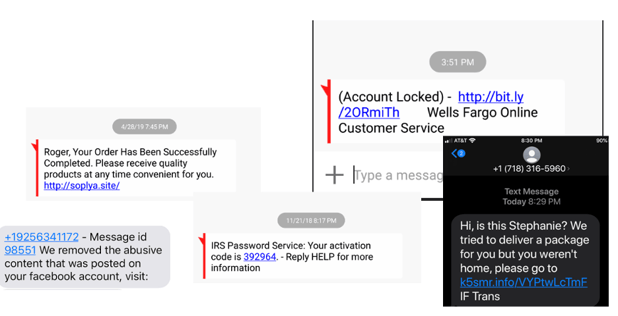
 Phishing via Short Message Service (SMS) texts, what is known as smishing, is becoming increasingly common (some examples are shown below). There is probably not a person on Earth who does not get at least one smishing message a month. It is a big problem.
Phishing via Short Message Service (SMS) texts, what is known as smishing, is becoming increasingly common (some examples are shown below). There is probably not a person on Earth who does not get at least one smishing message a month. It is a big problem.
The U.S. government has been warning about them for years, including here.
We have been warning about SMS scams for years as well, including here:
- https://blog.knowbe4.com/44-million-dollar-smishing-problem
- https://blog.knowbe4.com/smishing-examples-defenses
- https://blog.knowbe4.com/advanced-android-sms-phishing
- https://blog.knowbe4.com/why-should-we-care-about-personal-smishing-attacks
The Problem With SMS Messages
Unlike Internet browsers and email programs that display URL links, you cannot “hover” over a link to see what it really is or where it will take you. The good news is that what you see is what you get. There is no need to hover. What you can see is the real link…at least the initial link that is being displayed. There is no secondary link “under-the-covers” that is the real link, like you get with non-SMS messages. That is the only good news.
The bad news is that most of the links shown in SMS are “shortened” links that lead to other links which may lead to other links with no good way to inspect or filter them before you and your phone arrive at the final destination.
Unfortunately, there are far less methods and tools to examine the links you can see in an SMS message to determine if they are going to take you to a legitimate or malicious site. In the non-SMS-message world, you cannot only hover over the link, but there is likely to be multiple content-inspecting tools which will try to determine if the involved link is malicious or not. In the regular computer world, usually your Internet browser or email program has content inspection built-in, you probably have an antivirus program that inspects all downloaded content, and you or your organization may have additional layers of inspection, all of which help to detect and block malicious content. They do not always succeed, but at least you have a defense-in-depth chance.
Not so much with SMS.
Inspecting SMS Links
There are a variety of tricks used by SMS phishers that make smishing harder to review. Here are some of the issues and how to mitigate them.
Most SMS links are created with “shortening services”, which take you to a longer eventual destination link (example https://info.example.com/dsdata/trinity004/tlreport.html) and substitute it with something shorter (ex: https://t.co/ls4raG). These services became vogue back when Twitter only allowed 140-character messages. Any included URL could easily take up all 140 characters or at least enough of them that typing in a useful message became difficult. Today, there are dozens of URL shortening services. The top public ones are:
- ly
- gl (Google)
- com
- co (Twitter)
It is the rare smishing message that does not use a shortened URL. URL shortening is so common and useful that malware developers often develop their own shortening services so they can generate shortened URLs that look legitimate (ex: https://m.awss.com/s14/microsoft.com).
The good thing about shortened URLs that they can be “expanded” without having to actually click on them. There are almost as many “expander” websites that will expand shortened URLs for you as there are shortening services. You copy or type in the shortened URL and it tells you what the longer URL substitution is. The one I use most of the time is Expand URL (ex: https://www.expandurl.net/expand).
Unfortunately, many smishes use “nested” shortened URLs, sort of like a digital Russian Matryoshka dolls. They will have a shortened URL that leads to another shortened URL that leads to another shortened URL. Turns out many malware and URL inspection services do not handle nesting at all or only through a certain number of nestings (say three or four). The more nestings a smish can use, the more likely they are to avoid malware detection.
Submit Link to an Inspection Site
You can always copy or retype the link to an online URL inspection service like Google’s VirusTotal. VirusTotal will inspect your submitted link and review the resulting content with all the antivirus scanning engines capable of scanning URLs they have available during the submission, which at last count (on 11/8/22 was 68).
I will note that plenty of truly malicious links come up as not having anything detected as malicious by any of the antivirus scanners on VirusTotal when I use it. Do not take a malicious score of 0/68 as guaranteeing the URL is safe. The same is true on other content inspection sites, like Google Safe Browsing. The way I use them is that if my submission comes away as clean, then I still mostly stay suspicious about it. But if two or more antivirus engines detect the submitted URL link as malicious, it is definitely malicious, and the inspection engine usually helps to identify the malware variant being used.
URL Detonation on a Safe Computer
You can also type or copy the link to a known, clean, trusted locked down virtual machine that you use for forensic inspection. That virtual machine should not be connected to your local network. The only connection it should possibly have is a connection to the Internet. You should not log into any application/site/service that you normally log into (at least using the same login names and passwords). You must assume that any active malware content you accidentally execute can grab all the passwords located within the virtual machine image.
I run my forensic images with Microsoft’s free Sysinternals process utilities, including Autoruns and Process Explorer, and Sysinternals TCPView. For quick or detailed forensic investigations, these utilities do everything but malware code analysis.
Note: It can be very tricky to copy a URL link from an SMS message without accidentally selecting or activating it. Learn how your phone works with your favorite SMS app to allow you to copy and paste URL links. Then try your best not to mess up. I am so fearful of accidentally activating potentially malicious URLs that I simply retype them when I need them. Usually, they are shortened URLs and fairly easy to retype.
When In Doubt, Throw It Out
I also think a valid choice is simply to discard any unexpected SMS message that has a link in it. I occasionally get valid SMS messages from vendors, but nothing that is an emergency that requires that I absolutely click on a link right away. Ninety-nine percent of the time, it is a spam or phishing attack, so I can safely ignore it.
Why Doesn’t Someone Create an App That Inspects SMS URLs?
You may ask yourself why someone does not create a URL inspection service for SMS. That is because the SMS app vendors will not allow any third parties to interface with their applications. It is for safety reasons. If you allow legitimate vendors to interface with your app, you significantly raise the risk that rogue parties will also gain access. So, they throw it out and refuse to let anyone interface or control their SMS applications. Probably a smart decision on their part. Plus, if you do click on an SMS link that will open it up in the browser of your choice and the hope is that the browser has better content inspection capabilities. But relying on hope is not a good security strategy. Instead, use the recommendations listed above if you want to inspect an SMS URL before clicking on it.
Education Is the Key
You need to tell your employees (and family and friends) about SMS-based phishing messages. First, explain what SMS-based phishing is and give some popular examples (e.g., FedEx and Amazon messages seem to be very popular). Most people already know about SMS-based phishing, but I guarantee that a few people do not. I still have people come up to me at presentations and ask me what I meant by phishing, social engineering or patching. Do not assume that because you and 99% of the world knows something that everyone knows it.
Second, teach them how to recognize a smishing attack and how to treat it. This is what I tell my friends and co-workers about how to recognize any phishing attack, including an SMS-based phishing attack. If the message is unexpected, is requesting something new for the first time from the sender and if doing what the sender is requesting you to do could potentially harm you or your organization’s interests (i.e., they want you to provide confidential information or download a file), then slow down and investigate more before clicking.
SMS phishing is gaining steam. There is more of it than ever. We can expect smishing to get more mature and tricker as time goes on. It is best to develop and teach good SMS URL inspection habits while you can.
 Here's how it works:
Here's how it works:




