2020 Cyber Threats, Trends and Attacks
Data Breach Today
MAY 5, 2020
What You Don't See Now, Can Hurt You Later

Data Breach Today
MAY 5, 2020
What You Don't See Now, Can Hurt You Later

Data Breach Today
MAY 4, 2020
Trump Bans Use of Foreign Equipment That Poses 'National Security Threat' Declaring that threats to the United States' power grid are a national emergency, President Donald Trump is taking steps designed to help defend the grid from foreign interference by focusing on the supply chain.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
MAY 7, 2020
This is a good explanation of an iOS bug that allowed someone to break out of the application sandbox. A summary: What a crazy bug, and Siguza's explanation is very cogent. Basically, it comes down to this: XML is terrible. iOS uses XML for Plists , and Plists are used everywhere in iOS (and MacOS). iOS's sandboxing system depends upon three different XML parsers, which interpret slightly invalid XML input in slightly different ways.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Dark Reading
MAY 4, 2020
Researchers warn the installers are legitimate but don't come from official sources of the Zoom app, including the Apple App Store and Google Play.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
MAY 6, 2020
Researchers: Malware Is Capable of Launching DDoS Attacks Kaiji, a newly discovered botnet, is compromising Linux servers and IoT devices using brute-force methods that target the SSH protocol, according to the security firm Intezer. The botnet has the capability to launch DDoS attacks.

Data Breach Today
MAY 4, 2020
Nintendo Was Likely Anticipating the Dump After 2018 Intrusion Gamers are poring over a massive leak of Nintendo data, including source code for older gaming systems, prototypes of games and extensive software and hardware documentation. The data likely dates from a 2018 network intrusion at Nintendo.

Data Breach Today
MAY 8, 2020
The latest edition of the ISMG Security Report analyzes the many challenges involved in developing and implementing contact-tracing apps to help in the battle against COVID-19. Also featured: A discussion of emerging privacy issues and a report on why account takeover fraud losses are growing.

Threatpost
MAY 5, 2020
The vulnerability is one of 39 affecting various aspects of the mobile OS that the company fixed in a security update this week.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

WIRED Threat Level
MAY 4, 2020
As contact tracing plans firm up, the tech giants are sharing new details for their framework—and a potential app interface.

Dark Reading
MAY 6, 2020
Hackers are hitting the sports industry hard on social media and luring quarantined consumers with offers of free streaming services, a new report shows.

Security Affairs
MAY 5, 2020
A proof-of-concept (PoC) exploit for the recently fixed CVE-2020-1967 denial-of-service (DoS) issue in OpenSSL has been made public. Recently, the OpenSSL Project released a security update for OpenSSL that patches a high-severity vulnerability, tracked as CVE-2020-1967 , that can be exploited by attackers to launch denial-of-service (DoS) attacks. The CVE-2020-1967 vulnerability has been described as a “segmentation fault” in the SSL_check_chain function, it is the first issue addressed in Op

WIRED Threat Level
MAY 3, 2020
A recent infection, which managed to plunder a company's network within hours, demonstrates why the malware has become so prevalent.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Breach Today
MAY 5, 2020
Campaign Designed to Harvest Credentials of Financial Industry Regulatory Authority Members The Financial Industry Regulatory Authority, a private organization that helps self-regulate brokerage firms and exchange markets in the U.S., warns that a "widespread, ongoing" phishing campaign is targeting its members.
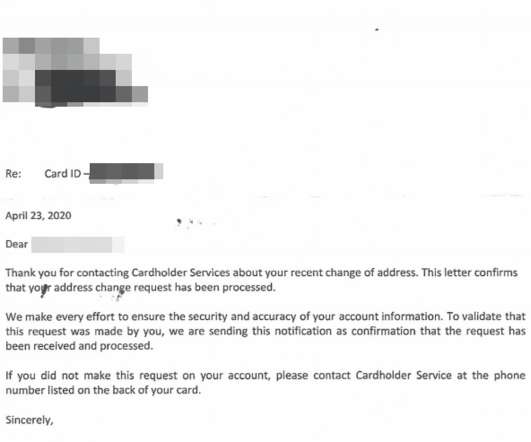
Krebs on Security
MAY 8, 2020
Millions of Americans now filing for unemployment will receive benefits via a prepaid card issued by U.S. Bank , a Minnesota-based financial institution that handles unemployment payments for more than a dozen U.S. states. Some of these unemployment applications will trigger an automatic letter from U.S. Bank to the applicant. The letters are intended to prevent identity theft, but many people are mistaking these vague missives for a notification that someone has hijacked their identity.

AIIM
MAY 6, 2020
The concept of a digital mailroom has been around a while. The idea is pretty simple - all incoming mail is scanned on entry and delivered electronically to the appropriate department or process. In reality, only mail with business value is likely to be processed. This will predominantly be documents with a structure such as forms, orders, invoices, delivery dockets, and vouchers.
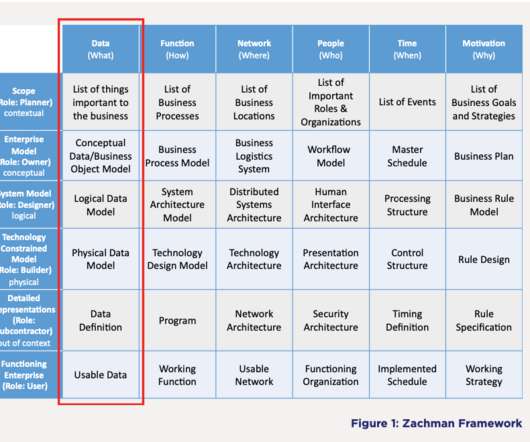
erwin
MAY 7, 2020
Although there is some crossover, there are stark differences between data architecture and enterprise architecture (EA). That’s because data architecture is actually an offshoot of enterprise architecture. In simple terms, EA provides a holistic, enterprise wide overview of an organization’s assets and processes, whereas data architecture gets into the nitty gritty.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Data Breach Today
MAY 7, 2020
'Unauthorized Individual' Accessed SSH File, Company Says Web hosting giant GoDaddy confirms that a data breach has affected about 28,000 of its customers' web hosting accounts, according to a news report. The company has reset passwords and usernames for some customers as a precaution, although it says no data appears to have been altered.

The Guardian Data Protection
MAY 7, 2020
MPs and rights groups have warned lack of data protection could make UK app illegal Coronavirus – latest updates See all our coronavirus coverage The government has left open the prospect of ditching its own contact-tracing app in favour of the “decentralised” model favoured by Apple and Google after it was revealed that a feasibility study into such a change is under way.

AIIM
MAY 7, 2020
Too often, I hear IIM professionals complain about this issue. "People aren't reading our IIM policy," they say. "I wish our organization forced everybody to read the policy. That way they would know what the IIM requirements are.". My response is always the same: Given the choice, 99% of the people in your organization will never read your IIM policy.
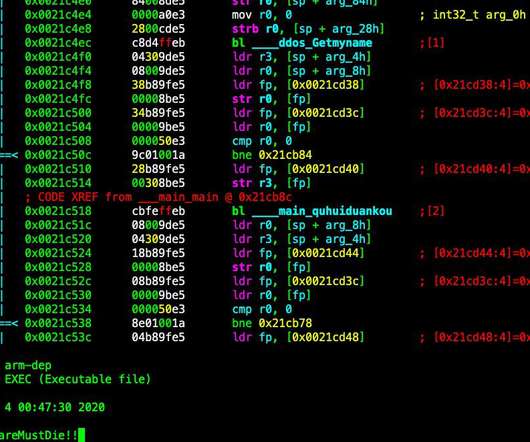
Security Affairs
MAY 5, 2020
Security researchers spotted a new piece of DDoS bot dubbed Kaiji that is targeting IoT devices via SSH brute-force attacks. Last week, the popular security researcher MalwareMustDie and the experts at Intezer Labs spotted a new piece of malware dubbed Kaiji, that is targeting IoT devices via SSH brute-force attacks. The malicious code was designed to target Linux-based servers and Internet of Things (IoT) devices and use them as part of a DDoS botnet.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Data Breach Today
MAY 5, 2020
'Password-Spraying' Campaigns Aimed at Stealing Research Data, US and UK Authorities Warn Authorities in the U.S. and U.K. are warning medical institutions, pharmaceutical companies, universities and others about "password-spraying campaigns" by advance persistent threat groups seeking to steal COVID-19 research data. Security experts outline defensive steps that organizations can take.
The Guardian Data Protection
MAY 2, 2020
Exclusive: Privacy experts say the breach in the SkillsSelect platform, which affects data going back to 2014, was ‘very serious’ Privacy experts have blasted the home affairs department for a data breach revealing the personal details of 774,000 migrants and people aspiring to migrate to Australia, including partial names and the outcome of applications.

Threatpost
MAY 8, 2020
The Shiny Hunters hacking group said it stole 500 GB of data from the tech giant’s repositories on the developer platform, which it owns.

Security Affairs
MAY 5, 2020
GoDaddy has been notifying its customers of a data breach, threat actors might have compromised their web hosting account credentials. GoDaddy has been notifying its customers of a data breach, attackers might have compromised users’ web hosting account credentials. Headquartered in Scottsdale, Arizona, the Internet domain registrar and web hosting company claims to have over 19 million customers worldwide.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
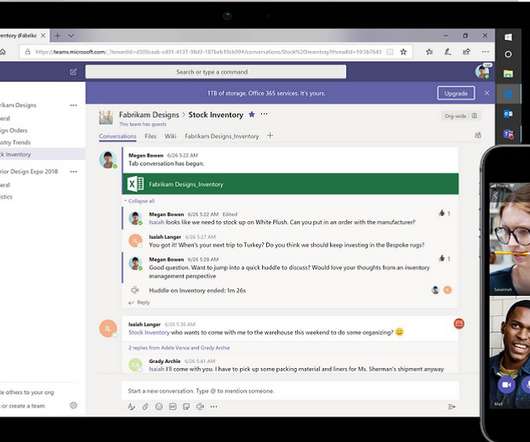
Data Breach Today
MAY 2, 2020
Fraudsters Look to Harvest Office 365 Credentials From At-Home Employees A recently uncovered phishing campaign is spoofing notifications from Microsoft's Teams collaboration platform in order to harvest Office 365 credentials from employees working from home offices because of the COVID-19 pandemic, according to research from Abnormal Security.

Data Protection Report
MAY 4, 2020
Following the example of many European countries, the French government plans to introduce a contact tracing app, known as “StopCovid”. The app is designed to be used by people once they leave the confinement of their homes with the aim of preventing the spread of COVID-19. StopCovid is being developed within the INRIA, the French national research institute for digital sciences and technologies.

The Guardian Data Protection
MAY 7, 2020
More protections needed before coronavirus app fully launched, says human rights committee Coronavirus – latest updates See all our coronavirus coverage The NHS contact-tracing app must not be rolled out across the UK until the government has increased privacy and data protections, an influential parliamentary committee has said, as rights groups warn that the current trial is unlawful under the data protection act.
Let's personalize your content