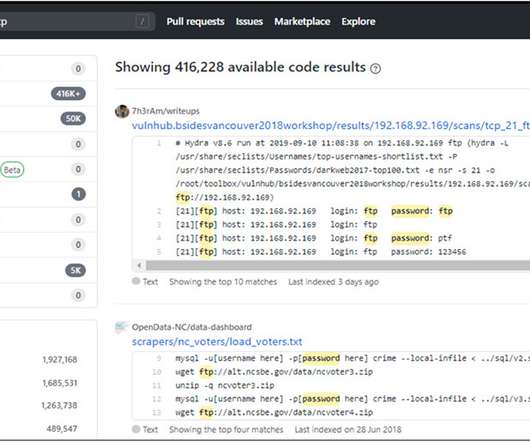
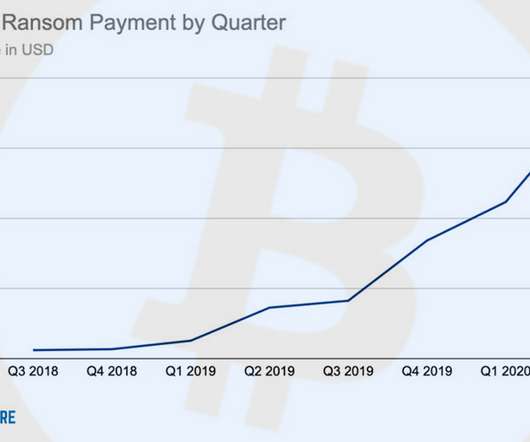
So You Want to Build a Vulnerability Disclosure Program?
Data Breach Today
AUGUST 20, 2020
Bug Bounty Pioneer Katie Moussouris on Challenges, Sustainability, Election Security To build a successful vulnerability disclosure program, avoid thinking of it as quick-fix "bug bounty Botox," and instead focus on building positive relationships with the security community, hiring top-notch talent and "building a sustainable ecosystem," says Luta Security's Katie Moussouris.








































Let's personalize your content