500M Avira Antivirus Users Introduced to Cryptomining
Krebs on Security
JANUARY 8, 2022
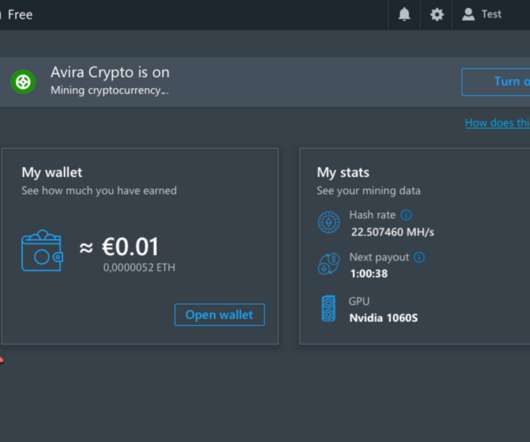
Many readers were surprised to learn recently that the popular Norton 360 antivirus suite now ships with a program which lets customers make money mining virtual currency. But Norton 360 isn’t alone in this dubious endeavor: Avira antivirus — which has built a base of 500 million users worldwide largely by making the product free — was recently bought by the same company that owns Norton 360 and is introducing its customers to a service called Avira Crypto.



































Let's personalize your content