7 Ways COVID-19 Has Changed Our Online Lives
Dark Reading
APRIL 14, 2020
The pandemic has driven more of our personal and work lives online - and for the bad guys, business is booming. Here's how you can protect yourself.

Dark Reading
APRIL 14, 2020
The pandemic has driven more of our personal and work lives online - and for the bad guys, business is booming. Here's how you can protect yourself.

Data Breach Today
APRIL 17, 2020
Prices for Kits Soar; Ads Proliferate on Dark Net Markets Ads for phishing kits doubled last year on underground forums and dark net markets, with prices skyrocketing over 149 percent - an apparent indicator of strong demand, according to security firm Group-IB.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
APRIL 15, 2020
The more things change, the more they stay the same. Much of the world is still behind on the basics.

Troy Hunt
APRIL 16, 2020
Hot on the heels of onboarding the USA government to Have I Been Pwned last month , I'm very happy to welcome another national government - Iceland! As of today, Iceland's National Computer Security Incident Response Team ( CERT-IS ), now has access to the full gamut of their gov domains for both on-demand querying and ongoing monitoring. As with the USA and Iceland, I expect to continue onboarding additional governments over the course of 2020 and expanding their access to meaningful data about

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
APRIL 14, 2020
Study Shows Fingerprints Made With 3D Printer Can Fool Sensors, But Process Is Difficult Fake fingerprints created with a 3D printer can bypass biometric scanners to unlock smartphones, laptops and other devices under certain circumstances, according to a study from a Cisco Talos.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
APRIL 17, 2020
Suspected Arson Attacks on Transmitter Masts Disrupt Emergency Services As countries pursue national 5G rollouts, an unwanted security challenge has intensified: Some extremists have been vandalizing or even firebombing transmitter masts, driven by conspiracy theories suggesting not only that 5G poses a public health risk, but that it also helps cause COVID-19.
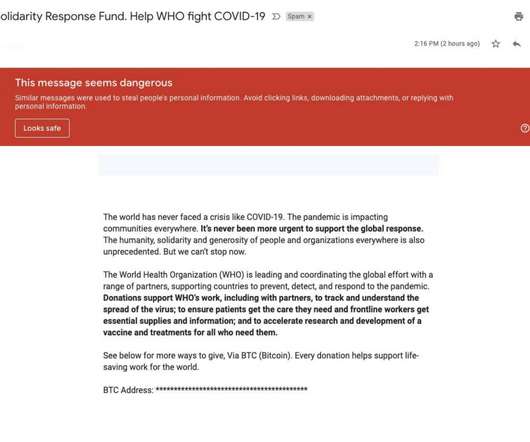
Security Affairs
APRIL 17, 2020
Google says that the Gmail malware scanners have blocked around 18 million phishing and malware emails using COVID-19 lures in just one week. Google announced that its anti-malware solutions implemented to defend its Gmail users have blocked around 18 million phishing and malware emails using COVID-19 lures within the last seven days. The IT giant also announced to have blocked more than 240 million spam messages related to the ongoing COVID-19 pandemic.

Thales Cloud Protection & Licensing
APRIL 16, 2020
The drastic changes we’re experiencing in our personal and professional lives would have been impossible to imagine just a year ago when we shared this blog about CEOs becoming more actively involved in data security conversations in the boardroom. Now, our new reality demands these questions are asked and answered by C-suite executives who must be certain about data security in uncertain times.

Data Breach Today
APRIL 14, 2020
Hank Thomas of Strategic Cyber Ventures on How the Industry Is Poised to Emerge From Crisis Before the COVID-19 pandemic, venture capitalist Hank Thomas helped launch SCVX, a cybersecurity-focused special purpose acquisition company. Post-pandemic, Thomas sees a bright future in filling what he sees as the market need for a scalable, integrated platform.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Schneier on Security
APRIL 17, 2020
It has produced several reports outlining what's wrong and what needs to be fixed. It's not fixing them : GAO looked at three DoD-designed initiatives to see whether the Pentagon is following through on its own goals. In a majority of cases, DoD has not completed the cybersecurity training and awareness tasks it set out to. The status of various efforts is simply unknown because no one has tracked their progress.
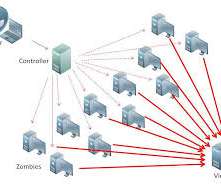
Security Affairs
APRIL 13, 2020
Dutch authorities have taken down 15 DDoS-for-hire services in a week, this is another success of law enforcement in the fight against cybercrime. An operation conducted by Dutch authorities last week has shut down 15 DDoS-for-hire services (aka DDoS booters or DDoS stressor), states a press release published by Dutch police. The operation was conducted with the support of Europol, Interpol, and the FBI along with web hosting providers and domain registrars.

Threatpost
APRIL 13, 2020
The Grandoreiro banking malware uses remote overlay and a fake Chrome browser plugin to steal from banking customers.

The Last Watchdog
APRIL 13, 2020
We’ve come to rely on our smartphones to live out our digital lives, both professionally and personally. When it comes to securing mobile computing devices, the big challenge businesses have long grappled with is how to protect company assets while at the same time respecting an individual’s privacy. Reacting to the BYOD craze , mobile security frameworks have veered from one partially effective approach to the next over the past decade.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Breach Today
APRIL 11, 2020
Ukrainian Man Behind the Actual Hacking Remains at Large The U.S. SEC has settled charges against two traders who were accused of profiting from the hacking of an EDGAR server in 2016. The Ukrainian man who allegedly hacked the system by bypassing its authentication control remains at large.

Krebs on Security
APRIL 15, 2020
The Coronavirus has prompted thousands of information security professionals to volunteer their skills in upstart collaborative efforts aimed at frustrating cybercriminals who are seeking to exploit the crisis for financial gain. Whether it’s helping hospitals avoid becoming the next ransomware victim or kneecapping new COVID-19-themed scam websites, these nascent partnerships may well end up saving lives.

AIIM
APRIL 16, 2020
Thanks to the internet and the connected world we live in, working remotely is increasing in popularity for a good reason ! The benefits of working from home have been good for both organization and their employees. On the one hand, organizations can hire talent despite the geographical issue and provide a flexible work schedule, minimized exposure to germs, and so on!

Security Affairs
APRIL 13, 2020
Zoom accounts are flooding the dark web, over 500 hundred thousand Zoom accounts are being sold on hacker forums. Over 500 hundred thousand Zoom accounts are available for sale on the dark web and hacker forums. Sellers are advertising them for.0020 cents each, in some cases they are offered for free. The huge trove of account credentials was not stolen by Zoom, instead, it appears the result of credential stuffing attacks that leverage records from third-party data breaches.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Data Breach Today
APRIL 13, 2020
Officials Say Usernames and Passwords Stolen San Francisco International Airport has disclosed that hackers stole usernames and passwords from two of its websites in March.

Krebs on Security
APRIL 14, 2020
Microsoft today released updates to fix 113 security vulnerabilities in its various Windows operating systems and related software. Those include at least three flaws that are actively being exploited, as well as two others which were publicly detailed prior to today, potentially giving attackers a head start in figuring out how to exploit the bugs.

The Guardian Data Protection
APRIL 13, 2020
Exclusive: draft plans for contact-tracing app said device IDs could be used to identify users Coronavirus – latest updates See all our coronavirus coverage A draft government memo explaining how the NHS contact-tracing app could stem the spread of the coronavirus said ministers might be given the ability to order “de-anonymisation” to identify people from their smartphones, the Guardian can reveal.
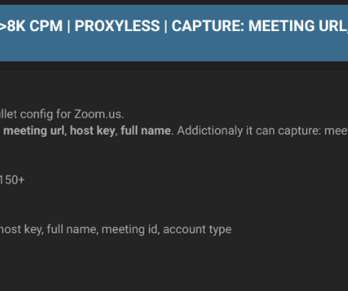
Security Affairs
APRIL 12, 2020
Security researchers discovered an archive available on a dark web forum that includes thousands of compromised Zoom credentials. Researchers discovered a database available on an underground forum in the dark web that contained more than 2,300 compromised Zoom credentials. Some of the records also included meeting IDs, names and host keys. The archive included credentials for Zoom accounts belonging to organizations in various industries, including banking, consultancy, healthcare software comp

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
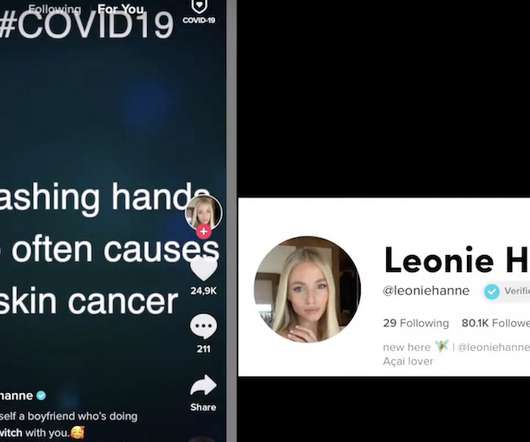
Data Breach Today
APRIL 15, 2020
Video-Sharing Service Does Not Always Use TLS/SSL Encryption TikTok, a video-sharing service, has been delivering video and other media without TLS/SSL encryption, which means it may be possible for someone to tamper with content, researchers say. That could be especially damaging in the current pandemic environment, where misinformation and confusion abounds.

AIIM
APRIL 17, 2020
There are a few different scenarios for auditing your data. Audits can be performed to assess data quality, identify data liabilities, ensure data privacy, uncover data leaks, and so on. Information governance audits, in particular, are used to ensure compliance with relevant information governance policies and procedures. On this episode of the AIIM on Air podcast , your host Kevin Craine explores Information Governance Audits with AIIM member Andrew du Fresne.
erwin
APRIL 15, 2020
Hello from my home office! I hope you and your family are staying safe, practicing social distancing, and of course, washing your hands. These are indeed strange days. During this coronavirus emergency, we are all being deluged by data from politicians, government agencies, news outlets, social media and websites, including valid facts but also opinions and rumors.

Security Affairs
APRIL 11, 2020
San Francisco International Airport (SFO) disclosed a data breach, its websites SFOConnect.com and SFOConstruction.com were hacked last month. In March hackers compromised two websites of San Francisco International Airport (SFO) and now it disclosed a data breach. SFO is a major gateway to Europe and Asia, it serves 45 international carriers. The attackers may have gained access to some users’ login credentials after deploying malware on both websites.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Data Breach Today
APRIL 15, 2020
More Advanced Cybercrime Services Help Hackers Boost Illicit Earnings Many criminals are continuing to tap cybercrime platforms and services to make it easier to earn an illicit paycheck, sometimes by combining tools, such as Emotet, Ryuk and TrickBot. This "loader-ransomware-banker trifecta has wreaked havoc" in recent years, says security firm Intel 471.

Threatpost
APRIL 14, 2020
New research found that almost half of companies had malware on their corporate-associated home networks - in comparison to malware being found on only 13 percent of corporate networks.

IT Governance
APRIL 15, 2020
As we enter the fourth week of the lockdown, you’ve hopefully begun to find a routine in your new work arrangement. Perhaps you’re able to get out of bed and shower before logging on instead of lying in bed until 8:55 am and crawling to your desk. Maybe you feel less guilty about having a mid-morning video chat with a colleague in lieu of your normal coffee break.
Let's personalize your content