Hackers Claim Drug Data Theft as Reports Warn Health Sector
Data Breach Today
JUNE 6, 2022
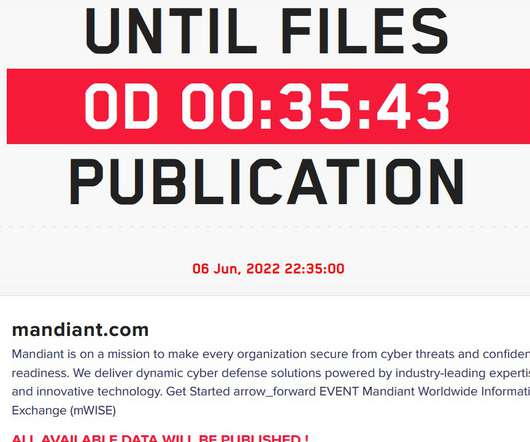
Pharma Maker Disputes Data Compromise Amid Reported Rise in Sector Attacks Novartis says no sensitive information was compromised in an alleged attack involving the drugmaker's data showing up for sale on the dark web. The incident comes as new reports warn of a surge in cyberattacks on healthcare sector entities and the return of Emotet malware.






































Let's personalize your content