Senate SolarWinds Hearing: 4 Key Issues Raised
Data Breach Today
FEBRUARY 24, 2021
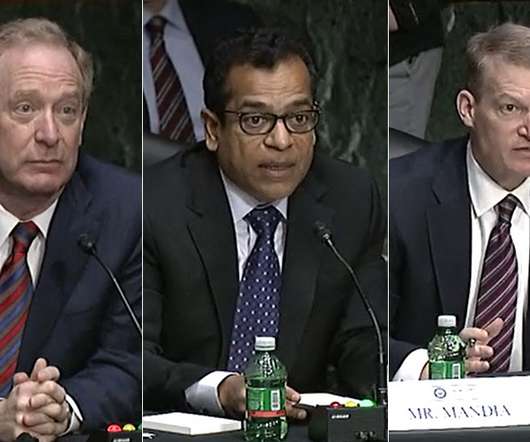
Issues Include Attackers' Use of Amazon's Infrastructure The Senate Intelligence Committee's hearing about the supply chain attack that affected SolarWinds and dozens of other companies and federal agencies answered some questions about what went wrong but also raised four key issues.



































Let's personalize your content