What is Federated Information Management?
Gimmal
MARCH 19, 2020
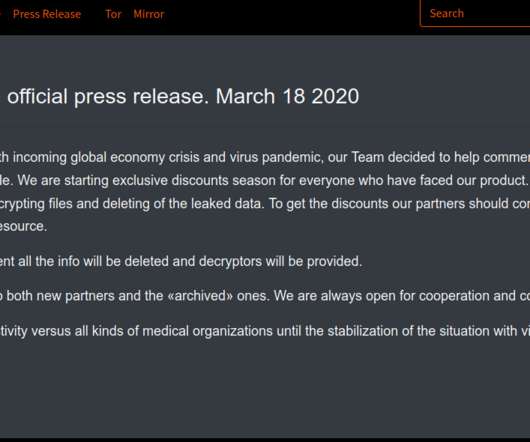
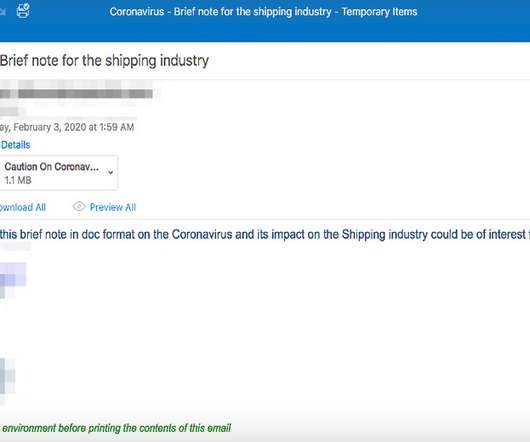
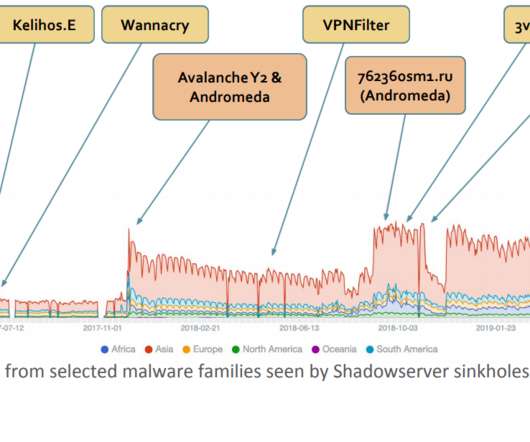
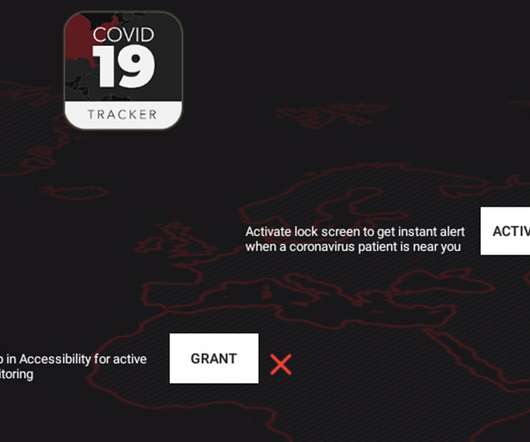
Almost every industry is facing a similar challenge today: How to implement an overarching information governance strategy that covers all information in a unified manner. As a leader in records and information management, Gimmal has solved this exact problem for our clients. This article will delve into the concept of federated information management and the challenges and obstacles faced by all organizations.

































Let's personalize your content