Work-at-Home: The Impact on Security
Data Breach Today
MAY 1, 2020
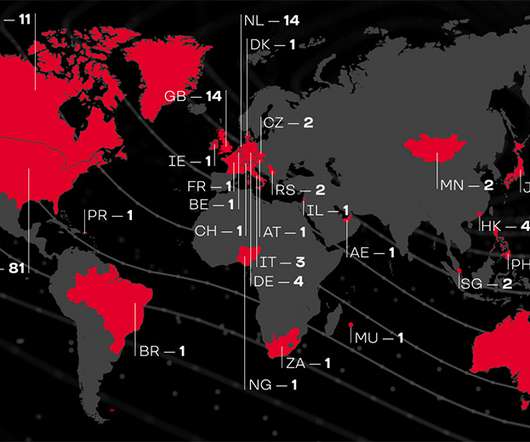
Survey Sizes Up Increased Risks, New Duties for Security Staff The shift to working at home is opening the door to cybersecurity incidents. Some 23% of respondents to a small survey conducted by the training organization (ISC)2 say their organization has experienced an increase in cybersecurity incidents since transitioning to remote work.































Let's personalize your content