Hackers Gaining Power of Subpoena Via Fake “Emergency Data Requests”
Krebs on Security
MARCH 29, 2022
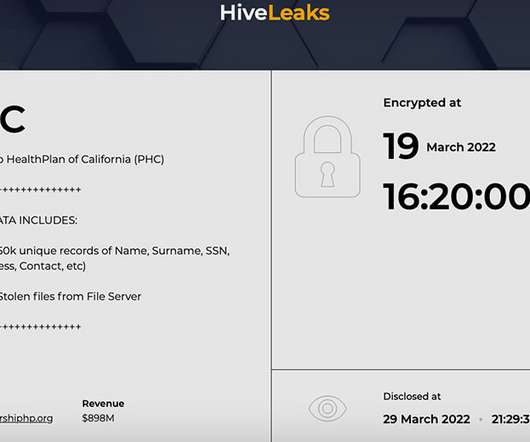
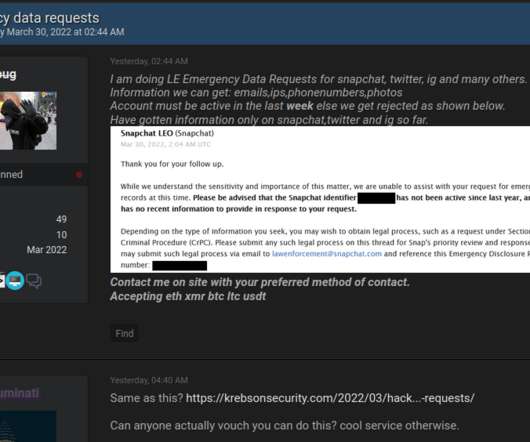
There is a terrifying and highly effective “method” that criminal hackers are now using to harvest sensitive customer data from Internet service providers, phone companies and social media firms. It involves compromising email accounts and websites tied to police departments and government agencies, and then sending unauthorized demands for subscriber data while claiming the information being requested can’t wait for a court order because it relates to an urgent matter of life







































Let's personalize your content