List of Data Breaches and Cyber Attacks in March 2021 – 21 Million Records Breached
IT Governance
APRIL 1, 2021
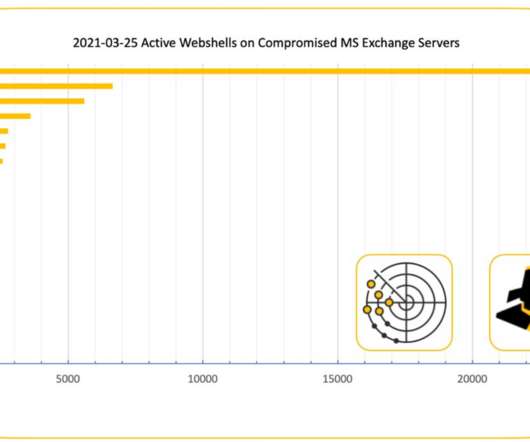
Don’t be fooled by the fact that we only recorded 20,995,371 breached records in March; it was one of the leakiest months we’ve ever seen, with 151 recorded incidents. By comparison, there was a seemingly Lilliputian 82 recorded breaches in January and 118 in February.









































Let's personalize your content