COVID-19: The Digital Exposure Crisis
Data Breach Today
MARCH 27, 2020
Cybersecurity Specialist John Walker on Lack of Preparedness, Bad Cyber Practices in UK The COVID-19 pandemic has exposed more than policy and social gaps, says U.K.-based cybersecurity expert John Walker. It's also manifested in digital exposures born out of lack of preparedness and bad practices. Walker offers insights on improving the cyber response.


















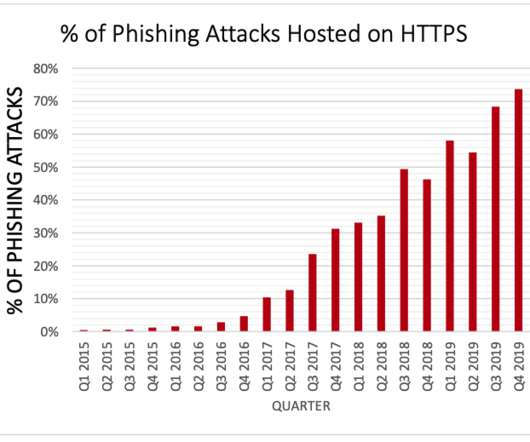

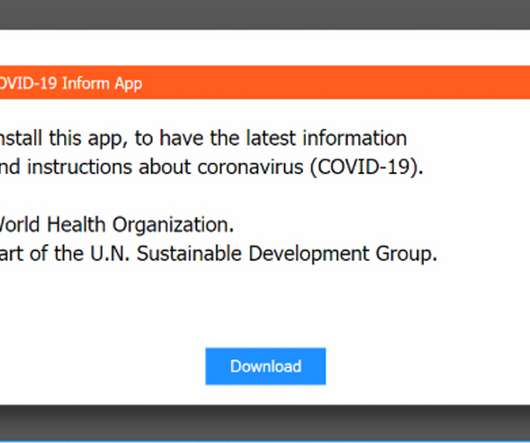


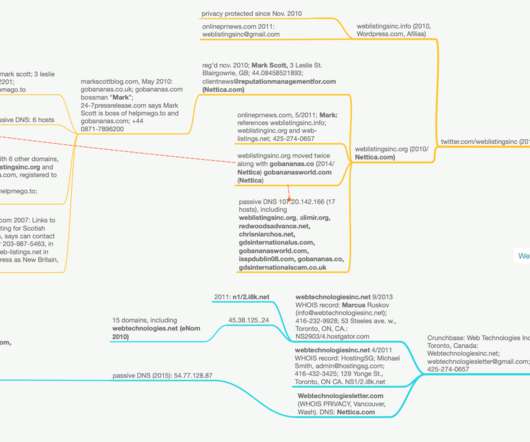
















Let's personalize your content