How AI Will Supercharge Spear-Phishing
Dark Reading
OCTOBER 21, 2020
To keep pace with intelligent, unpredictable threats, cybersecurity will have to adopt an intelligent security of its own.
Dark Reading
OCTOBER 21, 2020
To keep pace with intelligent, unpredictable threats, cybersecurity will have to adopt an intelligent security of its own.
Data Breach Today
OCTOBER 20, 2020
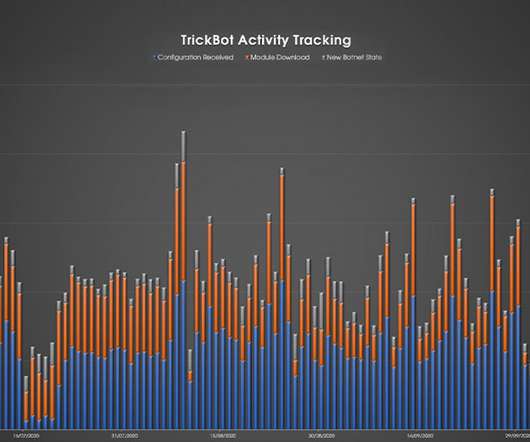
CrowdStrike: Botnet's Activity Has Already Picked Up The recent "takedown" of Trickbot by Microsoft and others had only a temporary effect; the botnet's activity levels have already rebounded, according to Crowdstrike and other security firms.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
OCTOBER 22, 2020
In an interview with WIRED, Facebook's chief privacy officers argue that the company has turned a corner. Again.
Krebs on Security
OCTOBER 22, 2020
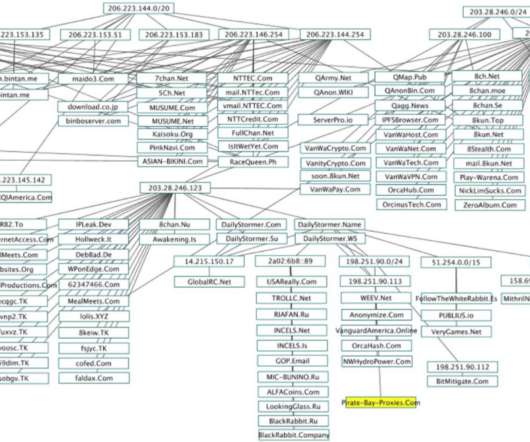
Some of the world’s largest Internet firms have taken steps to crack down on disinformation spread by QAnon conspiracy theorists and the hate-filled anonymous message board 8chan. But according to a California-based security researcher, those seeking to de-platform these communities may have overlooked a simple legal solution to that end: Both the Nevada-based web hosting company owned by 8chan’s current figurehead and the California firm that provides its sole connection to the Inte

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

The Last Watchdog
OCTOBER 19, 2020
There is no shortage of innovative cybersecurity tools and services that can help companies do a much better job of defending their networks. Related: Welcome to the CyberXchange Marketplace In the U.S. alone, in fact, there are more than 5,000 cybersecurity vendors. For organizations looking to improve their security posture, this is causing confusion and vendor fatigue, especially for companies that don’t have a full time Chief Information Security Officer.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
OCTOBER 21, 2020
In this episode of AIIM On Air , I speak with Sue Trombley, Managing Director of Thought Leadership for Iron Mountain. We discuss the biggest impacts on the workplace from Covid-19 and the challenges and opportunities of the new normal of business today. While remote work is a new reality for many organizations and workers, not all people and positions can work from home.

erwin
OCTOBER 22, 2020
Thoughts on erwin Insights Day No. 2 Keynote. If you didn’t watch New York Times Best-Selling Author Keith Ferrazzi’s keynote from erwin Insights 2020 , what are you waiting for? I was blown away by Keith’s perspective on “Leading Without Authority” and it got me thinking about my own career, our employees here at erwin, work as we knew it, and work as we’ll know it in a post-COVID world.
Security Affairs
OCTOBER 17, 2020
On Thursday, four JavaScript packages have been removed from the npm portal because they have been found containing malicious code. NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language. The four packages, which had a total of one thousand of downloads, are: plutov-slack-client nodetest199 nodetest1010 npmpubman . “Any computer that has this package installed or running sh

Data Breach Today
OCTOBER 20, 2020
DOJ: Russian GRU Officers Targeted 2018 Olympics, French Elections and More The U.S. Justice Department unsealed indictments against six Russian military officers on Monday, alleging that they carried out a series of major hacking operations, including deploying destructive NotPetya malware - tied to more than $10 billion in damages - and attacking the 2018 Olympics.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

AIIM
OCTOBER 22, 2020
As you already know, people are more likely to follow your rules after they buy in to the reasons behind them. But you can take it one step further, and provide your “rules” as solutions instead of orders. Amazon’s Kindle publishing team understands this concept well. I was preparing the Kindle edition of my recent book , following the production of the softcover edition.

National Archives Records Express
OCTOBER 19, 2020
This post is written by Sharmila Bhatia and Markus Most. We are pleased to announce the release of a white paper on the records management implications of: Internet of Things (IoT) Robotic Process Automation (RPA) Machine Learning (ML) Artificial Intelligence (AI). This white paper provides a basic description of each of these technologies, examples of their various applications, and enabling factors supporting the technologies.
Security Affairs
OCTOBER 20, 2020
The Nefilim ransomware operators have posted a long list of files that appear to belong to Italian eyewear and eyecare giant Luxottica. Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com.

Data Breach Today
OCTOBER 21, 2020
Researchers Find Pfizer Drug Customer Messages Accessible on Internet For the second time within a week, it's been revealed that sensitive voice messages containing patients' information have been exposed on the internet. The latest discovery involves unsecured voice transcripts of patient calls to drug giant Pfizer's automated customer support system.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

AIIM
OCTOBER 20, 2020
Before we start, let’s take a minute to address the big elephant in the room. You’re probably thinking, “ Where are you going with this sales angle, Sean? I work with records and information, and my job is all about managing, protecting, and storing it. I don’t sell a thing! ”. Well, what we’re going to cover today will show you that you ARE, in fact, in the business of selling when it comes to Information Governance – it’s just a slightly different model than we’re all used to.

The Guardian Data Protection
OCTOBER 17, 2020
Fears move may deter people from getting tested for Covid-19 if forces get data Coronavirus – latest updates See all our coronavirus coverage People who have been told to self-isolate through NHS test and trace could have their contact details passed to police, a move some fear could deter people from being tested for coronavirus. Police forces will be able to access information about people “on a case-by-case” basis, so they can learn whether an individual has been told to self-isolate, the Dep

Security Affairs
OCTOBER 19, 2020
Researchers from the Ben-Gurion University of the Negev demonstrated how to fool self-driving cars by displaying virtual objects. A group of researchers from the Ben-Gurion University of the Negev demonstrated that it is possible to fool self-driving cars by displaying virtual objects (phantoms). The experts define as phantom a depthless visual object used to deceive ADASs and cause these systems to perceive it as real.

Data Breach Today
OCTOBER 21, 2020
Indictments Are Just a First Step Toward a Crackdown The U.S. indictment charging that six Russian GRU military intelligence officers were responsible for numerous cyberattacks highlights Moscow's seemingly unending appetite for online destruction. Experts say more than indictments will be required to curb such activity.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.
Threatpost
OCTOBER 23, 2020
Dr. Reddy's, the contractor for Russia’s “Sputinik V” COVID-19 vaccine and a major generics producer, has had to close plants and isolate its data centers.
Dark Reading
OCTOBER 19, 2020
The most widely used content management system on the Web relies heavily on plug-ins and add-on software -- and that requires rigorous security measures at every level.
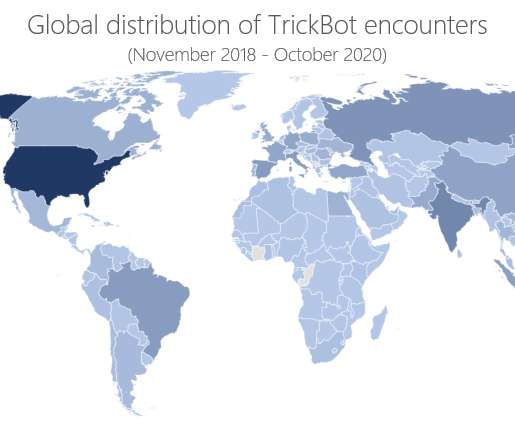
Security Affairs
OCTOBER 21, 2020
Microsoft brought down TrickBot infrastructure last week, but a few days later the botmasters set up a new command and control (C&C) servers. Microsoft’s Defender team, FS-ISAC , ESET , Lumen’s Black Lotus Labs , NTT , and Broadcom’s cyber-security division Symantec joined the forces and announced last week a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.

Data Breach Today
OCTOBER 19, 2020
DOJ: Russian GRU Officers Targeted 2018 Olympics, French Elections and More The U.S. Justice Department unsealed indictments against six Russian military officers on Monday, alleging that they carried out a series of major hacking operations, including deploying NotPetya ransomware - causing over $10 billion in damages - and attacking the 2018 Olympics.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Threatpost
OCTOBER 22, 2020
Up to 50,000 Office 365 users are being targeted by a phishing campaign that purports to notify them of a "missed chat" from Microsoft Teams.

Dark Reading
OCTOBER 21, 2020
One cybersecurity failure can result in a successful ransomware attack or data breach that could cause tremendous damage. There's no need to panic, but neither is there time to ignore the issue.

Security Affairs
OCTOBER 18, 2020
The financially-motivated hacker group FIN11 has started spreading ransomware to monetize its cyber criminal activities. The financially-motivated hacker group FIN11 has switched tactics starting using ransomware as the main monetization method. The group carried out multiple high-volume operations targeting companies across the world, most of them in North America and Europe.

Data Breach Today
OCTOBER 22, 2020
US Indictment Airs Russian Military's Dirty Laundry Although Russia's elite nation-state hackers are capable of waging destructive attacks, the GRU military intelligence Sandworm operators have not been able to remain in the shadows, a U.S.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Threatpost
OCTOBER 21, 2020
The majority of the bugs in Cisco’s Firepower Threat Defense (FTD) and Adaptive Security Appliance (ASA) software can enable denial of service (DoS) on affected devices.

WIRED Threat Level
OCTOBER 19, 2020
The Department of Justice has named and charged six men for allegedly carrying out many of the most costly cyberattacks in history.

Security Affairs
OCTOBER 19, 2020
A hacker collective claims to have hacked over 50,000 home security cameras and published their footage online, some of them on adult sites. A group of hackers claims to have compromised over 50,000 home security cameras and published their private footage online. Some footages were published on adult sites, experts reported that crooks are offering lifetime access to the entire collection for US$150.
Let's personalize your content