LA School District Accounts on Dark Web Before Attack
Data Breach Today
SEPTEMBER 7, 2022
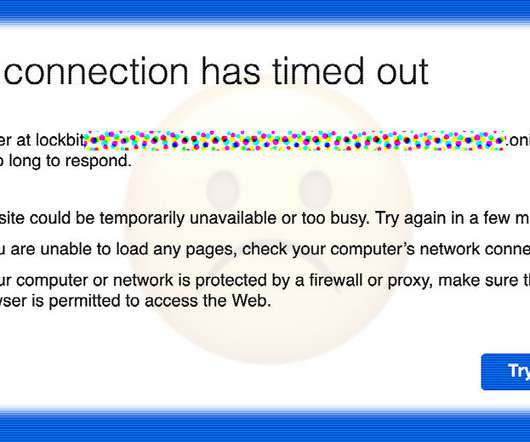
Hacked Accounts May Have Made District an Easy Ransomware Target The Labor Day weekend ransomware attack against Los Angeles Unified School District is drawing serious attention from the U.S. government, which has dispatched the FBI. The attack vector is unknown, but nearly two dozen compromised district accounts appeared on the Dark Web in the months leading up to the attack.









































Let's personalize your content