My (data) fine is enormous
Data Protector
OCTOBER 2, 2020
I am he as you are he as you are me and we are all together See how they stun the world and my mum, see how they fine I'm crying Sitting in the courthouse, waiting for the man to come Covid mask and goggles, stupid bloody Tuesday Man, you been a naughty boy, you set your cookies wrong I am the bad man, I spammed some good men My fine is enormous, goo goo g'joob Mister lead prosecutor sitting Pretty little lawyers in a row See how they drone “he should have known,” see how they fine I'm crying, I
 156
156  156
156 








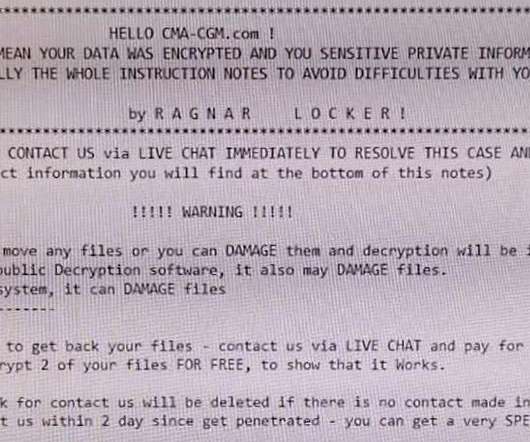


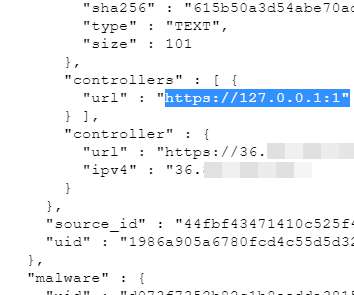





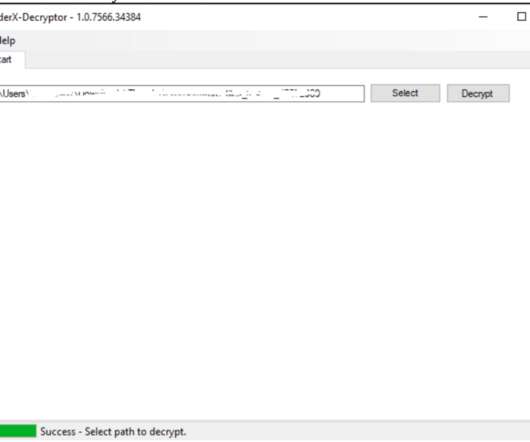


















Let's personalize your content