Eliminate the Password, Eliminate the Password Problem.
The Security Ledger
JANUARY 9, 2020
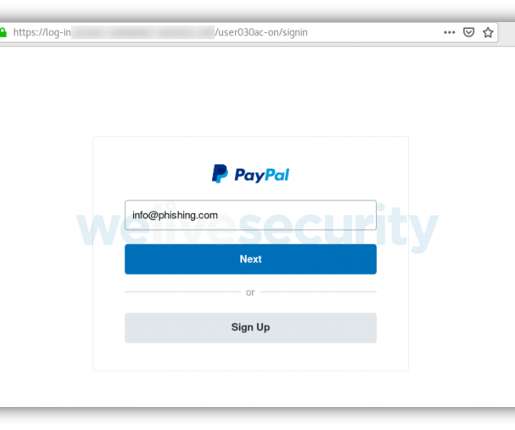
Weak, stolen or reused passwords are the root of 8 in 10 data breaches. Fixing the data breach problem means abandoning passwords for something more secure. But what does passwordless authentication even look like? Yaser Masoudnia, the Senior Director Product Management, Identity Access Management, at LogMeIn* takes us there. The post Eliminate. Read the whole entry. » Related Stories Explained: Two-Factor vs.





































Let's personalize your content