Conti’s Ransomware Toll on the Healthcare Industry
Krebs on Security
APRIL 18, 2022
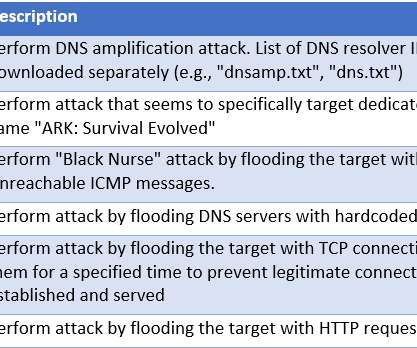
Conti — one of the most ruthless and successful Russian ransomware groups — publicly declared during the height of the COVID-19 pandemic that it would refrain from targeting healthcare providers. But new information confirms this pledge was always a lie, and that Conti has launched more than 200 attacks against hospitals and other healthcare facilities since first surfacing in 2018 under its earlier name, “ Ryuk.” On April 13, Microsoft said it executed a legal sneak atta









































Let's personalize your content