A Dangerous Year in America Enters Its Most Dangerous Month
WIRED Threat Level
OCTOBER 5, 2020
Seven distinct factors between now and the election threaten to combine, compound, and reinforce each other in unpredictable ways.

WIRED Threat Level
OCTOBER 5, 2020
Seven distinct factors between now and the election threaten to combine, compound, and reinforce each other in unpredictable ways.

IT Governance
OCTOBER 5, 2020
Are you trying to figure out the best way to protect your organisation from cyber attacks and data breaches? It can be tricky to know where to begin, which is why our Cyber Security Risk Scorecard contains a simple guide to help you secure your systems. We’ve run through some of the essential steps in this blog, or download the full, free checklist from our website.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
OCTOBER 5, 2020
A new initiative will run throughout the month of October, invites the general public to play cybersecurity games (and win fabulous prizes).

Data Breach Today
OCTOBER 5, 2020
Employee Surveillance Violations Trigger Germany's Biggest Privacy Fine to Date Privacy regulators in Germany have slammed clothing retailer H&M with a $41 million fine for collecting and retaining private employee data in violation of the EU's General Data Protection Regulation. H&M has apologized, instituted changes and promised to financially compensate employees.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Krebs on Security
OCTOBER 9, 2020
A week ago, KrebsOnSecurity broke the news that someone was attempting to disrupt the Trickbot botnet , a malware crime machine that has infected millions of computers and is often used to spread ransomware. A new report Friday says the coordinated attack was part of an operation carried out by the U.S. military’s Cyber Command. Image: Shuttstock.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
OCTOBER 6, 2020
Digitally Transforming IS the Future. Most organizations and departments have a mandate to continuously improve operations. A conventional change agenda involves better tools and technology, better behaviors, and better processes, all focused on generating better efficiencies and improved productivity - a transition called Digital Transformation. Ultimately, AIIM believes this Digital Transformation extends beyond conventional change.

Data Breach Today
OCTOBER 5, 2020
In an exclusive interview, Roger Severino, director of the HHS Office for Civil Rights, which enforces HIPAA, spells out critical steps healthcare organizations must take to safeguard patient information and ensure patient safety in light of the surge in ransomware and other hacking incidents.

Krebs on Security
OCTOBER 7, 2020
September featured two stories on a phony tech investor named John Bernard , a pseudonym used by a convicted thief named John Clifton Davies who’s fleeced dozens of technology companies out of an estimated $30 million with the promise of lucrative investments. Those stories prompted a flood of tips from Davies’ victims that paint a much clearer picture of this serial con man and his cohorts, including allegations of hacking, smuggling, bank fraud and murder.

erwin
OCTOBER 8, 2020
More and more companies are looking at cloud migration. Migrating legacy data to public, private or hybrid clouds provide creative and sustainable ways for organizations to increase their speed to insights for digital transformation, modernize and scale their processing and storage capabilities, better manage and reduce costs, encourage remote collaboration, and enhance security, support and disaster recovery.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
OCTOBER 5, 2020
Threat actors have hacked at least three Swiss universities, including the University of Basel and managed to drain employee salary transfers. Threat actors have managed to steal employee salary payments at several Swiss universities, including the University of Basel. “According to our information, several universities in Switzerland have been affected,” explained Martina Weiss, Secretary General of the Rectors’ Conference of the Swiss Universities.

Data Breach Today
OCTOBER 3, 2020
Researchers Note Similarities to Sekhmet Crypto-Locking Malware Security researchers with Appgate are warning about a recently uncovered ransomware variant called Egregor that appears to have infected about a dozen organizations worldwide over the past several months. The gang behind this crypto-locking malware is threatening to release data if victims don't pay.

National Archives Records Express
OCTOBER 5, 2020
Last week, our office released two NARA Bulletins for Federal agencies. The first, NARA Bulletin 2020-01 , is the guidance answering common questions and providing clarifications to the OMB/NARA Memorandum M-19-21 : Transition to Electronic Records. This Bulletin is the additional guidance required by the Memorandum. . We have received many questions from agencies, including general questions, exception process questions, records storage facility questions, and scheduling and transfer questions
Schneier on Security
OCTOBER 5, 2020
Interesting usability study: “ More Than Just Good Passwords? A Study on Usability and Security Perceptions of Risk-based Authentication “: Abstract : Risk-based Authentication (RBA) is an adaptive security measure to strengthen password-based authentication. RBA monitors additional features during login, and when observed feature values differ significantly from previously seen ones, users have to provide additional authentication factors such as a verification code.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
OCTOBER 3, 2020
University Hospital New Jersey paid a $670,000 ransom this month to prevent the leak of 240 GB of stolen data, including patient information. The University Hospital New Jersey (UHNJ) in Newark (New Jersey) has finally paid a $670,000 ransom to prevent the publishing of 240 GB of stolen data, including patient info. In September, systems at the University Hospital New Jersey (UHNJ) were encrypted with the SunCrypt ransomware , threat actors also stolen documents from the institution and leaked

Data Breach Today
OCTOBER 7, 2020
Yet Another Report Warns of Nation-State Influence Operations In the latest in a series of election security reports from government agencies, the U.S. Department of Homeland Security says Russia poses the most serious nation-state disruption threat to the U.S. presidential election, with China and Iran also posing threats.

Threatpost
OCTOBER 9, 2020
Ethical hackers so far have earned nearly $300K in payouts from the Apple bug-bounty program for discovering 55 bugs, 11 of them critical, during a three-month hack.
Schneier on Security
OCTOBER 6, 2020
Previously I have written about the Swedish-owned Swiss-based cryptographic hardware company: Crypto AG. It was a CIA-owned Cold War operation for decades. Today it is called Crypto International , still based in Switzerland but owned by a Swedish company. It’s back in the news : Late last week, Swedish Foreign Minister Ann Linde said she had canceled a meeting with her Swiss counterpart Ignazio Cassis slated for this month after Switzerland placed an export ban on Crypto International , a

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Security Affairs
OCTOBER 4, 2020
Visa revealed that two unnamed North American hospitality merchants have been infected with some strains of point-of-sale (POS) malware. US payments processor Visa revealed that two North American hospitality merchants have been hacked, threat actors infected the systems of the two unnamed organizations with some strains of point-of-sale (POS) malware.
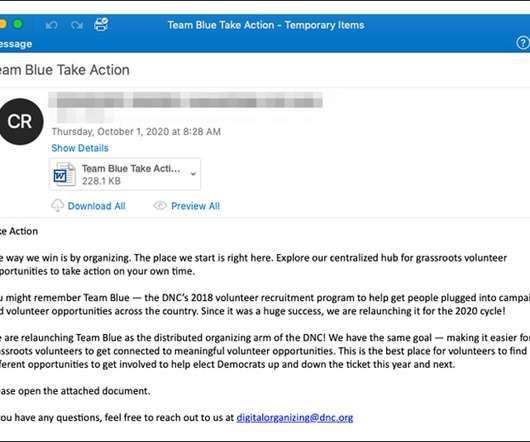
Data Breach Today
OCTOBER 5, 2020
Proofpoint and KnowBe4 Spot Malicious Messages Disguised as Political Announcements Security researchers are warning of a fresh wave of phishing emails with election-related lures that are designed to get users to click, opening the door to spreading the Emotet botnet or harvesting users' credentials.

Threatpost
OCTOBER 8, 2020
Two flaws in Microsoft's cloud-based Azure App Services could have allowed server-side forgery request (SSFR) and remote code-execution attacks.

OpenText Information Management
OCTOBER 5, 2020
It’s no secret that today’s global supply chain is more complex than ever. It has become a digital ecosystem of suppliers, logistics companies, customers and other value chain partners that stretch across the globe. The supply chain relies on the synchronized movement of thousands of interrelated parts to meet growing customer demand for better, more … The post What is a connected supply chain?

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Security Affairs
OCTOBER 5, 2020
Security researchers provided technical details about an IoT botnet dubbed Ttint that has been exploiting two zero-days in Tenda routers. Security researchers at Netlab, the network security division Qihoo 360, have published a report that details an IoT botnet dubbed Ttint. The experts are monitoring the Mirai-based botnet since November 2019 and observed it exploiting two Tenda router 0-day vulnerabilities to spread a Remote Access Trojan (RAT).
Data Breach Today
OCTOBER 7, 2020
Botnet Called 'One of the Most Prevalent Ongoing Threats' The U.S. Cybersecurity and Infrastructure Security Agency is warning about a recent spike in Emotet botnet attacks - designed to spread other malware - that are targeting state and local government agencies.

National Archives Records Express
OCTOBER 9, 2020
Every four years, the Federal Government moves into transition mode. No matter the outcome of the Presidential election, the Government enters a time of transition for senior staff across agencies. The Partnership for Public Service (PPS) Center for Presidential Transition produced a report last year highlighting the need for effective pre-election planning and preparation for significant turnover among the highest-level Government positions. .

OpenText Information Management
OCTOBER 7, 2020
The COVID-19 pandemic has wrought havoc on clinical trials, with thousands being suspended or stopped due to difficulties in continuing under lockdown condition. Research suggests that 80% of clinical research participants indicated that they were unwilling to visit the trial site for study appointments. The clinical trials sector has had to pivot quickly.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Security Affairs
OCTOBER 6, 2020
The CISA agency is warning of a surge in Emotet attacks targeting multiple state and local governments in the US since August. The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August. During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.

Data Breach Today
OCTOBER 9, 2020
The latest edition of the ISMG Security Report analyzes why clothing retailer H&M was hit with a hefty fine for violating the EU's General Data Protection Rule. Also featured: The coming of age of digital identities; deputy CSO at Mastercard on top priorities for 2021.

IT Governance
OCTOBER 7, 2020
In our latest round-up of phishing scams, we look at how and why the rise in remote working has made us more susceptible to fraud. We also explain why you should be careful if you receive an email telling you to complete a staff awareness training course, and discuss a new SMS scam that offers you an iPhone 12. Working from home increases the threat of phishing.
Let's personalize your content