COVID-19 ‘Breach Bubble’ Waiting to Pop?
Krebs on Security
JUNE 30, 2020
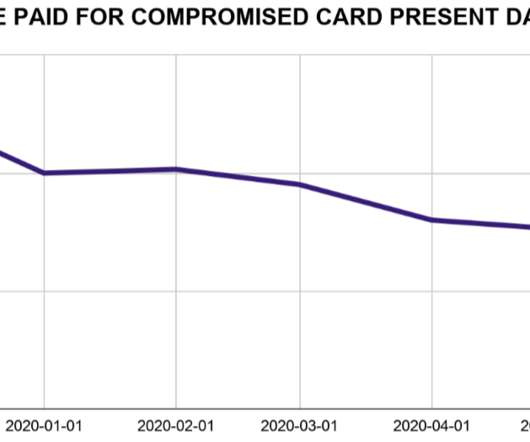
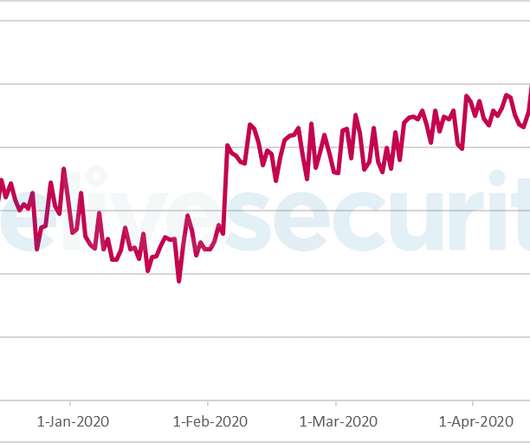
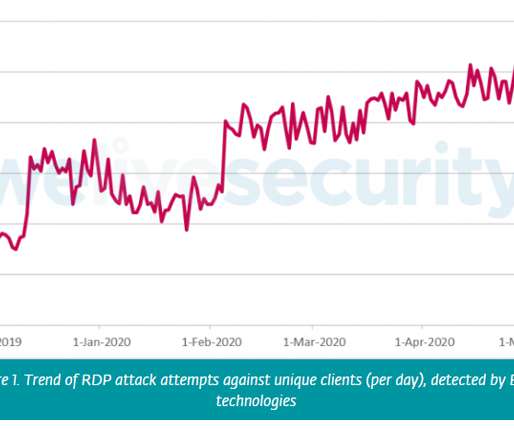
The COVID-19 pandemic has made it harder for banks to trace the source of payment card data stolen from smaller, hacked online merchants. On the plus side, months of quarantine have massively decreased demand for account information that thieves buy and use to create physical counterfeit credit cards. But fraud experts say recent developments suggest both trends are about to change — and likely for the worse.


































Let's personalize your content