Microsoft's Making a Secure PC Chip—With Intel and AMD's Help
WIRED Threat Level
NOVEMBER 17, 2020
The Pluton security processor will give the software giant an even more prominent role in locking down Windows hardware.

WIRED Threat Level
NOVEMBER 17, 2020
The Pluton security processor will give the software giant an even more prominent role in locking down Windows hardware.
Dark Reading
NOVEMBER 17, 2020
AI threat find: Phishing attack slips through email gateway and leads to large-scale compromise.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Data Breach Today
NOVEMBER 18, 2020
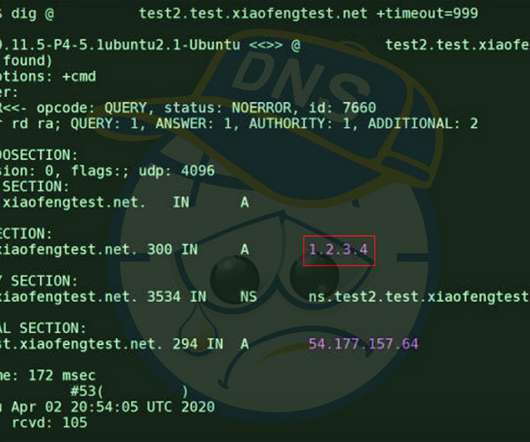
Fixes Arriving to Safeguard DNS Against Newly Found 'SAD DNS' Side-Channel Attack Researchers are warning that many domain name system server implementations are vulnerable to a spoofing attack that allows attackers to redirect, intercept and manipulate traffic. Thankfully, fixes are already arriving for this so-called SAD DNS flaw.

Krebs on Security
NOVEMBER 17, 2020
An increasing number of websites are asking visitors to approve “notifications,” browser modifications that periodically display messages on the user’s mobile or desktop device. In many cases these notifications are benign, but several dodgy firms are paying site owners to install their notification scripts and then selling that communications pathway to scammers and online hucksters.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

AIIM
NOVEMBER 19, 2020
Change is hard, but not impossible. Understanding how change works, considering how people will react to change , and planning a thoughtful roll-out are all ways to ease the burden of change. It’s a practice called Change Management , and for organizational change, it can be your key to success. It’s also important to recognize that not every change situation can be managed in the same way.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
NOVEMBER 14, 2020
Misconfigured Database Might Have Led to Data Breach, Security Experts Say An unauthorized person appears to have gained entry to insurance software firm Vertafore and compromised the driver's license information of over 27 million Texas citizens. Security analysts are leaning toward a misconfigured database as the culprit.
Krebs on Security
NOVEMBER 20, 2020
A 21-year-old Irishman who pleaded guilty to charges of helping to steal millions of dollars in cryptocurrencies from victims has been sentenced to just under three years in prison. The defendant is part of an alleged conspiracy involving at least eight others in the United States who stand accused of theft via SIM swapping , a crime that involves convincing mobile phone company employees to transfer ownership of the target’s phone number to a device the attackers control.

AIIM
NOVEMBER 17, 2020
How Do I Know I Need Change Management? The funny thing about Change Management is that it’s one of those things that you probably don’t know exists until you need it. Yes, I know that’s an odd thing to say, but hear me out on this. With change management, here’s a very common scenario leading to awareness. First, something new happens at your organization.
Security Affairs
NOVEMBER 19, 2020
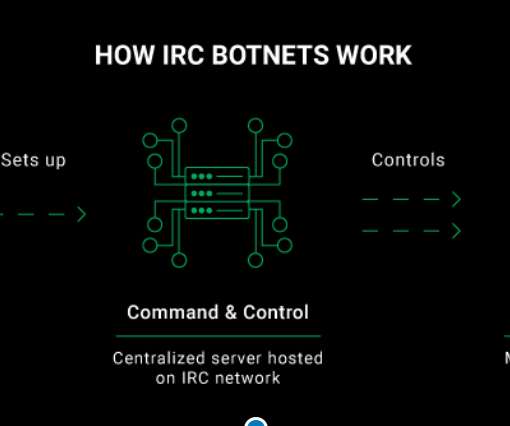
The CyberNews.com Investigation team carried out an infiltration operation against an IRC botnet and reported it to CERT Vietnam to help take it down. Original post @ [link]. In order to gather valuable information about the IRC botnet’s activity, we joined its Command and Control channel where we met the botmaster who was responsible for running the entire network of compromised systems.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Data Breach Today
NOVEMBER 16, 2020
Following Alerts of Potential Fraud, Ticketmaster Took 9 Weeks to Spot Big Breach Ticketmaster UK has been fined $1.7 million by Britain's privacy watchdog for its "serious failure" to comply with the EU's General Data Protection Regulation. Its failure to properly secure chatbot software led to attackers stealing at least 9.4 million payment card details.

Schneier on Security
NOVEMBER 16, 2020
Blockchain voting is a spectacularly dumb idea for a whole bunch of reasons. I have generally quoted Matt Blaze : Why is blockchain voting a dumb idea? Glad you asked. For starters: It doesn’t solve any problems civil elections actually have. It’s basically incompatible with “software independence”, considered an essential property.

Hunton Privacy
NOVEMBER 19, 2020
On November 18, 2020, the Centre for Information Policy Leadership (“CIPL”) at Hunton Andrews Kurth submitted its response to the Standing Committee of the National People’s Congress (“NPC”) of the People’s Republic of China on the Draft Personal Information Protection Law (“PIPL”). In its response, CIPL highlights several possible modifications of the PIPL, which it believes the NPC should consider and adopt during its review, not only to ensure China’s standing in the international data protec

Security Affairs
NOVEMBER 15, 2020
Chilean-based retail giant Cencosud has suffered a ransomware attack that impacted operations at its stores, Egregor ransomware appears to be involved. A ransomware attack, allegedly launched by the Egregor ransomware gang, hit the Chilean-based retail giant Cencosud, the incident impacted operations at its stores. Cencosud the largest retail company in Chile and the third largest listed retail company in Latin America, competing with the Brazilian Companhia Brasileira de Distribuição and the Me

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Breach Today
NOVEMBER 18, 2020
Capcom Says Over 350,000 Customer, Business Records Possibly Compromised Japanese computer game company Capcom acknowledged this week that a November security incident was a Ragnar Locker ransomware attack that resulted in about 350,000 customer and company records potentially compromised, including sales and shareholder data.

Data Protection Report
NOVEMBER 20, 2020
On November 17, 2020, the Minister of Innovation, Science and Industry, Navdeep Bains, tabled proposed legislation in Parliament that aims to overhaul Canada’s data privacy law. Bill C-11, entitled An Act to enact the Consumer Privacy Protection Act and the Personal Information and Data Protection Tribunal Act and to make consequential and related amendments to other Act , will create new data privacy obligations and new enforcement mechanisms for these obligations if it becomes law.

Threatpost
NOVEMBER 19, 2020
Researchers have unveiled an attack that allows attackers to eavesdrop on homeowners inside their homes, through the LiDAR sensors on their robot vacuums.

Security Affairs
NOVEMBER 20, 2020
Authorities in India believe that a major power outage that occurred in October in Mumbai may have been caused by hackers. On October 13, a major power outage occurred in the metropolitan area of Mumbai causing the partial disruption of the traffic management systems and the paralysis of the rail traffic and also impacted work at the stock exchange.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Data Breach Today
NOVEMBER 18, 2020
Learning From Difficult Recoveries and Advice in Government Alerts As ransomware attacks on the healthcare sector continue to surge, entities should heed the lessons emerging from these incidents as well as the advice provided in alerts from government agencies, security experts say.

Micro Focus
NOVEMBER 18, 2020
How Kmart modernized using AWS and Micro Focus Introduction A recent Forbes article commented, “COVID-19 will be remembered for many things and what’s becoming indisputable is how it is rapidly transforming business”. A probably less well-known impact is the additional complexity of the pandemic on large scale IT projects. For major change programs, IT teams.
Threatpost
NOVEMBER 16, 2020
Bumble fumble: An API bug exposed personal information of users like political leanings, astrological signs, education, and even height and weight, and their distance away in miles.
Security Affairs
NOVEMBER 18, 2020
Microsoft is tracking an ongoing Office 365 phishing campaign aimed at enterprises that is able to detect sandbox solutions and evade detection. Microsoft is tracking an ongoing Office 365 phishing campaign that is targeting enterprises, the attacks are able to detect sandbox solutions and evade detection. “We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” reads a message pub

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Data Breach Today
NOVEMBER 20, 2020
Threats Include Social Engineering, Insider Trading, Face-Seeking Assassin Drones "Has anyone witnessed any examples of criminals abusing artificial intelligence?" That's a question security firms have been raising.

WIRED Threat Level
NOVEMBER 18, 2020
A deepfake bot has been generating explicit, non-consensual images on the platform. The researchers who found it say their warnings have been ignored.

Schneier on Security
NOVEMBER 20, 2020
Symantec is reporting on an APT group linked to China, named Cicada. They have been attacking organizations in Japan and elsewhere. Cicada has historically been known to target Japan-linked organizations, and has also targeted MSPs in the past. The group is using living-off-the-land tools as well as custom malware in this attack campaign, including a custom malware — Backdoor.Hartip — that Symantec has not seen being used by the group before.

Threatpost
NOVEMBER 19, 2020
Threat actors mount year-long campaign of espionage, exfiltrating data, stealing credentials and installing backdoors on victims’ networks.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
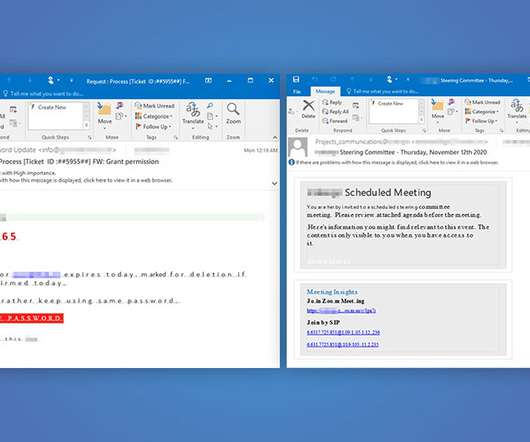
Data Breach Today
NOVEMBER 18, 2020
Fraudsters Using Evasive Techniques to Bypass Secure Email Gateways Microsoft's Security Intelligence team is warning users of the Office 365 suite about an ongoing phishing campaign that appears to be harvesting victims' credentials. The emails use several techniques to bypass and evade secure email gateways.

Security Affairs
NOVEMBER 20, 2020
Facebook has addressed a security vulnerability in its Messenger for Android app that could have allowed attackers to spy on users. Facebook has addressed a major security issue in its Messenger for Android app that could have allowed threat actors to spy on users by placing and connecting Messenger audio calls without their interaction. The vulnerability was discovered by white-hat hacker Natalie Silvanovich, from Google’s Project Zero team.

IT Governance
NOVEMBER 18, 2020
When the European Court of Justice invalidated the EU–US Privacy Shield earlier this year, organisations were left unsure about how to legally transfer personal data into and out of the EU. The ruling was made following criticism from the Austrian privacy activist Max Schrems, who argued that the US government’s mass surveillance practices contradicted the protections that the Privacy Shield was supposed to provide.
Let's personalize your content