Microsoft's Dream of Decentralized IDs Enters the Real World
WIRED Threat Level
MARCH 2, 2021
The company will launch a public preview of its identification platform this spring—and has already tested it at the UK's National Health Service.

WIRED Threat Level
MARCH 2, 2021
The company will launch a public preview of its identification platform this spring—and has already tested it at the UK's National Health Service.

erwin
MARCH 4, 2021
Modern data governance is a strategic, ongoing and collaborative practice that enables organizations to discover and track their data, understand what it means within a business context, and maximize its security, quality and value. It is the foundation for regulatory compliance and de-risking operations for competitive differentiation and growth. However, while digital transformation and other data-driven initiatives are desired outcomes, few organizations know what data they have or where it i
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Threatpost
MARCH 1, 2021
A snapshot of the 2020 mobile threat landscape reveals major shifts toward adware and threats to online banks.
Krebs on Security
MARCH 5, 2021
At least 30,000 organizations across the United States — including a significant number of small businesses, towns, cities and local governments — have over the past few days been hacked by an unusually aggressive Chinese cyber espionage unit that’s focused on stealing email from victim organizations, multiple sources tell KrebsOnSecurity.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
MARCH 1, 2021
Incidents Spotlight Growing COVID-19-Related Cyberthreats Two Indian vaccine makers and an Oxford University lab are reportedly among the latest targets of hackers apparently seeking to steal COVID-19 research data.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Thales Cloud Protection & Licensing
MARCH 1, 2021
Data Beyond Borders: The Schrems II Aftermath. divya. Tue, 03/02/2021 - 07:06. On July 16, 2020 the Court of Justice of the European Union issued the Schrems II decision in the case Data Protection Commission v. Facebook Ireland. That decision invalidates the European Commission’s adequacy decision for the EU-U.S. Privacy Shield Framework, on which more than 5,000 U.S. companies rely to conduct trans-Atlantic trade in compliance with EU data protection rules.
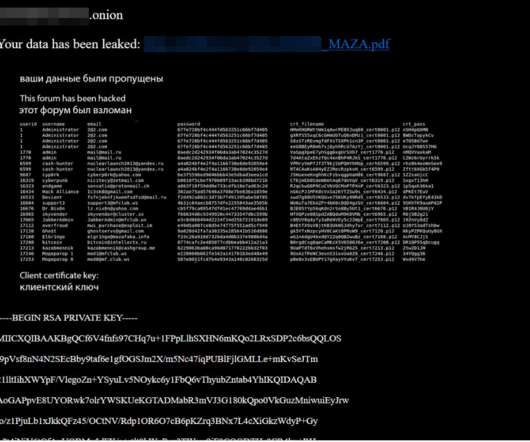
Krebs on Security
MARCH 4, 2021
Over the past few weeks, three of the longest running and most venerated Russian-language online forums serving thousands of experienced cybercriminals have been hacked. In two of the intrusions, the attackers made off with the forums’ user databases, including email and Internet addresses and hashed passwords. Members of all three forums are worried the incidents could serve as a virtual Rosetta Stone for connecting the real-life identities of the same users across multiple crime forums.

Data Breach Today
MARCH 1, 2021
Flaw Could Enable Access to Secret Encryption Key A critical authentication bypass vulnerability could enable hackers to remotely compromise programmable logic controllers made by industrial automation giant Rockwell Automation, according to the cybersecurity company Claroty. Rockwell has issued mitigation recommendations.

AIIM
MARCH 4, 2021
To succeed on the Digital Transformation journey, requires a strategy, planning, and the design of a better information ecosystem - what we refer to as Intelligent Information Management (IIM). The first step on this journey is to get all of your information into the information ecosystem. This is a practice called Capture. Let’s take a deeper look at this first step of digital transformation.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Schneier on Security
MARCH 1, 2021
Early in 2020, cyberspace attackers apparently working for the Russian government compromised a piece of widely used network management software made by a company called SolarWinds. The hack gave the attackers access to the computer networks of some 18,000 of SolarWinds’s customers, including US government agencies such as the Homeland Security Department and State Department, American nuclear research labs, government contractors, IT companies and nongovernmental agencies around the world.
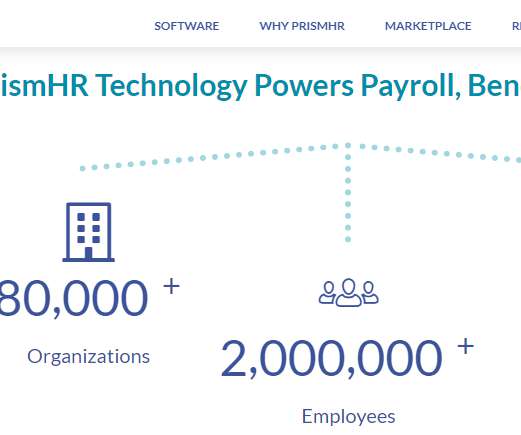
Krebs on Security
MARCH 2, 2021
PrismHR , a company that sells technology used by other firms to help more than 80,000 small businesses manage payroll, benefits, and human resources, has suffered what appears to be an ongoing ransomware attack that is disrupting many of its services. Hopkinton, Mass.-based PrismHR handles everything from payroll processing and human resources to health insurance and tax forms for hundreds of “professional employer organizations” (PEOs) that serve more than two million employees.

Data Breach Today
MARCH 3, 2021
Sophisticated Attackers Took the Time to Master a 20-Year-Old Product, FireEye Says Using a nearly 20-year-old file-transfer product: What could go wrong? Among the many lessons to be learned from the Accellion File Transfer Application mess is this: Attackers will devote substantial resources to reverse engineering hardware, software or a service if there's a financial upside.

WIRED Threat Level
FEBRUARY 28, 2021
The transparency group DDoSecrets says it will make the 70GB of passwords, private posts, and more available to researchers, journalists, and social scientists.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Troy Hunt
MARCH 1, 2021
I'm pleased to welcome the first new government onto Have I Been Pwned for 2021, Portugal. The Portuguese CSIRT, CERT.PT , now has full and free access to query their government domains across the entire scope of data in HIBP. This is now the 12th government onboarded to HIBP and I'm very happy to see the Portuguese join their counterparts in other corners of the world.

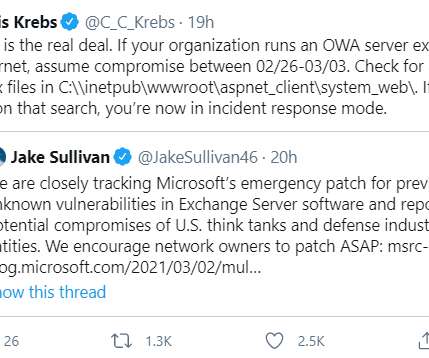
Krebs on Security
MARCH 2, 2021
Microsoft Corp. today released software updates to plug four security holes that attackers have been using to plunder email communications at companies that use its Exchange Server products. The company says all four flaws are being actively exploited as part of a complex attack chain deployed by a previously unidentified Chinese cyber espionage group.

Data Breach Today
MARCH 4, 2021
Microsoft, FireEye Find Additional Payloads Used During Supply Chain Attack Researchers with Microsoft and FireEye are disclosing additional malware used by the hacking group that targeted SolarWinds in December. These second-stage malware variants appear to have been deployed after organizations downloaded the "Sunburst" backdoor hidden in a software update.
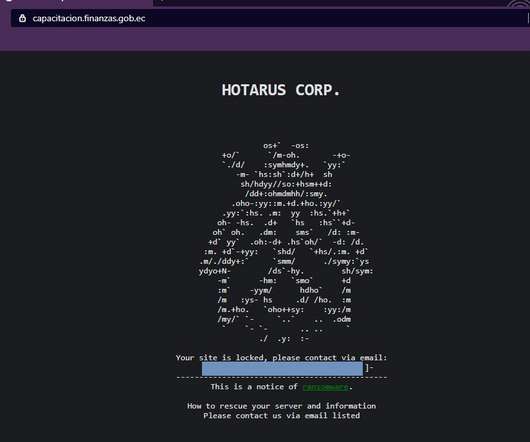
Security Affairs
FEBRUARY 27, 2021
‘Hotarus Corp’ Ransomware operators hacked Ecuador’s largest private bank, Banco Pichincha, and the country’s Ministry of Finance. ?A cybercrime group called ‘Hotarus Corp’ has breached the Ecuador’s largest private bank, Banco Pichincha, and the local Ministry of Finance (the Ministerio de Economía y Finanzas de Ecuador).

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Schneier on Security
MARCH 2, 2021
This is weird : Once an hour, infected Macs check a control server to see if there are any new commands the malware should run or binaries to execute. So far, however, researchers have yet to observe delivery of any payload on any of the infected 30,000 machines, leaving the malware’s ultimate goal unknown. The lack of a final payload suggests that the malware may spring into action once an unknown condition is met.

Hunton Privacy
MARCH 2, 2021
On March 2, 2021, Virginia’s Governor, Ralph Northam, signed the Consumer Data Protection Act into law without any further amendments. In addition to California, Virginia is now the second state to enact major privacy legislation of general applicability in the U.S. Read our previous blog post for an overview of the law and its requirements, which will take effect on January 1, 2023.

Data Breach Today
MARCH 2, 2021
Hackers Threatened to Leak Sensitive Data The cryptocurrency company Tether has refused to pay a ransom of 500 bitcoins ($24 million) after hackers threatened to leak sensitive data if the company failed to pay.

Security Affairs
MARCH 5, 2021
US managed service provider CompuCom was the victim of a cyberattack that partially disrupted its operations, experts believe it was a ransomware attack. US managed service provider CompuCom was the victim of a cyberattack that partially disrupted its services and some of its operations. Even if the company initially did not provide technical details about the attack, security experts speculated the involvement of ransomware due to the observed effects.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
MARCH 1, 2021
How's your 'Probiv'? How about customer service? Here's how Dark Web forums connect cybercriminals looking for talent with those looking for work -- and which skills are hot right now.
Threatpost
MARCH 5, 2021
A new variant of the Gafgyt botnet - that's actively targeting vulnerable D-Link and Internet of Things devices - is the first variant of the malware to rely on Tor communications, researchers say.

Data Breach Today
MARCH 4, 2021
Forecast Calls for Backdoored Email and Possibly Ransomware, Cryptominers One day after Microsoft disclosed four serious flaws in Microsoft Exchange email servers, attackers are going on a wide hunt for vulnerable machines, experts say. There's not only a risk of backdoored email accounts, but also ransomware and cryptominers.

Security Affairs
MARCH 3, 2021
Cybersecurity firm Qualys seems to have suffered a data breach, threat actors allegedly exploited zero-day flaw in their Accellion FTA server. Cybersecurity firm Qualys is the latest victim of a cyber attack, the company was likely hacked by threat actors that exploited a zero-day vulnerability in their Accellion FTA server. A couple of weeks ago, security experts from FireEye linked a series of cyber attacks against organizations running Accellion File Transfer Appliance (FTA) servers to the c

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

DXC Technology
MARCH 1, 2021
An emerging way to program, known as low-code application development, is transforming the way we create software. With this new approach, we’re creating applications faster and more flexibly than ever before. What’s more, this work is being done by teams where up to three-quarters of the team members can have no prior experience in developing […].

OpenText Information Management
MARCH 2, 2021
It’s never been easier to share your information and collaborate — and likewise, it has never been riskier, costlier, and more embarrassing to experience a data leak. These two competing realities create a real dilemma for IT: How do you maintain productivity and foster collaboration among a widely dispersed workforce while keeping control of your … The post Protecting your most valuable content appeared first on OpenText Blogs.

Data Breach Today
FEBRUARY 27, 2021
Critical Networks Within National Security Systems Should Implement Zero Trust The US National Security Agency has issued its zero trust guidance aimed at securing critical networks and sensitive data within key federal agencies. The NSA adds it is also assisting Defense Department customers with the zero trust implementations.
Let's personalize your content