Ransomware + Exfiltration + Leaks = Data Breach
Data Breach Today
JULY 7, 2020
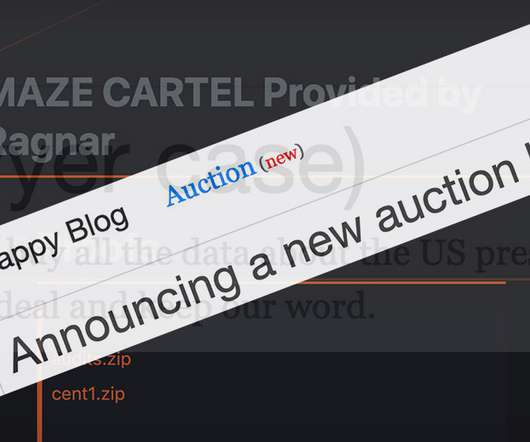
Data-Leaking Extortionists' Revised Playbook Goes Way Beyond Ransomware Ransomware-wielding attackers continue to pummel organizations. But labeling these as being just ransomware attacks often misses how much these incidents involve serious network intrusions, exfiltration of extensive amounts of data, data leaks and, as a result, reportable data breaches.



































Let's personalize your content