Good Cyber Hygiene in a Post-Pandemic World Starts with Us
Dark Reading
JUNE 26, 2020
Three ways that security teams can improve processes and collaboration, all while creating the common ground needed to sustain them.

Dark Reading
JUNE 26, 2020
Three ways that security teams can improve processes and collaboration, all while creating the common ground needed to sustain them.

Dark Reading
JUNE 24, 2020
Sensitivity of customer information and time-to-detection determine financial blowback of cybersecurity breaches.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
JUNE 23, 2020
Why embracing, not fighting, decentralization will pave the way to smoother cloud migrations.
Krebs on Security
JUNE 21, 2020
Hundreds of thousands of potentially sensitive files from police departments across the United States were leaked online last week. The collection, dubbed “ BlueLeaks ” and made searchable online, stems from a security breach at a Texas web design and hosting company that maintains a number of state law enforcement data-sharing portals. The collection — nearly 270 gigabytes in total — is the latest release from Distributed Denial of Secrets (DDoSecrets), an alternative to

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
JUNE 25, 2020
Superseding Indictment Expands Scope of Case, But Doesn't Add Charges The U.S Department of Justice unsealed a superseding indictment against WikiLeaks founder Julian Assange that expands the scope of the government's case against him. Federal prosecutors now allege that Assange conspired with the Anonymous and LulzSec groups to obtain classified information to publish.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

The Guardian Data Protection
JUNE 23, 2020
Local health chiefs say real-time information is crucial to monitor spread of disease Coronavirus – latest updates See all our coronavirus coverage Local outbreaks of Covid-19 could grow undetected because the government is failing to share crucial testing data, council leaders and scientists have warned. More than a month after being promised full details of who has caught the disease in their areas, local health chiefs are still desperately lobbying the government’s testing chief, Lady Harding

AIIM
JUNE 23, 2020
There may be no other industry that could benefit more from automation than the mortgage banking industry. This industry is full of time-consuming, error-prone, and paper and labor-intensive processes, all perfectly-suited for automation. And with huge volumes of loans being generated each year (nearly 5 million new consumer mortgages alone), it may soon become impossible to move forward without the use of automation.

Data Breach Today
JUNE 23, 2020
New Risks Could Emerge as More Practices Reopen Four recent cybersecurity incidents that may have involved ransomware demonstrate the ongoing threats facing the sector during the COVID-19 pandemic. They also serve as a warning that extra watchfulness is needed as physicians reopen their clinics.

Security Affairs
JUNE 26, 2020
A man accused to have developed distributed denial of service (DDoS) botnets based on the Mirai botnet was sentenced to 13 months in federal prison. Kenneth Currin Schuchman, 22, of Vancouver, Washington, was sentenced to 13 months in federal prison because it has developed distributed denial of service (DDoS) botnets based on the source code of Mirai botnet.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

erwin
JUNE 26, 2020
If you’re serious about a data-driven strategy , you’re going to need a data catalog. Organizations need a data catalog because it enables them to create a seamless way for employees to access and consume data and business assets in an organized manner. Given the value this sort of data-driven insight can provide, the reason organizations need a data catalog should become clearer.

Micro Focus
JUNE 25, 2020
I need to change – IT needs to change Rapid and large-scale IT change is a very costly exercise. Worse still, it is fraught with risk, the IT world beset with uncomfortable stories of failed transformational programs. CIOs can ill-afford such risk. By reusing valuable, trusted core applications and data, a smarter approach is available. View Article.

Data Breach Today
JUNE 26, 2020
Senior Care Facility Operator Describes Investigation Why are some breach notifications delayed for months? This week, a company that operates senior care facilities in North Carolina and South Carolina issued a statement offering a step-by-step explanation.
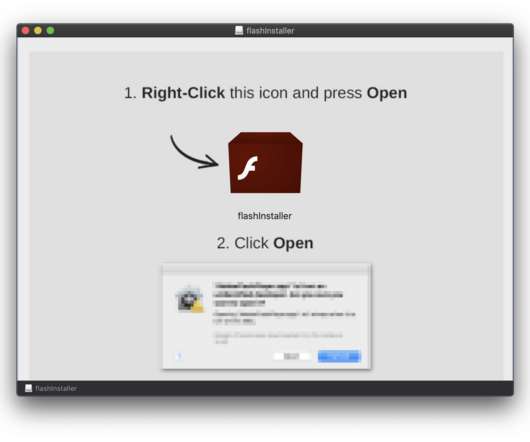
Security Affairs
JUNE 21, 2020
Shlayer Mac malware is back, the Mac threat is now spreading through new black SEO operations. Researchers spotted a new version of the Shlayer Mac malware that is spreading via poisoned Google search results. Researchers at security firm Intego observed the new variant being spread masqueraded as a fake Adobe Flash Player installer (.DMG disk image) and implementing fresh advanced evasion capabilities. “The new malware tricks victims into bypassing Apple’s built-in macOS security protecti

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

IBM Big Data Hub
JUNE 23, 2020
When planning for a day of business, how do you calculate the numerous factors that may affect your bottom-line revenue? For Serco, a company which operates a bike-sharing service throughout London, the answer was in their data.

IT Governance
JUNE 25, 2020
England’s coronavirus lockdown will all but end on 4 July, with the government allowing pubs, restaurants, cinemas, museums and hotels to reopen. The decision comes after steady progress in mitigating the spread of COVID-19 and the partial reopening of other sectors over the previous six weeks. But it doesn’t exactly signal a return to business as usual, as heavy restrictions will still be in place.

Data Breach Today
JUNE 22, 2020
Campaign Targets Unpatched Software and Weak Authentication, Defenders Warn Hackers wielding Nefilim ransomware are targeting unpatched or poorly secured Citrix remote-access technology, then stealing data, unleashing crypto-locking malware and threatening to dump data to try to force payment, New Zealand's national computer emergency response team warns.
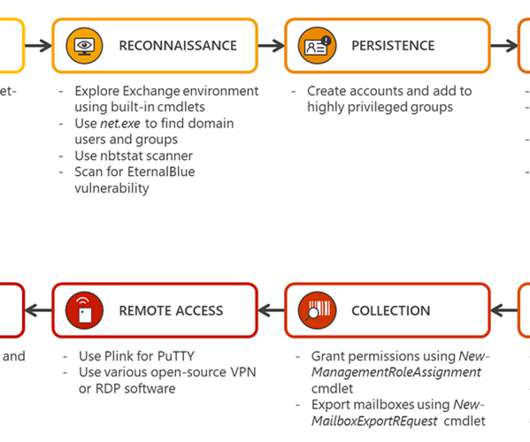
Security Affairs
JUNE 25, 2020
Microsoft researchers are warning of attacks against Exchange servers and published guidance on how to defend them. Microsoft’s Defender ATP Research Team released guidance on how to defend against attacks targeting Exchange servers with the use of behavior-based detection. Microsoft researchers analyzed multiple campaigns targeting Exchange servers in early April which showed how the malicious actors deploying web shells them.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

WIRED Threat Level
JUNE 22, 2020
The so-called BlueLeaks collection includes internal memos, financial records, and more from over 200 state, local, and federal agencies.
IBM Big Data Hub
JUNE 23, 2020
Turning raw data into improved business performance is a multilayered problem, but it doesn’t have to be complicated. To make things simpler, let’s start at the end and work backwards. Ultimately, the goal is to make better decisions during the execution of a business process. This can be as simple as not making a customer repeat their address after a hand-off in a call center, or as complex as re-planning an entire network of flights in response to a storm.

Data Breach Today
JUNE 24, 2020
How to Avoid Addressing Problems 'Too Far Downstream' Greg van der Gaast, head of information security at the University of Salford in the United Kingdom, has strong opinions on why some security investments aren't reaping maximum benefits. "We are addressing problems too far downstream," he says.
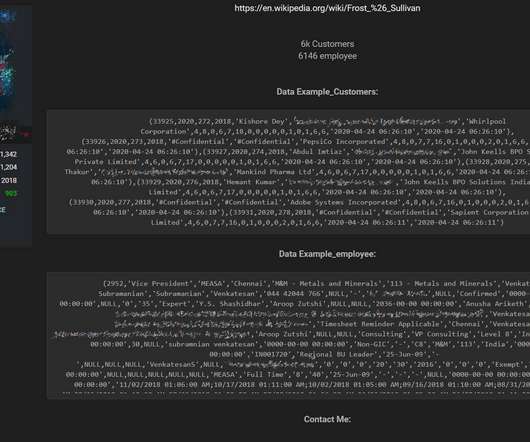
Security Affairs
JUNE 24, 2020
U.S. business consulting firm Frost & Sullivan suffered a data breach, a threat actor is offering for sale its databases on a hacker forum. U.S. firm Frost & Sullivan suffered a data breach, data from an unsecured backup that were exposed on the Internet was sold by a threat actor on a hacker forum. Frost & Sullivan is a business consulting firm involved in market research and analysis, growth strategy consulting, and corporate training across multiple industries.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Threatpost
JUNE 25, 2020
Several high-severity flaws in Nvidia's GPU display drivers for Windows users could lead to code-execution, DoS and more.

IBM Big Data Hub
JUNE 25, 2020
As communities and businesses worldwide look to understand the economic impact of COVID-19 and prepare for an eventual recovery, the biggest test of decision-making will be the data that will inform the business decisions. Was it trusted? Was it timely? Was it enough? To date, there are many efforts to release COVID-19 dashboards that can give us a hint on what to do next.

Data Breach Today
JUNE 24, 2020
Researchers: Cybercrime Group, Formerly Known for Dridex, Is Not Exfiltrating Data The Evil Corp cybercrime group, originally known for the Dridex banking Trojan, is now using new ransomware called WastedLocker, demanding ransom payments of $500,000 to $1 million, according to security researchers at NCC Group's Fox-IT.

Security Affairs
JUNE 26, 2020
German Police have arrested 32 individuals and detained 11 after a series of raids targeting users of an illegal underground economy forum. According to prosecutors in Frankfurt and Bamberg, the German Police have arrested 32 individuals and detained 11 after a series of raids targeting users of the “ crimenetwork.co ” illegal underground economy forum.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Hunton Privacy
JUNE 24, 2020
On June 11, 2020, the Centre for Information Policy Leadership (“CIPL”) at Hunton Andrews Kurth submitted its response (the “Response”) to the European Commission’s consultation regarding its white paper on “a European Approach to Excellence and Trust” on artificial intelligence (the “White Paper”). As we previously reported , the Commission’s White Paper outlines its proposed steps toward building an “ecosystem of excellence” to support the development and adoption of Artificial Intelligence (“

Threatpost
JUNE 23, 2020
Remote work is opening up new insider threats - whether it's negligence or malicious employees - and companies are scrambling to stay on top of these unprecedented risks.

Data Breach Today
JUNE 24, 2020
Symantec: Attackers Use Weaponized Cobalt Strike to Spread Malware The Sodinokibi ransomware gang is targeting point-of-sale payment device software after infecting networks with its crypto-locking malware, according to Symantec.
Let's personalize your content