How COVID-19 will change how we work FOREVER
OpenText Information Management
MARCH 12, 2020
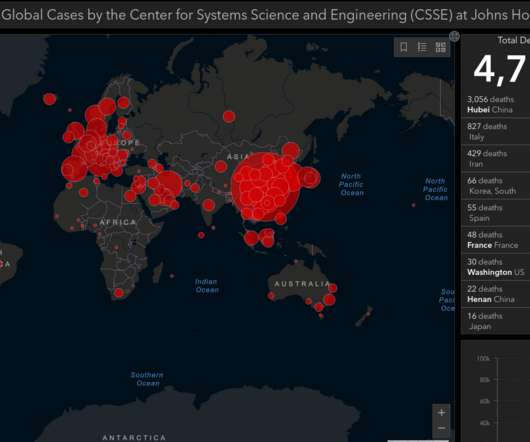
Global supply chains, especially in the manufacturing sector have experienced many different forms of disruption over the years – from earthquakes and tsunamis through to social unrest and even piracy in the Indian Ocean. Each disruption brings with it uncertainty in terms of how suppliers will be impacted and how long the disruption will last … The post How COVID-19 will change how we work FOREVER appeared first on OpenText Blogs.






































Let's personalize your content