Task Force Seeks to Disrupt Ransomware Payments
Krebs on Security
APRIL 29, 2021
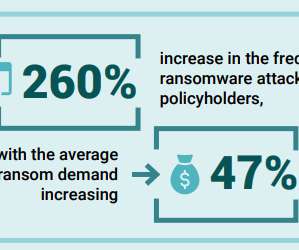
Some of the world’s top tech firms are backing a new industry task force focused on disrupting cybercriminal ransomware gangs by limiting their ability to get paid, and targeting the individuals and finances of the organized thieves behind these crimes. In a 50-page report delivered to the Biden administration this week, top executives from Amazon , Cisco , FireEye , McAfee , Microsoft and dozens of other firms joined the U.S.







































Let's personalize your content