Zoom Snooping: How Body Language Can Spill Your Password
Threatpost
NOVEMBER 5, 2020
Researchers figure out how to read what people are typing during a Zoom call using shoulder movements.

Threatpost
NOVEMBER 5, 2020
Researchers figure out how to read what people are typing during a Zoom call using shoulder movements.

WIRED Threat Level
NOVEMBER 1, 2020
Scammers are luring people into Google Docs in an attempt to get them to visit potentially malicious websites.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Governance
NOVEMBER 2, 2020
With 117 publicly reported security incidents, October 2020 is the leakiest month we’ve ever recorded. The good news is that those data breaches and cyber attacks accounted for just 18,407,479 breached records. However, it’s worth noting that, in very few incidents, the number of affected records is revealed – either because the organisation doesn’t know or because it’s not required to disclose that information.

Data Breach Today
NOVEMBER 5, 2020
Prosecutors Says Stolen Cryptocurrency Tied to Mysterious Digital Wallet The U.S. Justice Department is looking to seize more than $1 billion worth of bitcoin that investigators have linked to the notorious Silk Road darknet marketplace. The cryptocurrency was stored within a mysterious digital wallet that had been dormant for years, but the subject of much speculation.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Krebs on Security
NOVEMBER 4, 2020
Companies hit by ransomware often face a dual threat: Even if they avoid paying the ransom and can restore things from scratch, about half the time the attackers also threaten to release sensitive stolen data unless the victim pays for a promise to have the data deleted. Leaving aside the notion that victims might have any real expectation the attackers will actually destroy the stolen data, new research suggests a fair number of victims who do pay up may see some or all of the stolen data publi
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
NOVEMBER 1, 2020
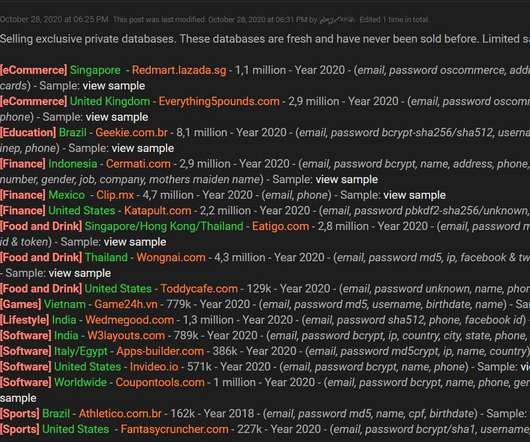
A threat actor is offering for sale account databases containing an aggregate total of 34 million user records stolen from 17 companies. A data breach broker is selling account databases containing a total of 34 million user records stolen from 17 companies. The threat actor is advertising the stolen data since October 28 on a hacker forum. Source Bleeping Computer.

Data Breach Today
NOVEMBER 2, 2020
Privacy Regulator in UK Cautions Organizations to Conduct Thorough Due Diligence Hotel giant Marriott has been hit with the second largest privacy fine in British history, after it failed to contain a massive, long-running data breach. But the final fine of $23.8 million was just 20% of the penalty initially proposed by the U.K.'s privacy watchdog, owing in part to COVID-19's ongoing impact.

Krebs on Security
NOVEMBER 3, 2020
Two young men from the eastern United States have been hit with identity theft and conspiracy charges for allegedly stealing bitcoin and social media accounts by tricking employees at wireless phone companies into giving away credentials needed to remotely access and modify customer account information. Prosecutors say Jordan K. Milleson , 21 of Timonium, Md. and 19-year-old Kingston, Pa. resident Kyell A.

AIIM
NOVEMBER 3, 2020
More and more records managers in state and local government operations tell me that their job is changing. In addition to stacks and stacks of scanned files, and a confluence of different types of electronic files, the inclusion of audio and video records are becoming more and more common. Indeed, many managers now must capture, store, and manage things like audio from 911 dispatch, police camera footage, and other documentary evidence that fall outside the typical scope of “records.”.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
NOVEMBER 1, 2020
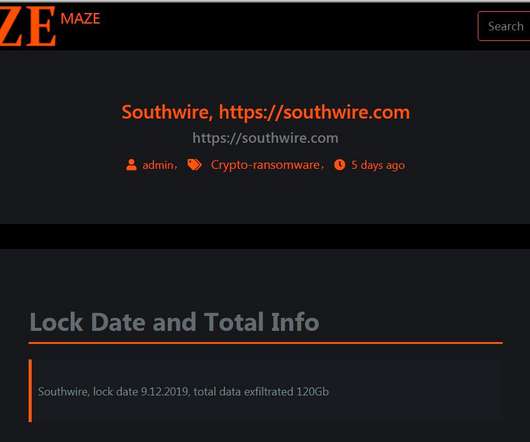
The Maze ransomware operators are shutting down their operations for more than one year the appeared on the threat landscape in May 2019. The Maze cybercrime gang is shutting down its operations, it was considered one of the most prominent and active ransomware crew since it began operating in May 2019. The gang was the first to introduce a double-extortion model in the cybercrime landscape at the end of 2019.
Data Breach Today
NOVEMBER 5, 2020
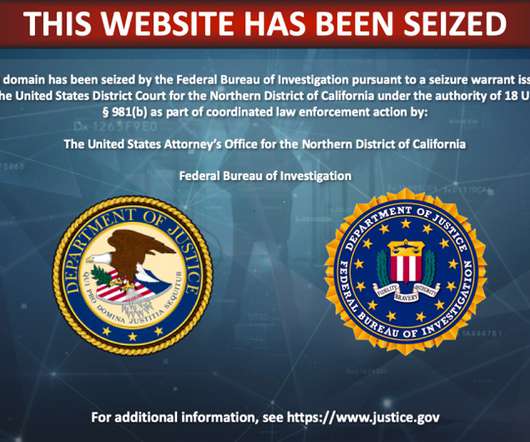
4 Domains Targeted US Citizens With Pro-Iranian Propaganda, Prosecutors Say The U.S. Justice Department has seized 27 website domains operated by Iran's Islamic Revolutionary Guard Corps to conduct a covert influence campaign targeting the U.S. and other citizens from around the world.
Schneier on Security
NOVEMBER 2, 2020
Google’s Project Zero has discovered and published a buffer overflow vulnerability in the Windows Kernel Cryptography Driver. The exploit doesn’t affect the cryptography, but allows attackers to escalate system privileges: Attackers were combining an exploit for it with a separate one targeting a recently fixed flaw in Chrome. The former allowed the latter to escape a security sandbox so the latter could execute code on vulnerable machines.
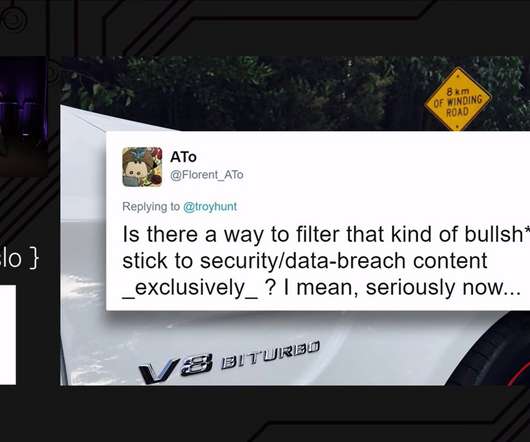
Troy Hunt
NOVEMBER 2, 2020
I've had this blog post in draft for quite some time now, adding little bits to it as the opportunity presented itself. In a essence, it boils down to this: people expressing their displeasure when I post about a topic they're not interested in then deciding to have a whinge that my timeline isn't tailored to their expectation of the things they'd like me to talk about.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
NOVEMBER 1, 2020
Japan’s Nuclear Regulation Authority (NRA) issued a warning of temporary suspension of its email systems, likely caused by a cyber attack. The Japan’s Nuclear Regulation Authority (NRA) temporarily suspended its email systems, the interruption is likely caused by a cyber attack. The agency published a warning on its website, it is asking people to contact it via phone or fax because it is unable to receive emails from the outside world. “From 17:00 on October 27, 2nd year of Reiwa, sending

Data Breach Today
NOVEMBER 3, 2020
Final Fines Set Precedent, Avoid Court Cases, Likely Reflect EU Penalty Benchmarks Large, recently levied privacy fines against the likes of British Airways, H&M and Marriott show regulators continuing to bring the EU's General Data Protection Regulation to bear after businesses get breached. But in the case of Marriott and BA, were the final fines steep enough?
Schneier on Security
NOVEMBER 4, 2020
Accuracy isn’t great, but that it can be done at all is impressive. Murtuza Jadiwala, a computer science professor heading the research project, said his team was able to identify the contents of texts by examining body movement of the participants. Specifically, they focused on the movement of their shoulders and arms to extrapolate the actions of their fingers as they typed.
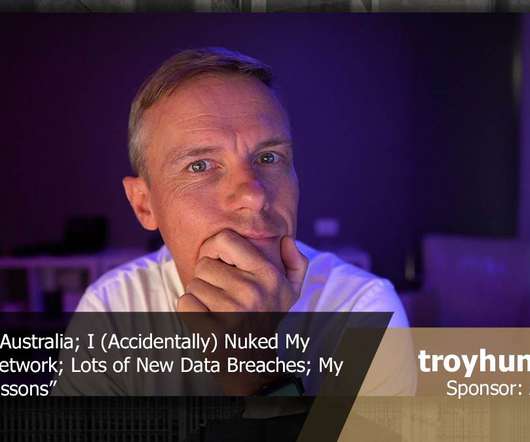
Troy Hunt
NOVEMBER 5, 2020
Alrighty, quickie intro before I rush off to hit the tennis court, catch up with old friends, onto the wake park before BBQ and, of course, ??. I'm doing a quick snapshot on how we're travelling down here COVID wise, I lament the demise (followed by resurrection) of my Ubiquiti network, there's a heap of new data breaches in HIBP and a bunch more insight into my guitar lessons (no, I'm not giving guitar lessons!

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Security Affairs
NOVEMBER 4, 2020
The source code for the KPot information stealer was put up for auction and the REvil ransomware operators want to acquire it. The authors of KPot information stealer have put its source code up for auction , and the REvil ransomware operators will likely be the only group to bid. #KPOT source code up for sale! pic.twitter.com/fJ3BwlaHsR — ??????

Data Breach Today
NOVEMBER 2, 2020
Cybereason Finds Kimsuky Group Using Fresh Spying Tools, Infrastructure Researchers with Cybereason have uncovered a fresh set of malicious tools tied to a North Korean-linked hacking group called Kimsuky, according to a recent analysis. This same advanced persistent threat group is also the subject of a new joint alert by CISA and the FBI.

Dark Reading
NOVEMBER 5, 2020
From meditation to the right mindset, seasoned vulnerability researchers give their advice on how to maximize bug bounty profits and avoid burnout.

Data Matters
NOVEMBER 4, 2020
The results are in, and California voters have approved the California Privacy Rights Act (CPRA) which was listed on the ballot as Proposition 24. The law, most of which does not go into effect until January 1, 2023, will substantially overhaul and amend the California Consumer Privacy Act (CCPA) which went into effect just this year, on January 1, 2020, with final regulations issued just a few months ago, on August 14, 2020.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Security Affairs
NOVEMBER 4, 2020
Yesterday almost $1 billion worth of cryptocurrency contained in a password-protected BitCoin wallet was moved to another wallet. Ahead of the 2020 Presidential election a mysterious transaction was noticed by cyber security experts and researchers. Someone has transferred almost $1 billion worth of cryptocurrency contained in a password-protected BitCoin wallet to another wallet.

Data Breach Today
NOVEMBER 5, 2020
Fraudsters Have Been Using SMTP Multipass Flaw for Business Email Compromise Schemes Attackers have been actively exploiting a flaw in Rackspace's hosted email service to send phishing emails, bearing legitimate and validated domain names, as part of business email compromise scams, warns IT security testing consultancy 7 Elements. Rackspace tells customers it plans to fix the problem soon.

Hunton Privacy
NOVEMBER 4, 2020
On November 3, 2020, California voters approved California Proposition 24, the California Privacy Rights Act (“CPRA”). As we previously reported , the CPRA significantly amends and expands upon the California Consumer Privacy Act of 2018, which became enforceable earlier this year. The new and modified obligations under the CPRA will become operative on January 1, 2023, and, with the exception of access requests, will apply to personal information collected by businesses on or after January 1, 2

WIRED Threat Level
NOVEMBER 4, 2020
A criminal complaint alleges that a West Virginia man disguised the plastic components as wall hangers and sold hundreds of them online.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Security Affairs
NOVEMBER 5, 2020
Apple released iOS 14.2 that addressed three zero-day vulnerabilities in its mobile OS that have been abused in attacks in the wild. Apple has addressed three iOS zero-day vulnerabilities actively exploited in attacks the wild and affecting iPhone, iPad, and iPod devices. The zero-day vulnerabilities have been fixed by the IT giant with the release of iOS 14.2 , iOS users are advised to install it immediately. “Apple is aware of reports that an exploit for this issue exists in the wild,&#

Data Breach Today
NOVEMBER 4, 2020
Time is Ripe for Interference, But US Projects Confidence After weeks of rising anxiety, Election Day proceeded in the U.S. with no public indications of interference. But experts say misinformation campaigns are still likely, and there's plenty of time for malicious activity as the vote tallying proceeds.

Threatpost
NOVEMBER 3, 2020
A threat actor is compromising telecommunications companies and targeted financial and professional consulting industries using an Oracle flaw.
Let's personalize your content