM) or information management solution.

Data Breach Today
APRIL 6, 2021
Gemini Advisory Says Russian Cybercriminal Sold Gift Card, Payment Card Data A Russian-speaking cybercriminal recently sold on a darknet forum thousands of stolen payment and gift cards that researchers at Gemini Advisory believe were taken from the now defunct online gift card exchange Cardpool.com.
Krebs on Security
APRIL 5, 2021
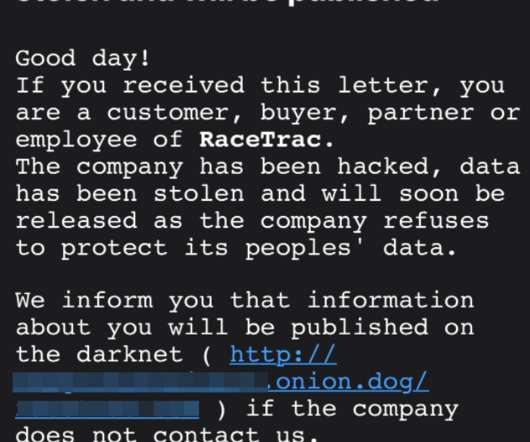
Some of the top ransomware gangs are deploying a new pressure tactic to push more victim organizations into paying an extortion demand: Emailing the victim’s customers and partners directly, warning that their data will be leaked to the dark web unless they can convince the victim firm to pay up. This letter is from the Clop ransomware gang, putting pressure on a recent victim named on Clop’s dark web shaming site. “Good day!

The Last Watchdog
APRIL 5, 2021
We live in a time where technology is advancing rapidly, and digital acceleration is propelling development teams to create web applications at an increasingly faster rhythm. The DevOps workflow has been accompanying the market shift and becoming more efficient every day – but despite those efforts, there was still something being overlooked: application security.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Schneier on Security
APRIL 9, 2021
Unknown hackers attempted to add a backdoor to the PHP source code. It was two malicious commits , with the subject “fix typo” and the names of known PHP developers and maintainers. They were discovered and removed before being pushed out to any users. But since 79% of the Internet’s websites use PHP, it’s scary. Developers have moved PHP to GitHub, which has better authentication.
Data Breach Today
APRIL 9, 2021
Cisco Talos: Reliance on These Tools Expands Attack Surface The increasing reliance on collaboration tools such as Slack and Discord to support those working remotely during the COVID-19 pandemic has opened up new ways for fraudsters and cybercriminals to bypass security tools and deliver malware, Cisco Talos reports.

Troy Hunt
APRIL 9, 2021
"What a s**t week". I stand by that statement in the opening couple of minutes of the video and I write this now at midday on Saturday after literally falling asleep on the couch. The Facebook incident just dominated; everything from processing data to writing code to dozens of media interviews. And I ran a workshop over 4 half days. And had 2 lots of guests visiting.

The Last Watchdog
APRIL 7, 2021
Passwordless authentication as a default parameter can’t arrive too soon. Related: Top execs call for facial recognition to be regulated. The good news is that passwordless technologies are not only ready for prime time, they appear to be gaining traction in ways that suggest we’re on the cusp of a period of wide-scale adoption. That’s the upshot of a new report, The State of Passwordless Security 2021 , put out by HYPR , a New York City-based supplier of advanced authentication systems.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Threatpost
APRIL 9, 2021
Like the Facebook incident earlier this week, the information — including user profile IDs, email addresses and other PII -- was scraped from the social-media platform.
Data Breach Today
APRIL 8, 2021
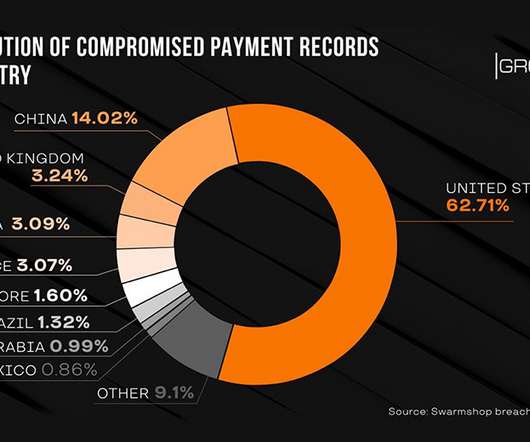
Group-IB: Administrator, Seller and Buyer Data Also Stolen For the second time in two years, the contents of the darknet payment card marketplace Swarmshop have been removed and posted to a competing underground forum, Group-IB reports. The content includes data on more than 600,000 payment cards as well as administrator, seller and buyer information.
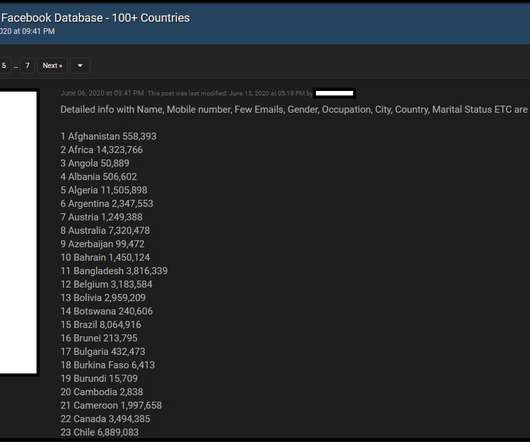
Security Affairs
APRIL 3, 2021
On April 3, a user has leaked the phone numbers and personal data of 533 million Facebook users in a hacking forum for free online. Bad news for Facebook, a user in a hacking forum has published the phone numbers and personal data of 533 million Facebook users. The availability of the data was first reported by Alon Gal, CTO of cyber intelligence firm Hudson Rock.

Troy Hunt
APRIL 8, 2021
Another month, another national government to bring onto Have I Been Pwned. This time it's the Ukrainian National Cybersecurity Coordination Center who now has access to monitor all their government domains via API domain search, free of charge. The Ukraine is now the 13th government to be onboarded to HIBP's service joining counterparts across Europe, North America and Australia.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.
WIRED Threat Level
APRIL 6, 2021
The encrypted messaging app is integrating support for MobileCoin in a bid to keep up with the features offered by its more mainstream rivals.

Data Breach Today
APRIL 9, 2021
ISMG Editors Discuss Hot Topics, Including Health Data Breaches Four editors at Information Security Media Group discuss important cybersecurity issues, including President Biden’s latest cybersecurity proposals and large vendor-related breaches in healthcare.

Schneier on Security
APRIL 7, 2021
According to Wired , Signal is adding support for the cryptocurrency MobileCoin, “a form of digital cash designed to work efficiently on mobile devices while protecting users’ privacy and even their anonymity.” Moxie Marlinspike, the creator of Signal and CEO of the nonprofit that runs it, describes the new payments feature as an attempt to extend Signal’s privacy protections to payments with the same seamless experience that Signal has offered for encrypted conversations

Thales Cloud Protection & Licensing
APRIL 8, 2021
Safe-T Has Partnered with Thales to Bring a New Remote Access Security Solution to the Table. madhav. Thu, 04/08/2021 - 07:38. The global pandemic of 2020 has changed the world around us in drastic and likely permanent ways. One of the most significant effects the pandemic has had on daily life is the need for businesses to support employees choosing to work from home.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
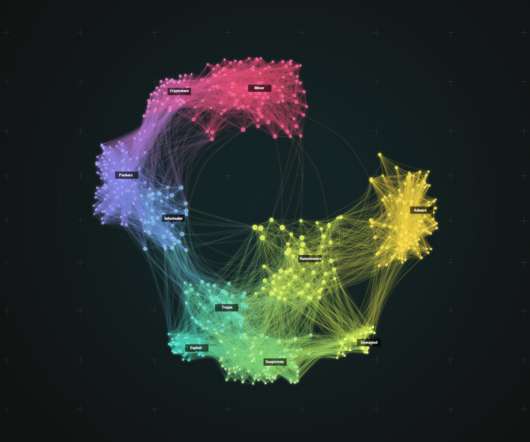
Elie
APRIL 5, 2021
We present Spotlight, a large-scale malware lead-generation framework that uses deep-learning to clusters malware famillies to isolate potentially-undiscovered ones and prioritizes them for further investigation.

Data Breach Today
APRIL 9, 2021
Andy Purdy, the chief security officer for Huawei Technologies USA who formerly worked on the White House staff and in the Department of Homeland Security, discusses cybersecurity best practices.

Security Affairs
APRIL 9, 2021
Cisco announced it will not release security updates to address a critical security vulnerability affecting some of its Small Business routers. Cisco is urging customers that are using some of its Small Business routers to replace their devices because they will no longer receive security updates. According a security advisory published by the company, Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers are affected by Remote Command Execution vulnerability that resides in the Managem

Schneier on Security
APRIL 5, 2021
The new 802.11bf standard will turn Wi-Fi devices into object sensors: In three years or so, the Wi-Fi specification is scheduled to get an upgrade that will turn wireless devices into sensors capable of gathering data about the people and objects bathed in their signals. “When 802.11bf will be finalized and introduced as an IEEE standard in September 2024, Wi-Fi will cease to be a communication-only standard and will legitimately become a full-fledged sensing paradigm,” explains Fra

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
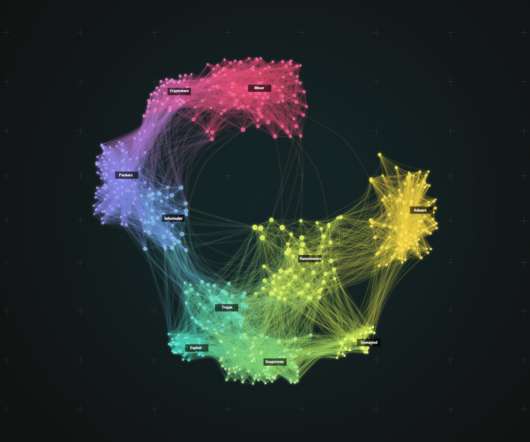
Elie
APRIL 4, 2021
Malware is one of the key threats to online security today, with applications ranging from phishing mailers to ransomware and trojans. We present Spotlight, a large-scale malware lead-generation framework.
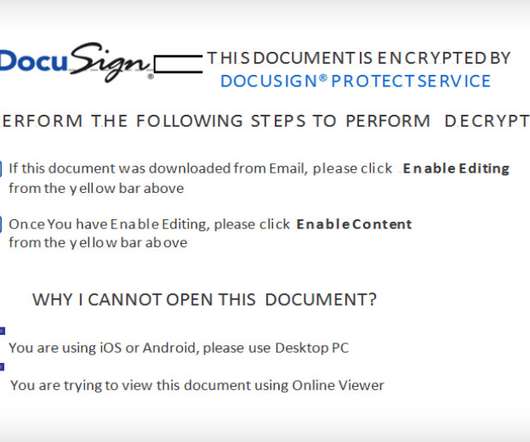
Data Breach Today
APRIL 8, 2021
Report: Builder Allows Cybercriminals to Create Specialized Office Documents Cybercriminal gangs are using a newly uncovered malicious document builder called "EtterSilent" to create differentiated and harder-to-discover malicious documents that can be deployed in phishing attacks. The most recent strike using EtterSilent was launched in late March.

Threatpost
APRIL 6, 2021
Cyberattackers are actively exploiting known security vulnerabilities in widely deployed, mission-critical SAP applications, allowing for full takeover and the ability to infest an organization further.
Let's personalize your content