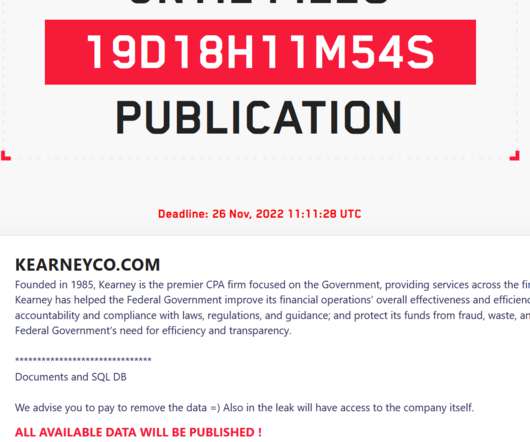
Who is Extorting Australian Health Insurer Medibank?
Data Breach Today
NOVEMBER 8, 2022
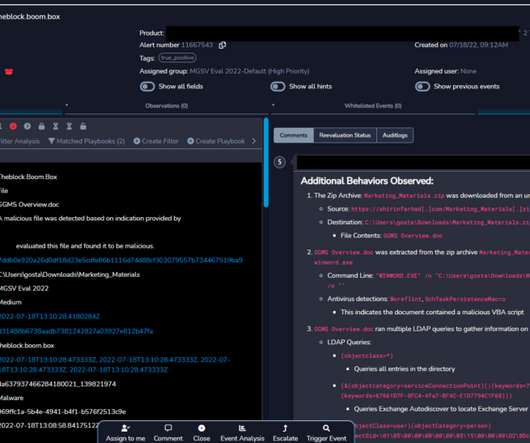
A Ransomware Group Has Given Medibank 24 Hours to Pay. But Medibank Says it Won't. Who is attempting to extort Australian health insurer Medibank, why did Medibank tell its attackers it wouldn't pay a ransom and will this deter future cyber extortionists? Here are a few thoughts on the high cybercrime drama playing out.



































Let's personalize your content